What Is Hash Based Cryptography Next Lvl Programming
Github Virmanimudit8 Hash Based Cryptography We’ll guide you through the steps involved in implementing hash based cryptography in your projects, ensuring that your data remains secure and tamper proof. Now that we have a basic idea of what a hash function is in cryptography, let's break down the internal mechanics. the first act of the hashing algorithm is to divide the large input data into blocks of equal size. further, the algorithm applies the hashing process to the data blocks one by one.

An Analysis Of Common Hash Algorithms And Their Applications In Hash based cryptography is the generic term for constructions of cryptographic primitives based on the security of hash functions. it is of interest as a type of post quantum cryptography. Learn about the mechanisms and workings of hash based cryptography in this guide by entropiq. Definition: hash based cryptography was first developed by leslie lamport and ralph merkle in the late 1970s. hash based cryptography creates digital signature algorithms whose security is mathematically based on the security of a selected cryptographic hash function. Hash based cryptography is among the oldest area of quantum safe cryptography, with digital signature algorithms dating back to 1979, before the invention of elliptic curve cryptography.
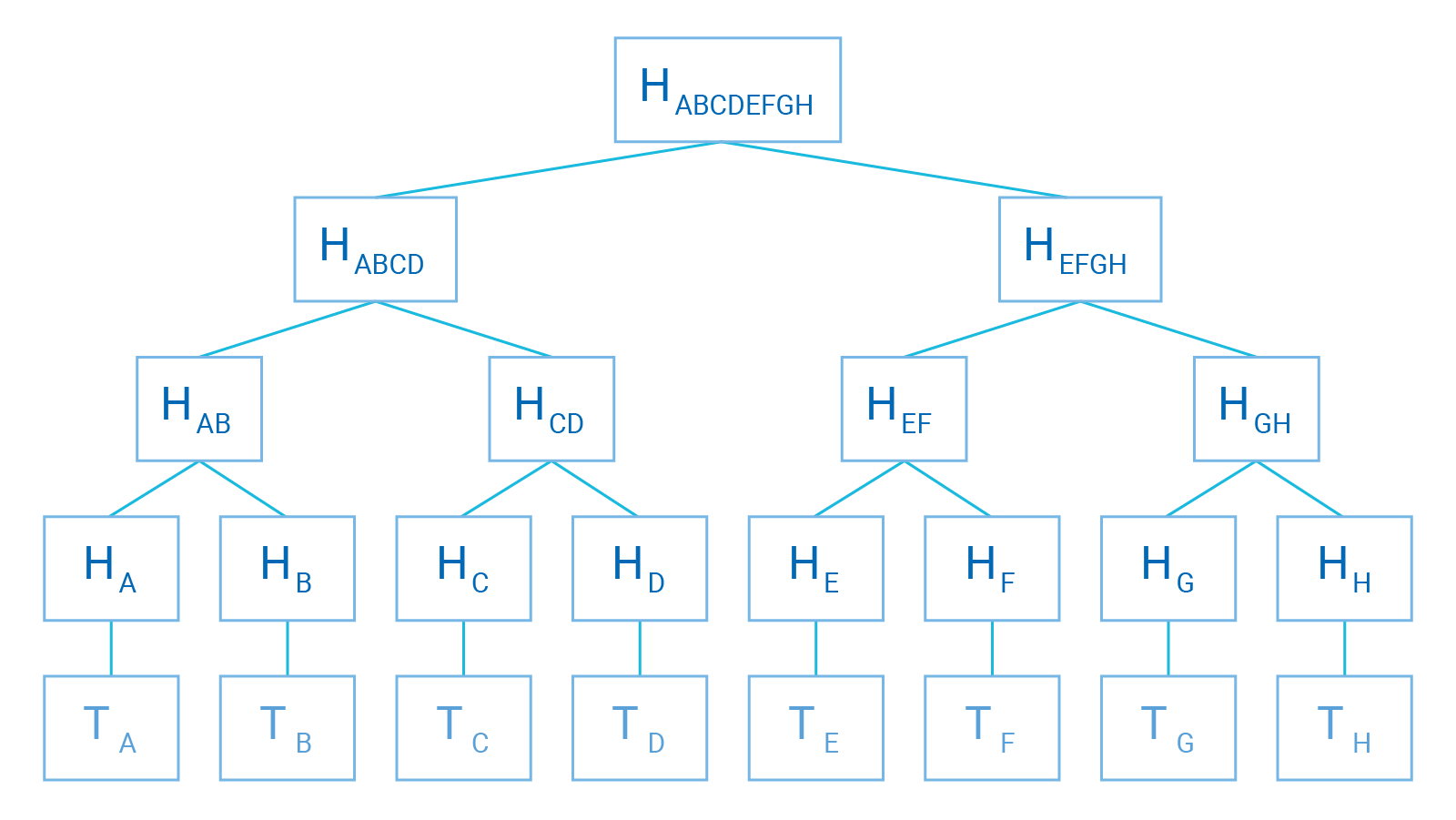
What Is Hash Based Cryptography Utimaco Definition: hash based cryptography was first developed by leslie lamport and ralph merkle in the late 1970s. hash based cryptography creates digital signature algorithms whose security is mathematically based on the security of a selected cryptographic hash function. Hash based cryptography is among the oldest area of quantum safe cryptography, with digital signature algorithms dating back to 1979, before the invention of elliptic curve cryptography. What is hash algorithm in cryptography? have you ever wondered how data is secured and validated in the digital realm? in this informative video, we’ll take. As stated above, hashing is the method of identifying an object from a group. each object gets a unique identification number once hashed. but, what does that mean technically? technically, a mathematical function generates a fixed length output from any input string of any length. What is a hash based cryptography? the security of quantum resistant cryptographic algorithms of this category is based on the properties of cryptographic hash functions. among such properties we can distinguish ― resistance to the search for a prototype, collisions, the second prototype. Cryptographic hash functions are intended to be fast, deterministic, and one way, meaning that even a minor change in input yields a very different hash. these functions are important for securing information digitally by allowing data verification and authentication.

1 883 Cryptography Hash Images Stock Photos Vectors Shutterstock What is hash algorithm in cryptography? have you ever wondered how data is secured and validated in the digital realm? in this informative video, we’ll take. As stated above, hashing is the method of identifying an object from a group. each object gets a unique identification number once hashed. but, what does that mean technically? technically, a mathematical function generates a fixed length output from any input string of any length. What is a hash based cryptography? the security of quantum resistant cryptographic algorithms of this category is based on the properties of cryptographic hash functions. among such properties we can distinguish ― resistance to the search for a prototype, collisions, the second prototype. Cryptographic hash functions are intended to be fast, deterministic, and one way, meaning that even a minor change in input yields a very different hash. these functions are important for securing information digitally by allowing data verification and authentication.
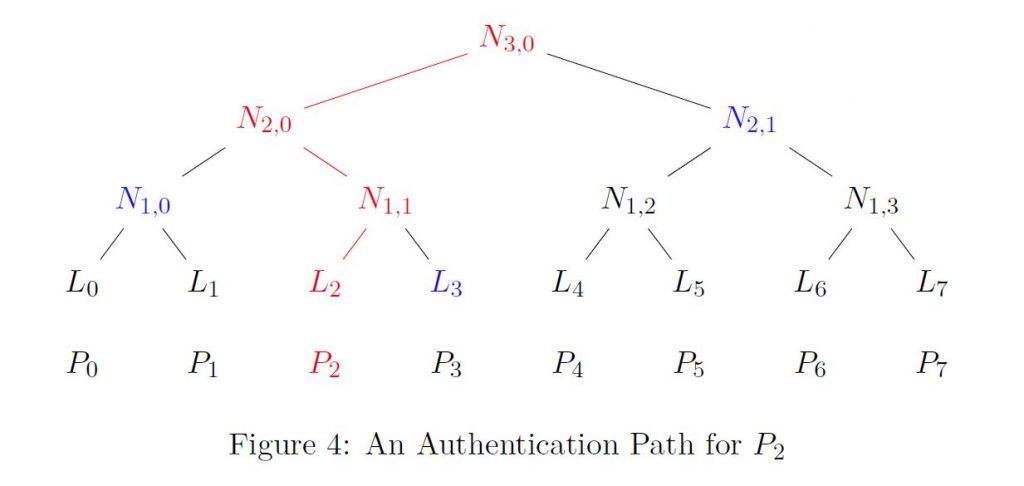
Math Paths To Quantum Safe Security Hash Based Cryptography Isara What is a hash based cryptography? the security of quantum resistant cryptographic algorithms of this category is based on the properties of cryptographic hash functions. among such properties we can distinguish ― resistance to the search for a prototype, collisions, the second prototype. Cryptographic hash functions are intended to be fast, deterministic, and one way, meaning that even a minor change in input yields a very different hash. these functions are important for securing information digitally by allowing data verification and authentication.
Comments are closed.