Understand Malware Behavior Faster With The Process Tree In Any Run
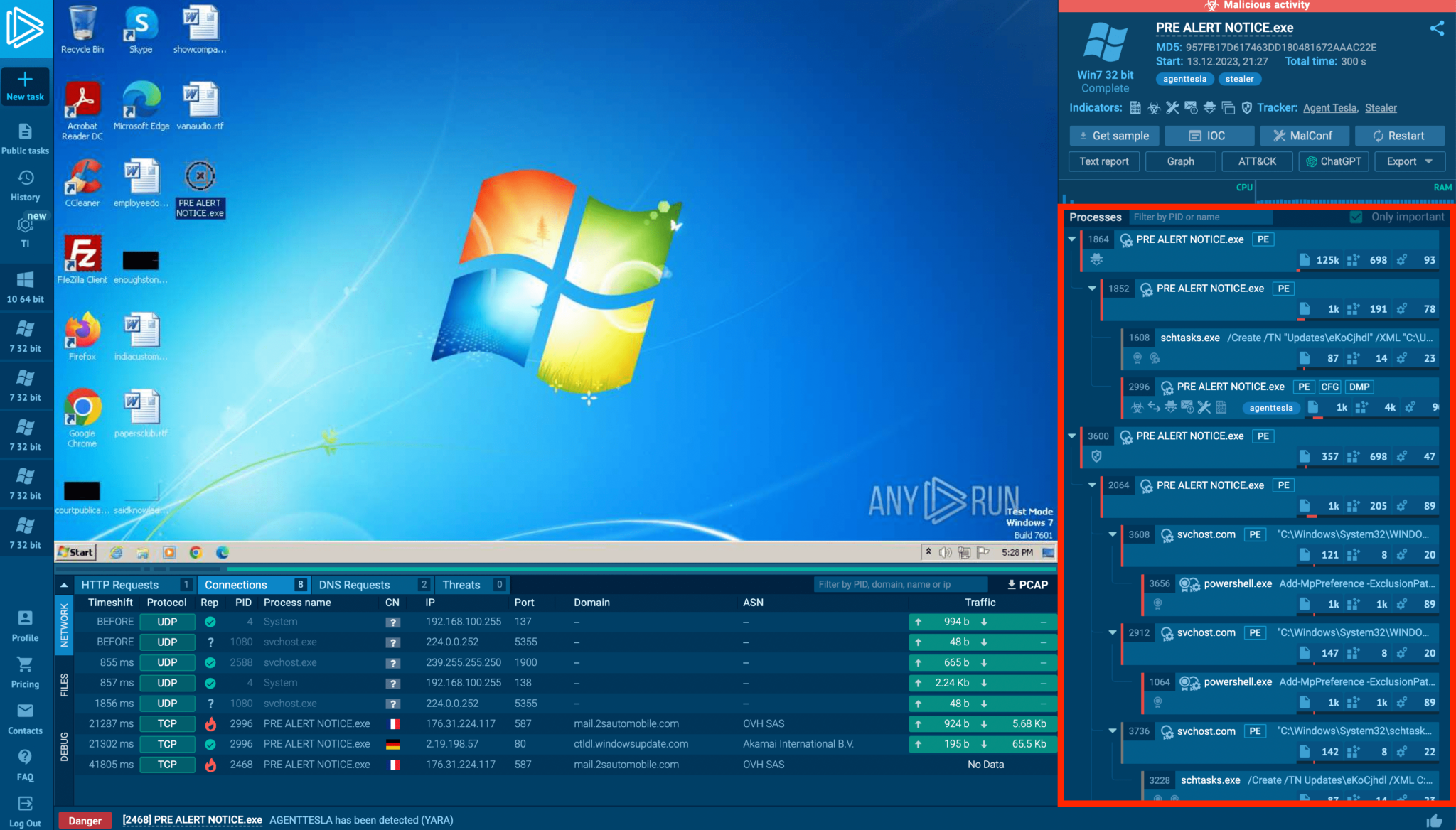
Quickly Check If A File Is Malicious With Any Run S Process Tree Today, we’ll show you how to use the process tree in any.run to visualize malware execution flow in real time. track parent child process relationships, spot anomalies, and detect suspicious. In any.run, the process tree helps you quickly gather essential analytical information. in this article, we’ll explain what the process tree is, how to use it effectively, and what insights you can gain from a superficial analysis of a sample.
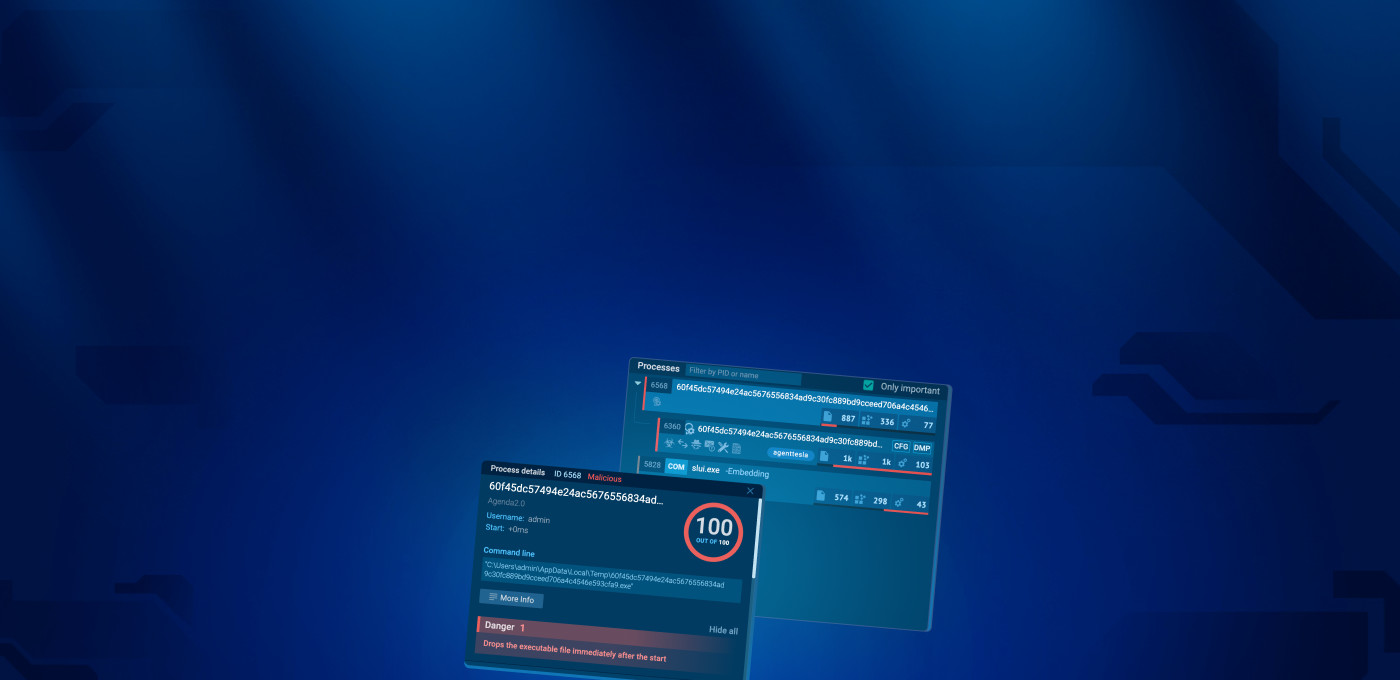
Quickly Check If A File Is Malicious With Any Run S Process Tree According to the any.run detailed write up, the process tree visualizes process relationships and provides tools for analysis, while icons indicate suspicious activities and process signatures. clicking icons reveals static information like pe details, memory dumps, and configuration files. Now, you can investigate android malware in a real arm based sandbox, exactly as it would behave on an actual mobile device. no more blind spots or unreliable analysis. Any.run revolutionizes the way security professionals approach malware analysis by providing an intuitive, browser based interface that allows analysts to observe malware behavior in real time while maintaining complete control over the analysis environment. whether you’re investigating suspicious email attachments, analyzing potential advanced persistent threats (apts), or conducting threat. The visual process tree and network analysis allow us to see an attack’s full scope in one place, which really speeds up our containment and remediation processes.

Mastering 4 Stages Of Malware Analysis Pdf Malware Intelligence Any.run revolutionizes the way security professionals approach malware analysis by providing an intuitive, browser based interface that allows analysts to observe malware behavior in real time while maintaining complete control over the analysis environment. whether you’re investigating suspicious email attachments, analyzing potential advanced persistent threats (apts), or conducting threat. The visual process tree and network analysis allow us to see an attack’s full scope in one place, which really speeds up our containment and remediation processes. By creating the process trees and analyzing them, we can detect the anomalous process tree (in orange) and investigate if it’s malicious or not. this method can help us to uncover lots of attacks that are not detected. In this article, we’ll explain what the process tree is, how to use it effectively, and what insights you can gain from a superficial analysis of a sample. by the end, you’ll be able to determine if a file or url is malicious without having to dive too deep. See how you can easily understand the infection chain of any malware by using the process graph report in the any.run sandbox. Any.run’s process graphs display attack patterns in an interactive visual tree structure, allowing analysts to quickly identify malicious processes and obtain more detailed information.
Comments are closed.