Usenix Security 23 A Data Free Backdoor Injection Approach In Neural Networks
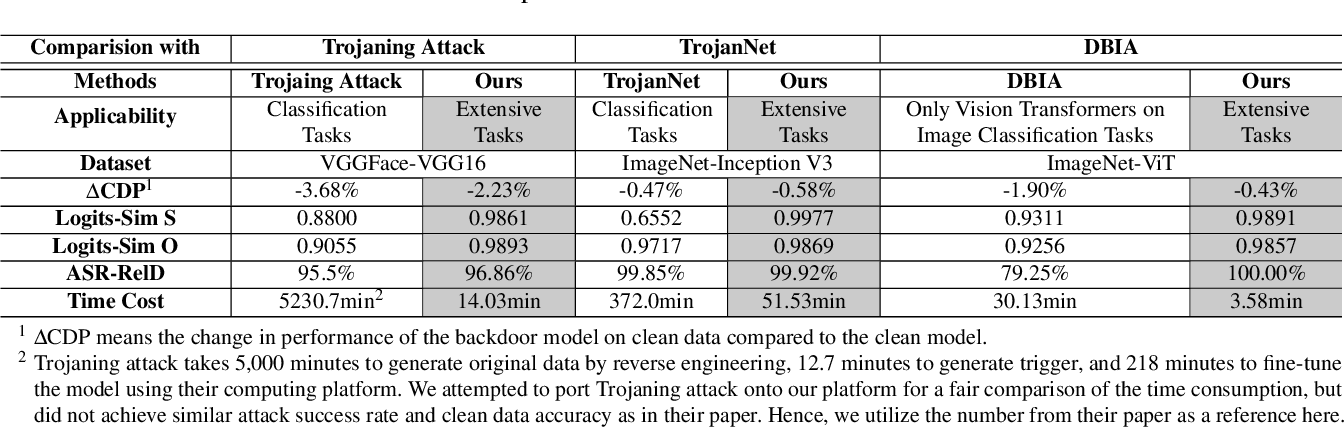
Table 3 From A Data Free Backdoor Injection Approach In Neural Networks • we propose a new data free backdoor injection approach by designing a novel loss function that crafts a backdoored dnn model from a clean one based on the built substitute dataset irrelevant to the main task. In this paper, we propose a novel backdoor injection approach in a "data free" manner. we collect substitute data irrelevant to the main task and reduce its volume by filtering out redundant samples to improve the efficiency of backdoor injection.
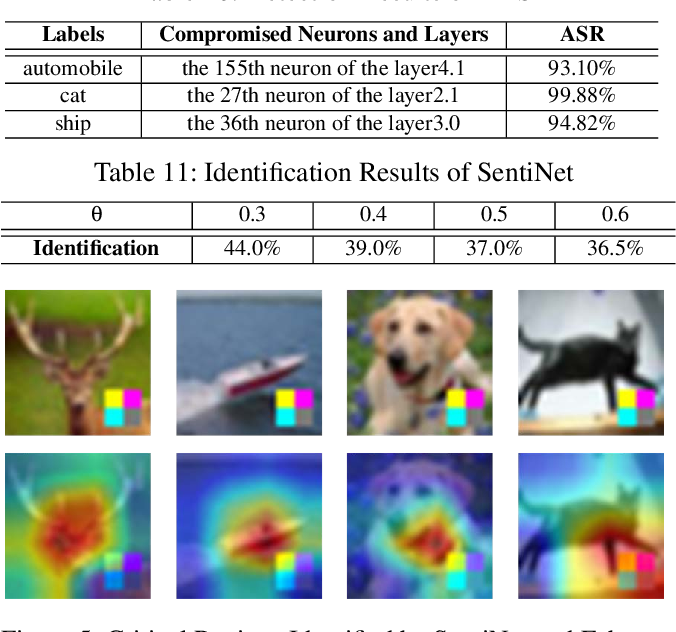
Table 2 From A Data Free Backdoor Injection Approach In Neural Networks Many thanks to usenix for publishing their outstanding usenix security ’23 presenter’s content, and the organizations strong commitment to open access. originating from the conference’s events situated at the anaheim marriott; and via the organizations channel. Usenix security '23 a data free backdoor injection approach in neural networks peizhuo lv, chang yue, ruigang liang, and yunfei yang, sklois, institute of information more. This repository contains the pytorch implementation of "a data free backdoor injection approach in neural networks". our paper is accepted by the 32nd usenix security symposium (usenix security 2023). Openreview is a long term project to advance science through improved peer review with legal nonprofit status. we gratefully acknowledge the support of the openreview sponsors. © 2025 openreview.
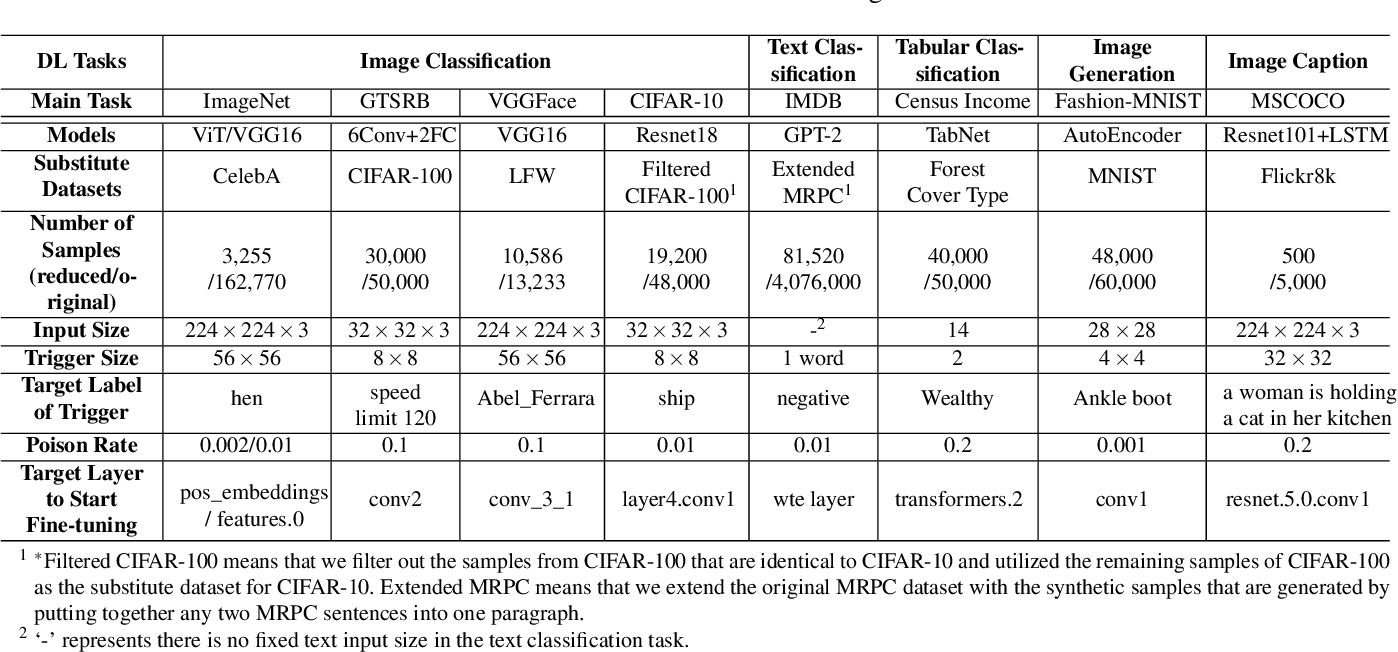
Table 8 From A Data Free Backdoor Injection Approach In Neural Networks This repository contains the pytorch implementation of "a data free backdoor injection approach in neural networks". our paper is accepted by the 32nd usenix security symposium (usenix security 2023). Openreview is a long term project to advance science through improved peer review with legal nonprofit status. we gratefully acknowledge the support of the openreview sponsors. © 2025 openreview. A data free backdoor injection approach in neural networks donate today submitted by arnold on march 22, 2023 4:09 pm dblp. 本文提出的data free的后门攻击手段,实现了不使用原始数据集而达到后门注入的目的。 提出了替代数据集以及对其优化的方法,并且提出了先进的后门注入方法,主要体现在对参数的动态优化上。. This repository contains the pytorch implementation of "a data free backdoor injection approach in neural networks". our paper is accepted by the 32nd usenix security symposium (usenix security 2023). Usenix security brings together researchers, practitioners, system administrators, system programmers, and others to share and explore the latest advances in the security and privacy of computer systems and networks.
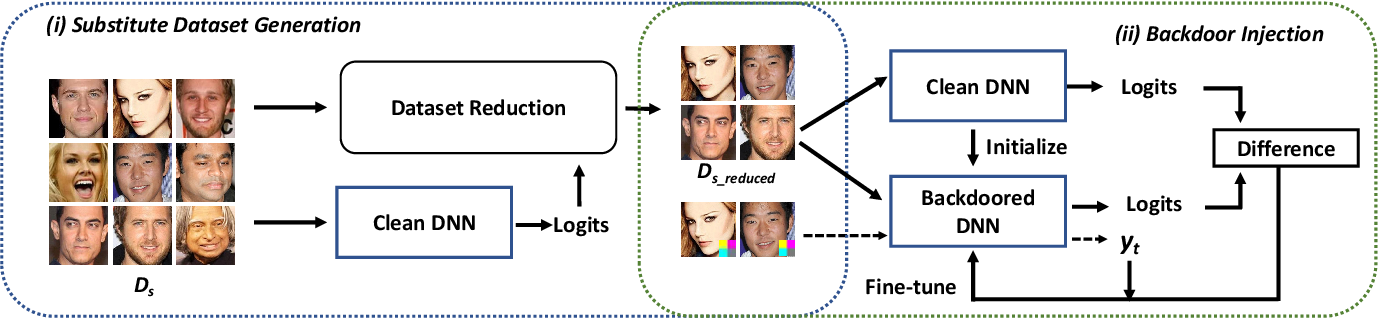
Figure 2 From A Data Free Backdoor Injection Approach In Neural A data free backdoor injection approach in neural networks donate today submitted by arnold on march 22, 2023 4:09 pm dblp. 本文提出的data free的后门攻击手段,实现了不使用原始数据集而达到后门注入的目的。 提出了替代数据集以及对其优化的方法,并且提出了先进的后门注入方法,主要体现在对参数的动态优化上。. This repository contains the pytorch implementation of "a data free backdoor injection approach in neural networks". our paper is accepted by the 32nd usenix security symposium (usenix security 2023). Usenix security brings together researchers, practitioners, system administrators, system programmers, and others to share and explore the latest advances in the security and privacy of computer systems and networks.
Comments are closed.