What Are The Main Elements Of A Vulnerability Management Process

Vulnerability Management Process Pdf Vulnerability Computing Another foundational element for any effective vulnerability management program is an up-to-date asset inventory with a process to ensure that it remains as current and comprehensive as possible 7 Do more than patching In the vulnerability management process, remediation must take shape in the context of a world where patching isn’t the only option

What Are The Main Elements Of A Vulnerability Management Process By prioritizing vulnerability management, companies can stay ahead of threats and ensure compliance through proactive measures rather than reactive fixes Investing in strong security measures Risk-based vulnerability management (VM) is the identification, prioritization and remediation of cyber-based vulnerabilities based on the relative risk they pose to a specific organization This paper addresses strategic risk management as an essential discipline for the sustainability of large corporations in an environment marked by increasing uncertainties and rapid transformations Vulnerability management is not a one-step process Conventional vulnerability management solutions rely on multiple tools to execute each step, making it hard for IT security teams
Vulnerability Management Doobsiss This paper addresses strategic risk management as an essential discipline for the sustainability of large corporations in an environment marked by increasing uncertainties and rapid transformations Vulnerability management is not a one-step process Conventional vulnerability management solutions rely on multiple tools to execute each step, making it hard for IT security teams CISA Issues Vulnerability-Management Tools Dependent on Industry Action Khanchit Khirisutchalual/Getty Images By Mariam Baksh November 10, 2022

7 Steps To Mapping A Strong Vulnerability Management Process Partner It CISA Issues Vulnerability-Management Tools Dependent on Industry Action Khanchit Khirisutchalual/Getty Images By Mariam Baksh November 10, 2022

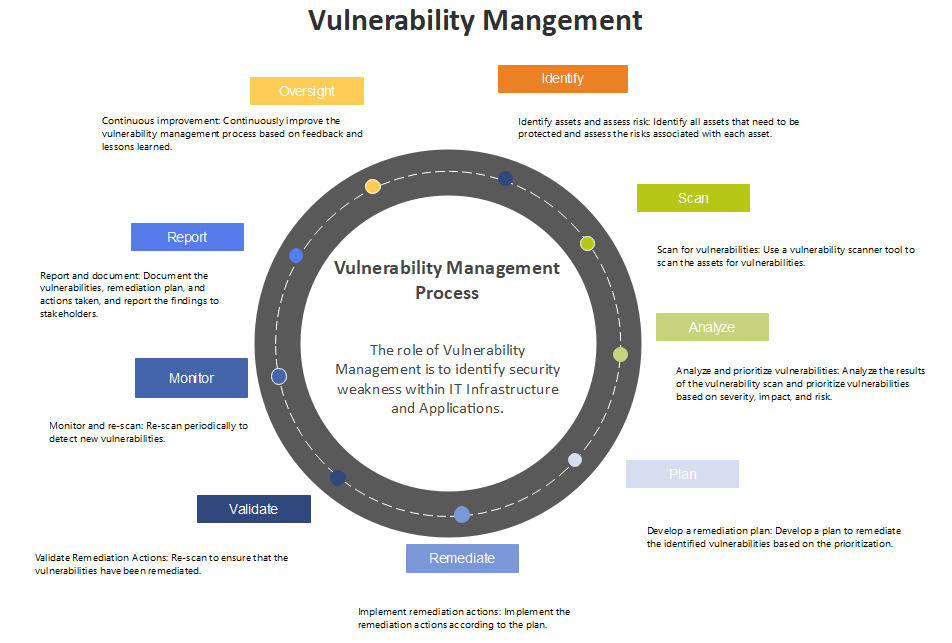
5 Main Stages Of The Vulnerability Management Process The Qa Lead

6 Steps To Creating A Strong Vulnerability Management Process B Comp
Comments are closed.