Vulnerability Management Process Flow Chart Vulnerability Management
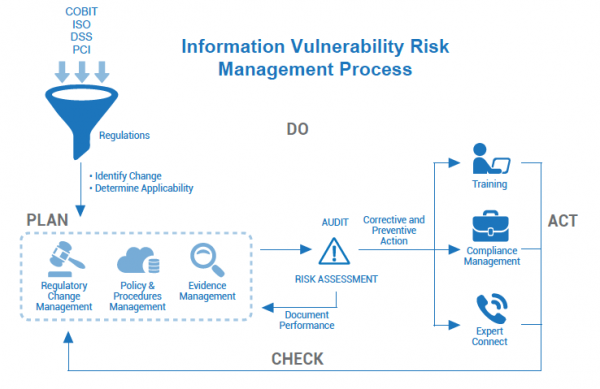
Vulnerability Management Process Flow Chart Vulnerability Management Learn what vulnerability management is, what steps are involved in the process, and how you can implement a robust vulnerability management program that leverages automation. A vulnerability management process flow chart can guide it security teams’ decision making to ensure they take the best steps for the safety of their organizations. read on to learn about how a vulnerability management process flow chart can benefit you.

Vulnerability Management Process Flow Chart Vulnerability Management A vulnerability management process flow chart may help security professionals make the best decisions for the protection of their organizations. this powerpoint slide showcases a vulnerability management process flow chart for an enterprise. There are five main stages in the vulnerability management lifecycle include: assess, prioritize, act, reassess, improve. learn more here. An iso 27001 vulnerability management process flow chart template gives you the visual roadmap to identify, assess and remediate risks and align with iso 27001 a.12.6 technical vulnerability management requirements. The cyclical nature of vulnerability management implies continuous process improvement, and it is crucial to understand how a single process feeds into other processes and how all tasks are interconnected across three domains.

Vulnerability Management Process Flow Chart Vulnerability Management An iso 27001 vulnerability management process flow chart template gives you the visual roadmap to identify, assess and remediate risks and align with iso 27001 a.12.6 technical vulnerability management requirements. The cyclical nature of vulnerability management implies continuous process improvement, and it is crucial to understand how a single process feeds into other processes and how all tasks are interconnected across three domains. Promote a dedicated process owner who will be responsible for the implementation and the management of the
Comments are closed.