What Is An Ssh Tunnel Ssh Tunneling

Ssh Tunneling Tecadmin Ssh has the i option to tell which private key file to use when authenticating: i identity file selects a file from which the identity (private key) for rsa or dsa authentication is read. the default is ~ .ssh identity for protocol version 1, and ~ .ssh id rsa and ~ .ssh id dsa for protocol version 2. identity files may also be specified on a per host basis in the configuration file. it is. What is interesting there is the line: skipping ssh dss key root .ssh id dsa not in pubkeyacceptedkeytypes. this variable sounds like what i am looking for, but it is not defined within the sshd config.
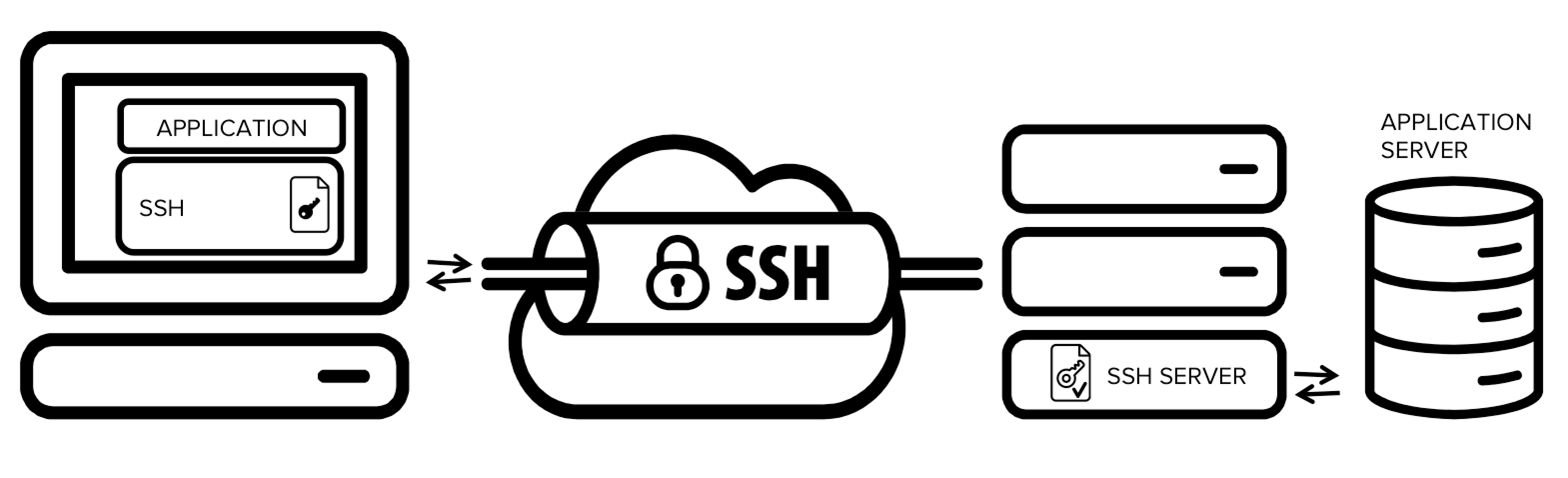
What Is An Ssh Tunnel Ssh Tunneling How do i set the host name and port in a config file for windows, using openssh through powershell? as on unix linux: edit or create the file now by typing: nano ~ .ssh config in here,. Want to transfer my local file to server by using linux terminal.suppose we used to access server by putty or ssh but not able to transfer there file by on same terminal. The fingerprint is based on the host's public key, usually based on the etc ssh ssh host rsa key.pub file. generally it's for easy identification verification of the host you are connecting to. With ssh i
What Is An Ssh Tunnel Ssh Tunneling The fingerprint is based on the host's public key, usually based on the etc ssh ssh host rsa key.pub file. generally it's for easy identification verification of the host you are connecting to. With ssh i

Ssh Tunnel And Ssh Tunneling Explained Evuzzo I'm trying to understand how openssh decides what key exchange method to use. what i don't see is how to specify the method. in addition, i know every ssh server client is required to support at le. I want to generate rsa sha2 256 ssh key pair using ssh keygen utility. can you please share the command for the same? for ssh rsa, it's ssh keygen t rsa. Is there a way to make ssh output what macs, ciphers, and kexalgorithms that it supports? i'd like to find out dynamically instead of having to look at the source. Ssh (s ecure sh ell) is a cryptographic network protocol to allow remote login and other network services to operate securely over an unsecured network. differences: sftp is works on interactive mode (session) and scp works on non interactive.
Github Yaobinwen Ssh Tunneling Explained Explain What Is Ssh Is there a way to make ssh output what macs, ciphers, and kexalgorithms that it supports? i'd like to find out dynamically instead of having to look at the source. Ssh (s ecure sh ell) is a cryptographic network protocol to allow remote login and other network services to operate securely over an unsecured network. differences: sftp is works on interactive mode (session) and scp works on non interactive.
Comments are closed.