Vulnerability Management Procedure Pdf Vulnerability Computing

Procedure Vulnerability Management Procedure Template En Download The purpose of this procedure is to delineate the steps involved in it vulnerability management in accordance with the usg vulnerability management policy found in the usg it handbook. Systems with open vulnerabilities present varying levels of risk to data and other systems depending on the severity of said vulnerabilities. the purpose of this procedure is to provide an outline for the management process of identified vulnerabilities on uc’s network.

Vulnerability Management Datasheet Pdf Vulnerability Computing The roles and vulnerability management responsibilities provided in this section have been extracted and summarized from cio 2100.1, federal guidance, or gsa security operations (secops) scanning team standard operating procedures processes. For example, this guide describes the process of performing a focused and defined vulnerability management process. the development of this process can be informed by the information learned and developed in a controls management process. The intent of this procedure is to establish a clear and efficient process for managing system vulnerabilities, ensuring the security and resilience of james cook university’s (jcu; the university) digital technology assets. This standard defines the requirements for notification, application of security related patches and procedures for vulnerability management. scope and applicability.

Vulnerability Management Standard It Procedure Template The intent of this procedure is to establish a clear and efficient process for managing system vulnerabilities, ensuring the security and resilience of james cook university’s (jcu; the university) digital technology assets. This standard defines the requirements for notification, application of security related patches and procedures for vulnerability management. scope and applicability. While you, as an individual or an organization, may not know all answers to the questions outlined in the owasp vulnerability management guide (ovmg or the guide), it should not prohibit your business from becoming more resilient through vulnerability management program adoption. Computer vulnerability management is a security practice designed to proactively prevent the exploitation of it vulnerabilities that exist within computers in an organization. This resource guide was developed to help locate resources to help you gain a working knowledge of the vulnerability management process as well as identify best practices for incorporating them into your own program. It details the roles and responsibilities of the it security team, system owners, and other stakeholders, as well as the steps for vulnerability scanning, remediation, reporting, and continuous improvement.
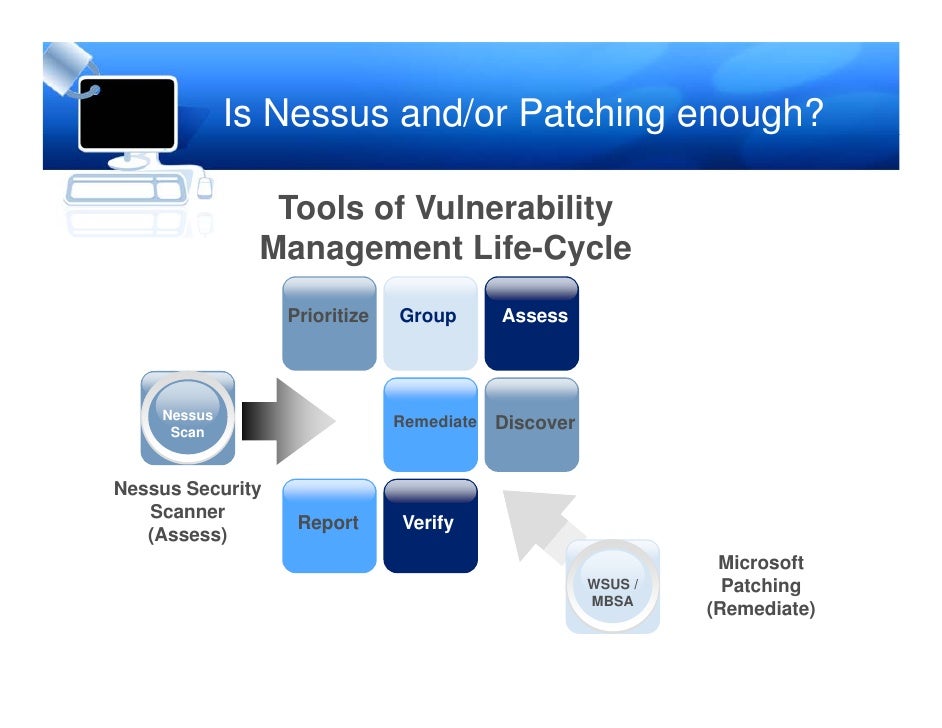
Vulnerability Management While you, as an individual or an organization, may not know all answers to the questions outlined in the owasp vulnerability management guide (ovmg or the guide), it should not prohibit your business from becoming more resilient through vulnerability management program adoption. Computer vulnerability management is a security practice designed to proactively prevent the exploitation of it vulnerabilities that exist within computers in an organization. This resource guide was developed to help locate resources to help you gain a working knowledge of the vulnerability management process as well as identify best practices for incorporating them into your own program. It details the roles and responsibilities of the it security team, system owners, and other stakeholders, as well as the steps for vulnerability scanning, remediation, reporting, and continuous improvement.

Vulnerability Management Procedure Pdf Vulnerability Computing This resource guide was developed to help locate resources to help you gain a working knowledge of the vulnerability management process as well as identify best practices for incorporating them into your own program. It details the roles and responsibilities of the it security team, system owners, and other stakeholders, as well as the steps for vulnerability scanning, remediation, reporting, and continuous improvement.
Comments are closed.