Vulnerability Management Lifecycle 5 Step Process Explained
Vulnerability Management Lifecycle 5 Step Process Explained There are five main stages in the vulnerability management lifecycle include: assess, prioritize, act, reassess, improve. learn more here. This article explained the need to cut down on manual processes, align to a well structured framework for compliance purposes, and follow the five main steps of the vulnerability management lifecycle.

Vulnerability Management Lifecycle A Comprehensive Guide King Obi Explore the vulnerability management lifecycle, from discovery to remediation. learn its five key steps, challenges, and best practices for cybersecurity. A typical round of the lifecycle has five stages: asset inventory and vulnerability assessment. vulnerability prioritization. vulnerability resolution. verification and monitoring. reporting and improvement. This detailed guide explains each of the five crucial stages, tools used, and best practices, helping cybersecurity students and professionals build strong defenses and prepare for certifications like oscp and ceh. learn how to implement this life cycle to protect your organization from cyber threats proactively. Moving from reactive patching to a structured vulnerability management lifecycle transforms security from tactical firefighting to strategic resilience engineering.

How To Set Up A Good Vulnerability Management Lifecycle Geek911 This detailed guide explains each of the five crucial stages, tools used, and best practices, helping cybersecurity students and professionals build strong defenses and prepare for certifications like oscp and ceh. learn how to implement this life cycle to protect your organization from cyber threats proactively. Moving from reactive patching to a structured vulnerability management lifecycle transforms security from tactical firefighting to strategic resilience engineering. The vulnerability management lifecycle can be divided into five steps, each one with its specific role in identifying, preventing, mitigating, and classifying vulnerabilities existent in your it infrastructure. the five steps are sequential, so when the final step of the lifecycle ends, the process restarts. There are three key phases in the initial vulnerability assessment stage. in this phase, you identify and inventory all of your organization’s digital assets, such as servers, workstations, and. Learn the 5 essential steps of the vulnerability management lifecycle with an example and the challenges organizations face in managing these vulnerabilities. In the following paragraphs, we will discuss the steps of the vulnerability management lifecycle and delve into the importance of each stage in detail. by implementing these steps diligently, organizations can build a resilient security framework that safeguards their valuable digital infrastructure and data against cyber threats.

Vulnerability Management Lifecycle Blue Team Resources The vulnerability management lifecycle can be divided into five steps, each one with its specific role in identifying, preventing, mitigating, and classifying vulnerabilities existent in your it infrastructure. the five steps are sequential, so when the final step of the lifecycle ends, the process restarts. There are three key phases in the initial vulnerability assessment stage. in this phase, you identify and inventory all of your organization’s digital assets, such as servers, workstations, and. Learn the 5 essential steps of the vulnerability management lifecycle with an example and the challenges organizations face in managing these vulnerabilities. In the following paragraphs, we will discuss the steps of the vulnerability management lifecycle and delve into the importance of each stage in detail. by implementing these steps diligently, organizations can build a resilient security framework that safeguards their valuable digital infrastructure and data against cyber threats.
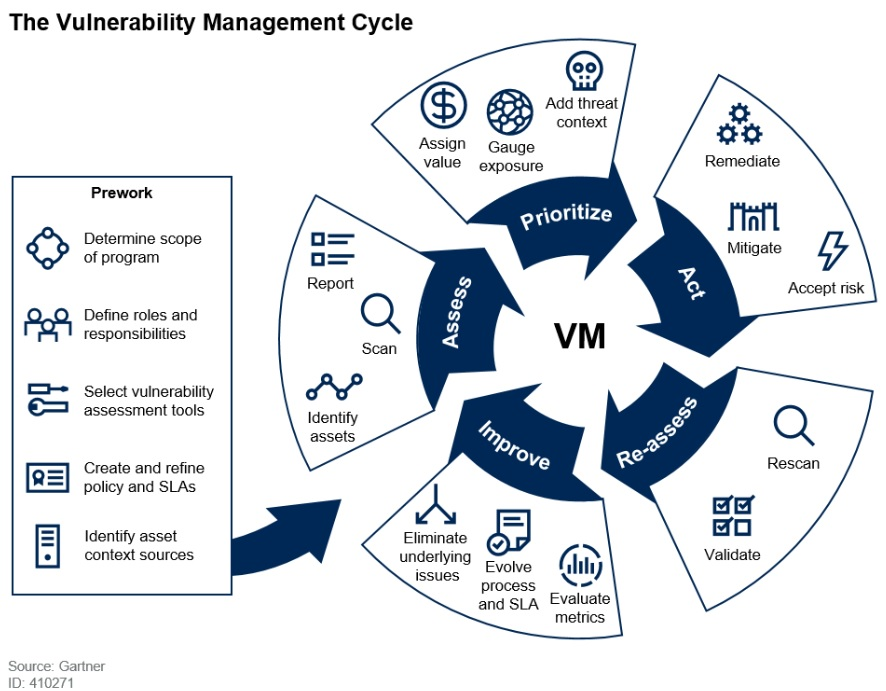
Vulnerability Management Lifecycle Process And Best Practices Learn the 5 essential steps of the vulnerability management lifecycle with an example and the challenges organizations face in managing these vulnerabilities. In the following paragraphs, we will discuss the steps of the vulnerability management lifecycle and delve into the importance of each stage in detail. by implementing these steps diligently, organizations can build a resilient security framework that safeguards their valuable digital infrastructure and data against cyber threats.
Vulnerability Management Lifecycle A Comprehensive Guide
Comments are closed.