What Is A Google Hacking Google Hack

Google Hacking Week Using Google To Hack Stuff Knightwise Google has confirmed it has been hacked — but what user information was compromised? here's what you need to know. Google hacking, also named google dorking, [1][2] is a hacker technique that uses google search and other google applications to find security holes in the configuration and computer code that websites are using.
Google Dorking How To Use Google For Hacking Hackproofhacks What is google hacking (dorking)? google hacking, sometimes, referred to as google dorking, is an information gathering technique used by an attacker leveraging advanced google searching techniques. Google hacking, also known as "google dorking", is the technique of using advanced search operators on google and other search engines to locate hard to find pages, vulnerable systems, and exposed sensitive data on websites. Google hacking (sometimes called google dorking) is when hackers use search engines to identify security vulnerabilities. with a bit of time and search know how, a hacker could figure out the best way to attack you. eliminating your site from google isn't smart. Hackers use a search engine e.g. b. google to find websites that are vulnerable to standard attacks or should remain hidden from the public. google hacking does not describe hacking by the google search engine itself, but how hackers can get help from the google search engine with a hack.

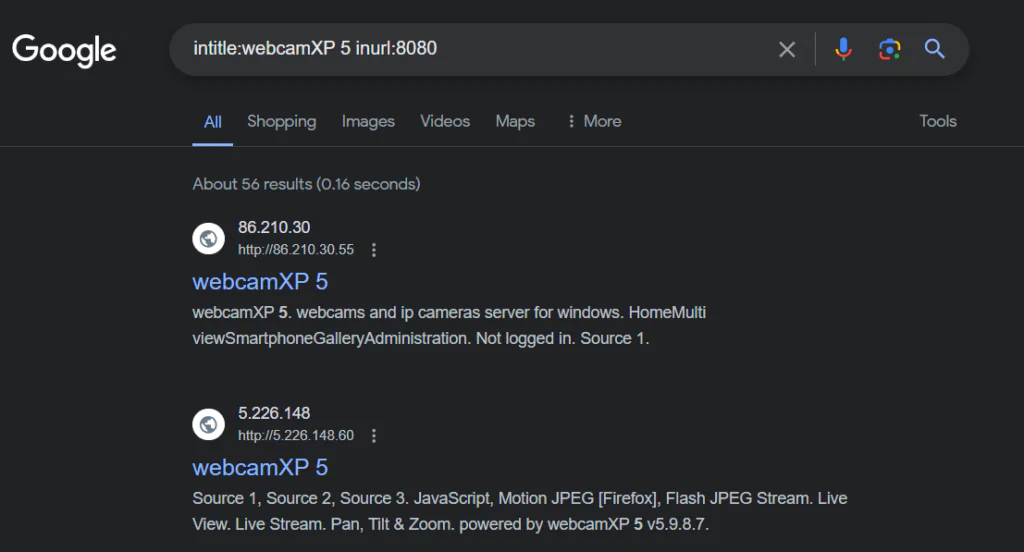
M K Hacking Google Hacking Hack Unprotected Web Cams Google hacking (sometimes called google dorking) is when hackers use search engines to identify security vulnerabilities. with a bit of time and search know how, a hacker could figure out the best way to attack you. eliminating your site from google isn't smart. Hackers use a search engine e.g. b. google to find websites that are vulnerable to standard attacks or should remain hidden from the public. google hacking does not describe hacking by the google search engine itself, but how hackers can get help from the google search engine with a hack. Google hacking is a term that encapsulates a wide range of techniques for querying google to reveal vulnerable web applications and sometimes to pinpoint vulnerabilities within specific web applications. Learn about google hacking, the google hacking database, and the tools used by hackers to exploit vulnerabilities in google search results. Google hacking refers to the use of advanced google search operators to find security vulnerabilities or sensitive data that is publicly accessible on the internet. also known as google dorking, this technique can expose login credentials, internal documents, and misconfigured servers. Google hacking, also known as google dorking, is a technique that uses advanced google search operators to find sensitive information, security vulnerabilities, and exposed files on the internet.

Hacking Google Thetvdb Google hacking is a term that encapsulates a wide range of techniques for querying google to reveal vulnerable web applications and sometimes to pinpoint vulnerabilities within specific web applications. Learn about google hacking, the google hacking database, and the tools used by hackers to exploit vulnerabilities in google search results. Google hacking refers to the use of advanced google search operators to find security vulnerabilities or sensitive data that is publicly accessible on the internet. also known as google dorking, this technique can expose login credentials, internal documents, and misconfigured servers. Google hacking, also known as google dorking, is a technique that uses advanced google search operators to find sensitive information, security vulnerabilities, and exposed files on the internet.
Comments are closed.