What Is Public Key Cryptography Twilio
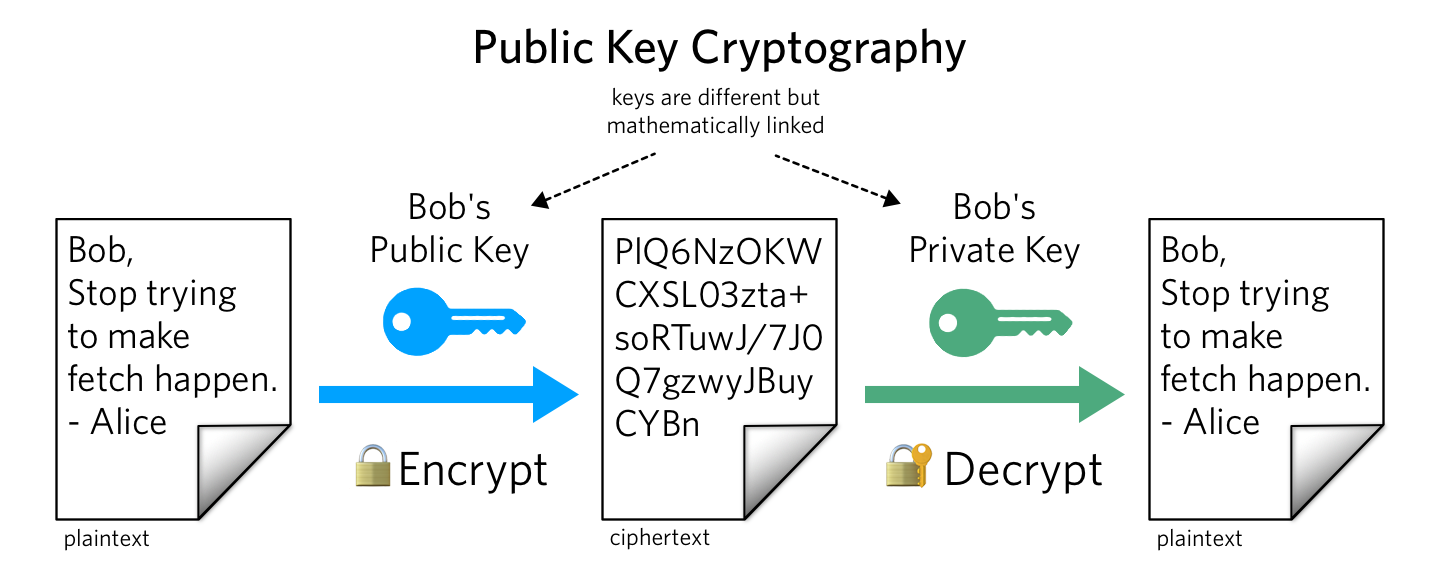
What Is Public Key Cryptography This post will dive into public key cryptography, also known as asymmetric cryptography, an overview of how it works, and its everyday use cases — including how twilio uses public key crypto in our verify api and to secure our api. Asymmetric encryption, also known as public key cryptography, is a type of encryption that uses a pair of keys for secure communication a public key and a private key. the private key is owned by the issuer and is used to compute the signature.
What Is Public Key Cryptography Twilio Learn how to implement public key client validation with twilio. includes sample curl commands, http requests, and a java example. Public key client validation helps organizations in compliance heavy industries meet strict security requirements. learn how to get started in this overview. Other than verifying that the public key belongs to the legitimate recipient (see certificate authorities, below), no secure key exchange is required. however, generating and using the public key is slow because the key needs to be very large to support this scheme. This new feature enhances security by allowing you to validate requests from twilio, ensuring data integrity and authenticity. with public key client validation, you can now have greater confidence in the interactions between your application and twilio.
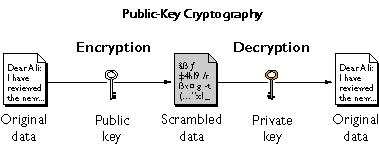
Public Key Cryptography Network Encyclopedia Other than verifying that the public key belongs to the legitimate recipient (see certificate authorities, below), no secure key exchange is required. however, generating and using the public key is slow because the key needs to be very large to support this scheme. This new feature enhances security by allowing you to validate requests from twilio, ensuring data integrity and authenticity. with public key client validation, you can now have greater confidence in the interactions between your application and twilio. Public key cryptography, also known as asymmetric encryption, is a method of securing digital communication using a pair of keys: a public key and a private key. Public key cryptography, also known as asymmetric cryptography, is a fundamental concept in modern cybersecurity. it uses a pair of keys—a public key and a private key—to encrypt and decrypt data, ensuring secure communication and authentication in digital environments. Public key cryptography functions as an asymmetric cryptographic system that works between public keys and private keys during the process of data encryption and decryption. public key – shared openly and used for encryption of data. private key – kept secret and used for decryption of data. This post will dive into public key cryptography, also known as asymmetric cryptography, an overview of how it works, and its everyday use cases — including how twilio uses public key crypto in our verify api and to secure our api. let's start with some context and history.

Public Key Cryptography Deepstash Public key cryptography, also known as asymmetric encryption, is a method of securing digital communication using a pair of keys: a public key and a private key. Public key cryptography, also known as asymmetric cryptography, is a fundamental concept in modern cybersecurity. it uses a pair of keys—a public key and a private key—to encrypt and decrypt data, ensuring secure communication and authentication in digital environments. Public key cryptography functions as an asymmetric cryptographic system that works between public keys and private keys during the process of data encryption and decryption. public key – shared openly and used for encryption of data. private key – kept secret and used for decryption of data. This post will dive into public key cryptography, also known as asymmetric cryptography, an overview of how it works, and its everyday use cases — including how twilio uses public key crypto in our verify api and to secure our api. let's start with some context and history.
Comments are closed.