What Is Hashing What Is Hashing With Example Hashing Explained Simply Simplilearn

Ppt What Is Hashing What Is Hashing With Example Hashing 8x higher interaction in live online classes conducted by industry experts simplilearn's jobassist helps you get noticed by top hiring companies. Hashing in cyber security is a one way process that transforms data into a fixed length string, known as a hash or digest, using cryptographic functions. it ensures data integrity and security, making password storage, digital signatures, and blockchain applications essential.

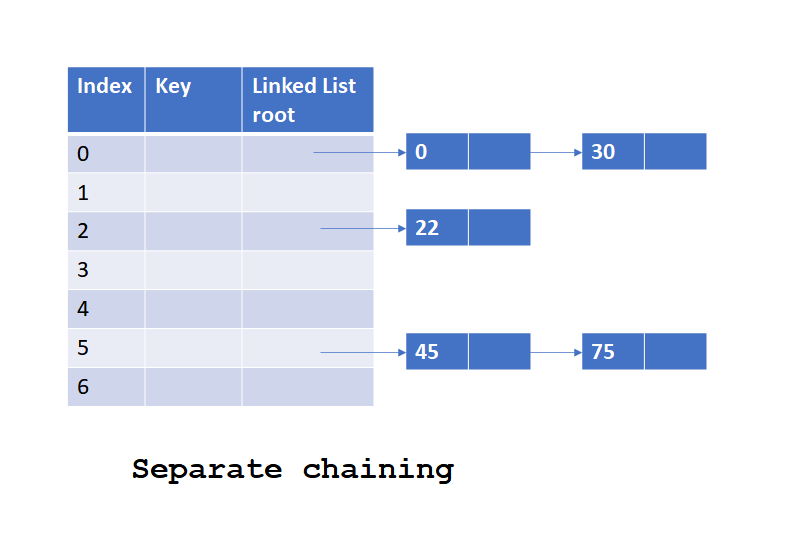
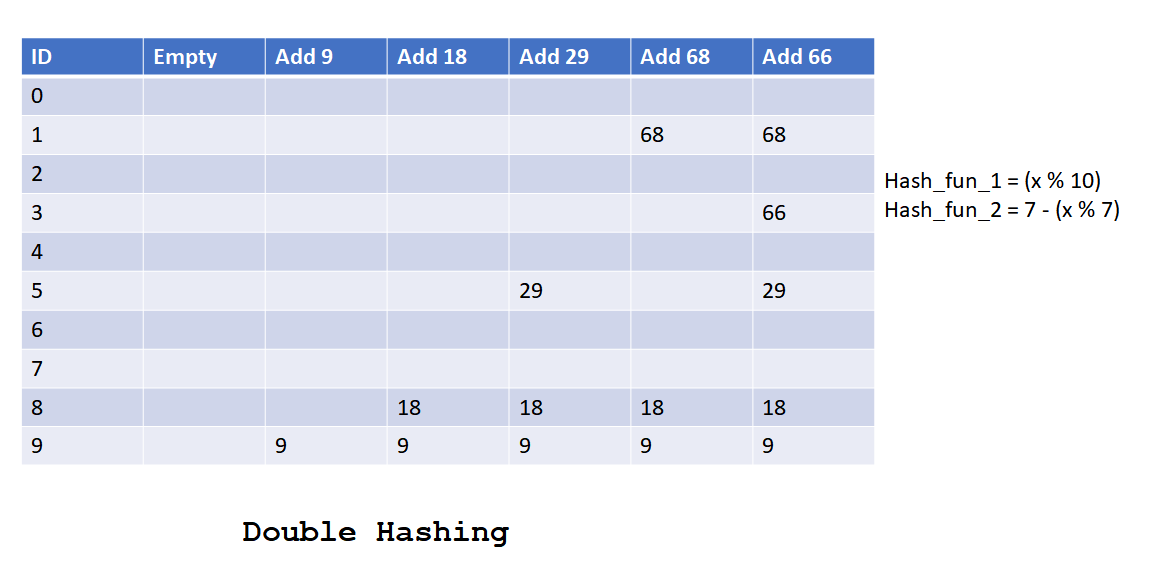
Ppt What Is Hashing What Is Hashing With Example Hashing In this presentation on what is hashing, we learn about what is hashing with an example, the different applications, advantages and ways to strengthen hashes. Hashing algorithms and security explained. | video: computerphile what is hashing used for? hashing is primarily used for security purposes — specifically cybersecurity. a hashed value has many uses, but it’s primarily meant to encode a plaintext value so the enclosed information can’t be exposed. the hashing process is non reversible or extremely difficult to decode, making it a popular. Hashing refers to the process of generating a fixed size output from an input of variable size using the mathematical formulas known as hash functions. this technique determines an index or location for the storage of an item in a data structure. Hashing uses hash functions to fill items in a hash table. to search, each key is passed into the same hash function which computes an index which provides the corresponding value location. let’s have a look at the ideal hash table. hashing method has following key constituents.

Ppt What Is Hashing What Is Hashing With Example Hashing Hashing refers to the process of generating a fixed size output from an input of variable size using the mathematical formulas known as hash functions. this technique determines an index or location for the storage of an item in a data structure. Hashing uses hash functions to fill items in a hash table. to search, each key is passed into the same hash function which computes an index which provides the corresponding value location. let’s have a look at the ideal hash table. hashing method has following key constituents. Hashing is the process of converting data of any size into a fixed size value using a mathematical function known as a hash function. in computer science, hashing is primarily used to determine the index or location for storing or retrieving an item quickly in a data structure. Hashing is the process of altering pieces of data or information into a fixed length that can't be recognized. as a cryptographic technique, users utilize it to protect data and improve security on messages that need to reach their destination safely.
Hashing Explained With Simple Example Simpletechtalks Hashing is the process of converting data of any size into a fixed size value using a mathematical function known as a hash function. in computer science, hashing is primarily used to determine the index or location for storing or retrieving an item quickly in a data structure. Hashing is the process of altering pieces of data or information into a fixed length that can't be recognized. as a cryptographic technique, users utilize it to protect data and improve security on messages that need to reach their destination safely.
Hashing Explained With Simple Example Simpletechtalks
Comments are closed.