Workflow Secure Infrastructure Blog

New Workflow Encrypted Pdf Economies Government Finances Rod trent may 6, 2021january 28, 2024 publishedmay 6, 2021january 28, 2024 previous post workflow. Workflow automation in security and compliance can improve speed, accuracy, and consistency within your business's compliance processes. by automating workflows, you reduce the manual effort required for routine tasks, freeing your team to focus on more strategic and value added activities.

Workflow Secure Infrastructure Blog Here, we focus on embedding security directly into devops workflows using microsoft defender for cloud’s cloud security posture management (cspm) capabilities. Establishing secure workflows and infrastructure guardrails is just the beginning of the larger cloud security journey. after setting up secure and compliant infrastructure, the next step is to establish zero trust security best practices across your organization. Welcome to part 4, the final stage of the golden workflow strategy. you’ve completed both the crawl and walk phases — standardizing builds, introducing an image registry, and establishing. This article explains how telecom and infrastructure providers can improve security by automating workflows to detect config errors, enforce zero trust segmentation, and accelerate incident response using ai.

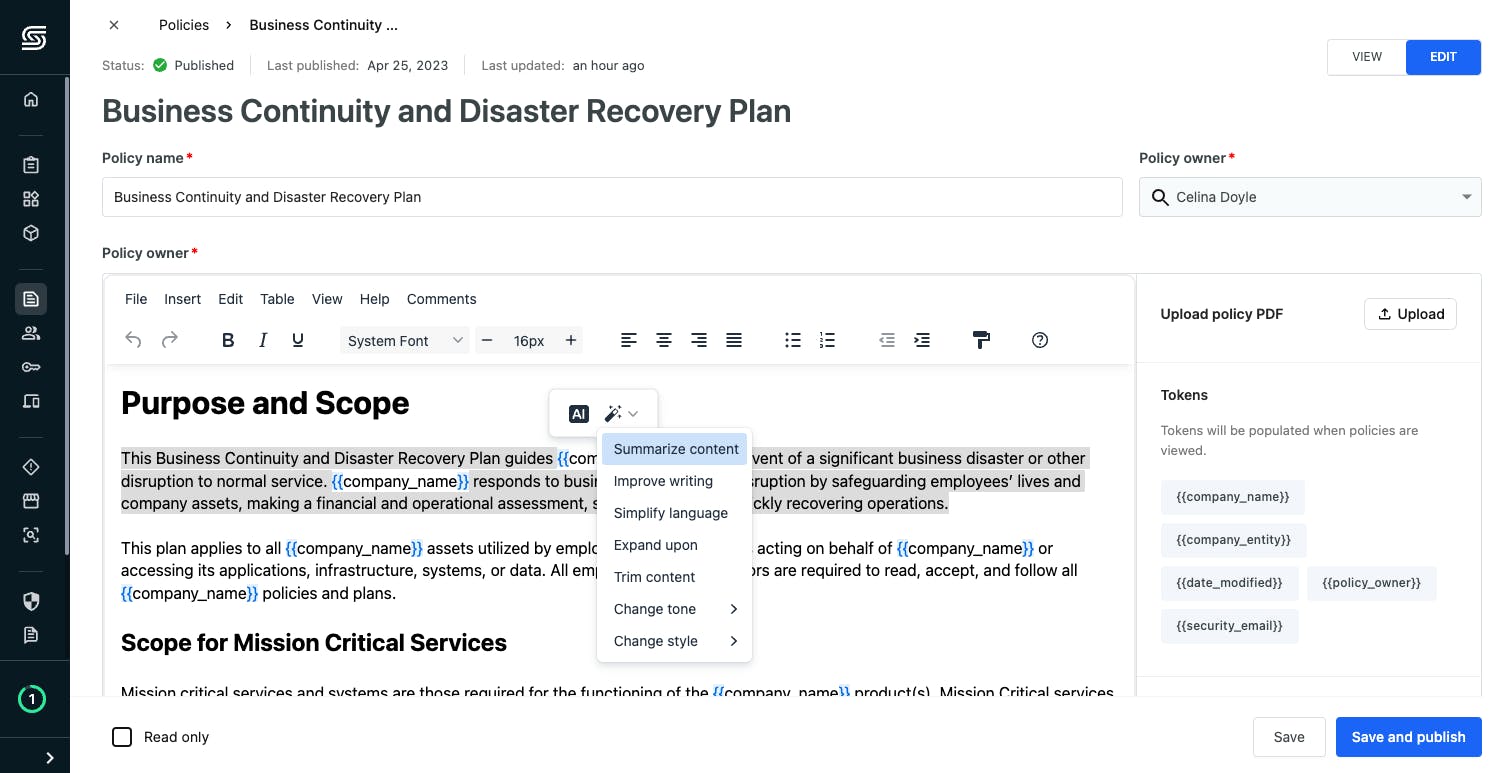
8 Automated Security Workflows That Reduce Costs And Complexity Welcome to part 4, the final stage of the golden workflow strategy. you’ve completed both the crawl and walk phases — standardizing builds, introducing an image registry, and establishing. This article explains how telecom and infrastructure providers can improve security by automating workflows to detect config errors, enforce zero trust segmentation, and accelerate incident response using ai. Secure workload 3.8 brings a wealth of new capabilities to help security professionals protect critical application workloads. We’ve fine tuned our vision for a smart and secure workflow platform that caters to all enterprise teams. with the introduction of innovative features like api creation, apps, cases, records, and dynamic integrations, we are closer than ever to realizing that vision. For businesses looking to simplify processes while tightening security, lcnc platforms offer a practical and accessible solution. let’s look into how these platforms are transforming cybersecurity, making it easier to automate key security tasks and keep your organization safe from potential threats. Explore cloud security automation best practices, effective strategies, and the benefits of automating security for improved efficiency and risk management.
8 Automated Security Workflows That Reduce Costs And Complexity Secure workload 3.8 brings a wealth of new capabilities to help security professionals protect critical application workloads. We’ve fine tuned our vision for a smart and secure workflow platform that caters to all enterprise teams. with the introduction of innovative features like api creation, apps, cases, records, and dynamic integrations, we are closer than ever to realizing that vision. For businesses looking to simplify processes while tightening security, lcnc platforms offer a practical and accessible solution. let’s look into how these platforms are transforming cybersecurity, making it easier to automate key security tasks and keep your organization safe from potential threats. Explore cloud security automation best practices, effective strategies, and the benefits of automating security for improved efficiency and risk management.
8 Automated Security Workflows That Reduce Costs And Complexity For businesses looking to simplify processes while tightening security, lcnc platforms offer a practical and accessible solution. let’s look into how these platforms are transforming cybersecurity, making it easier to automate key security tasks and keep your organization safe from potential threats. Explore cloud security automation best practices, effective strategies, and the benefits of automating security for improved efficiency and risk management.
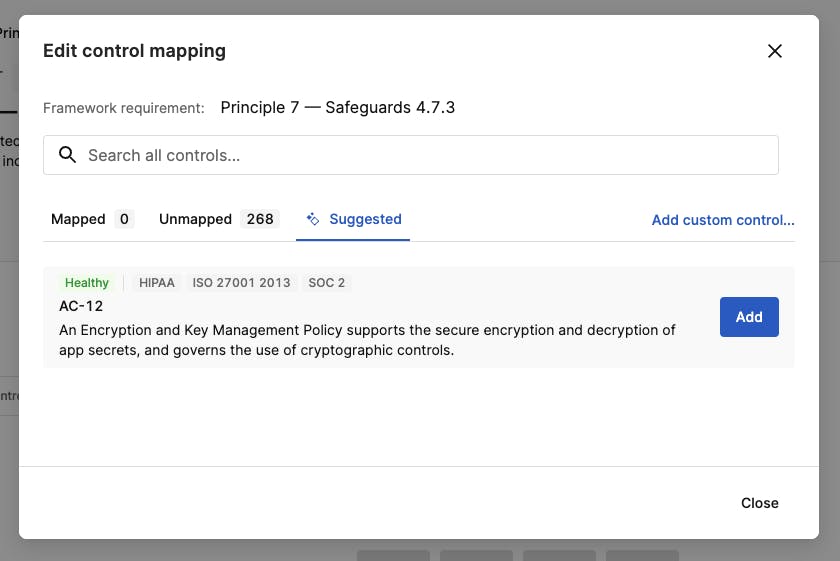
8 Automated Security Workflows That Reduce Costs And Complexity
Comments are closed.