Understanding Vulnerabilities In Android Os Architecture

Security Vulnerabilities In Android Applications Pdf Mobile App Securing an android app is a complex and critical task that requires a comprehensive and thorough approach. organizations should consider all the key components of an android app and test them for security vulnerabilities, ensuring that the app is secure and the data it handles is protected. By contextualizing hardware vulnerabilities within the broader security architecture of android devices, this review emphasizes the importance of hardware security in ensuring system integrity and resilience.

Android Had The Most Vulnerabilities Of Any Os In 2019 Says Report This paper focuses on understanding and analyzing the vulnerabilities present in android platform. in this paper firstly we study the android architecture; analyze the existing threats and security weaknesses. then we identify various exploit mitigation techniques to mitigate known vulnerabilities. This research has emphasized the various vulnerabilities and bugs of the android operating system discovered in recent years. furthermore, this study intends to provide possible mitigation techniques against the existing vulnerabilities of the android system. Before diving into mobile pentesting, you should first understand android’s architecture. knowing how android is structured helps you identify where vulnerabilities may exist — whether. In this paper, we survey a collection of anti malware techniques and organize these techniques into three canonical classes (static methods, dynamic methods, hybrid methodologies) according to how.
Understanding Vulnerabilities In Android Os Architecture Before diving into mobile pentesting, you should first understand android’s architecture. knowing how android is structured helps you identify where vulnerabilities may exist — whether. In this paper, we survey a collection of anti malware techniques and organize these techniques into three canonical classes (static methods, dynamic methods, hybrid methodologies) according to how. Learn how vulnerabilities in rooting frameworks like kernelsu can expose your android device to severe security risks, and discover how zimperium zlabs helps mitigate these threats. In this paper, we perform the first study of android system vulnerabilities by comprehensively analyzing all 2,179 vulnerabilities on the android security bulletin program over about three years since its initiation in august 2015. This article explores key components of android application architecture and demonstrates common vulnerabilities in intentionally vulnerable apps found in the wild. Android allows developers to freely access and modify source code. this paper focuses on analyzing and understanding the vulnerabilities present in android. in this paper we have to study about how to check the vulnerability and exploiting the android smart phones. 1. introduction.
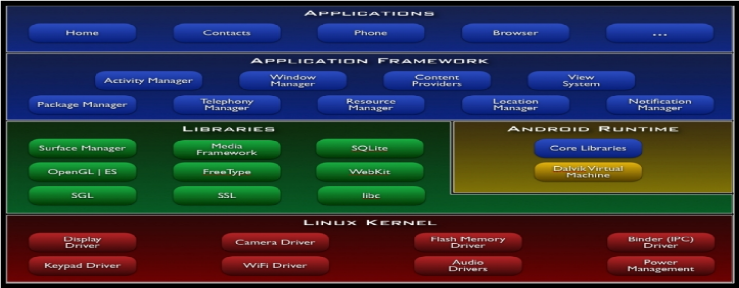
Understanding Vulnerabilities In Android Os Architecture Learn how vulnerabilities in rooting frameworks like kernelsu can expose your android device to severe security risks, and discover how zimperium zlabs helps mitigate these threats. In this paper, we perform the first study of android system vulnerabilities by comprehensively analyzing all 2,179 vulnerabilities on the android security bulletin program over about three years since its initiation in august 2015. This article explores key components of android application architecture and demonstrates common vulnerabilities in intentionally vulnerable apps found in the wild. Android allows developers to freely access and modify source code. this paper focuses on analyzing and understanding the vulnerabilities present in android. in this paper we have to study about how to check the vulnerability and exploiting the android smart phones. 1. introduction.

Understanding Vulnerabilities In Android Os Architecture This article explores key components of android application architecture and demonstrates common vulnerabilities in intentionally vulnerable apps found in the wild. Android allows developers to freely access and modify source code. this paper focuses on analyzing and understanding the vulnerabilities present in android. in this paper we have to study about how to check the vulnerability and exploiting the android smart phones. 1. introduction.
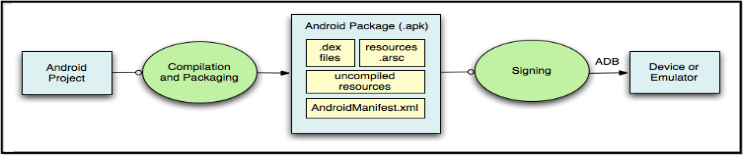
Understanding Vulnerabilities In Android Os Architecture
Comments are closed.