Top 10 Hacking Techniques Explained In 10 Minutes Ethical Hacking

Ethical Hacking Techniques Pdf Security Hacker White Hat You'll learn how these attacks work, see real life examples, and get practical tips on how to protect yourself and your organization from these cyber threats. by understanding these common. You'll learn how these attacks work, see real life examples, and get practical tips on how to protect yourself and your organization from these cyber threats. by understanding these common hacking techniques, you'll be better equipped to defend against them and keep your data secure. let's dive in!.

Top 10 Hacking Techniques Explained In 10 Minutes Ethical Hacking The following strategies lay out how we can safeguard systems and data against these vulnerabilities, integrate ethical hacking techniques and gain insights into the types of hacking techniques that cybercriminals frequently use. If you’re serious about cybersecurity — whether you’re a red teamer, a blue teamer, or somewhere in the middle — these are the top 10 ethical hacking techniques you should have in your. Using simple hacks, a hacker can learn about your personal unauthorized information which you might not want to reveal. knowing about these common hacking techniques like phishing, ddos,. Ethical hackers, or white hat hackers, play a crucial role in identifying and fixing security vulnerabilities before malicious hackers can exploit them. this blog unveils the top 10 ethical hacking techniques of 2025 that are revolutionizing how organizations protect their digital assets.
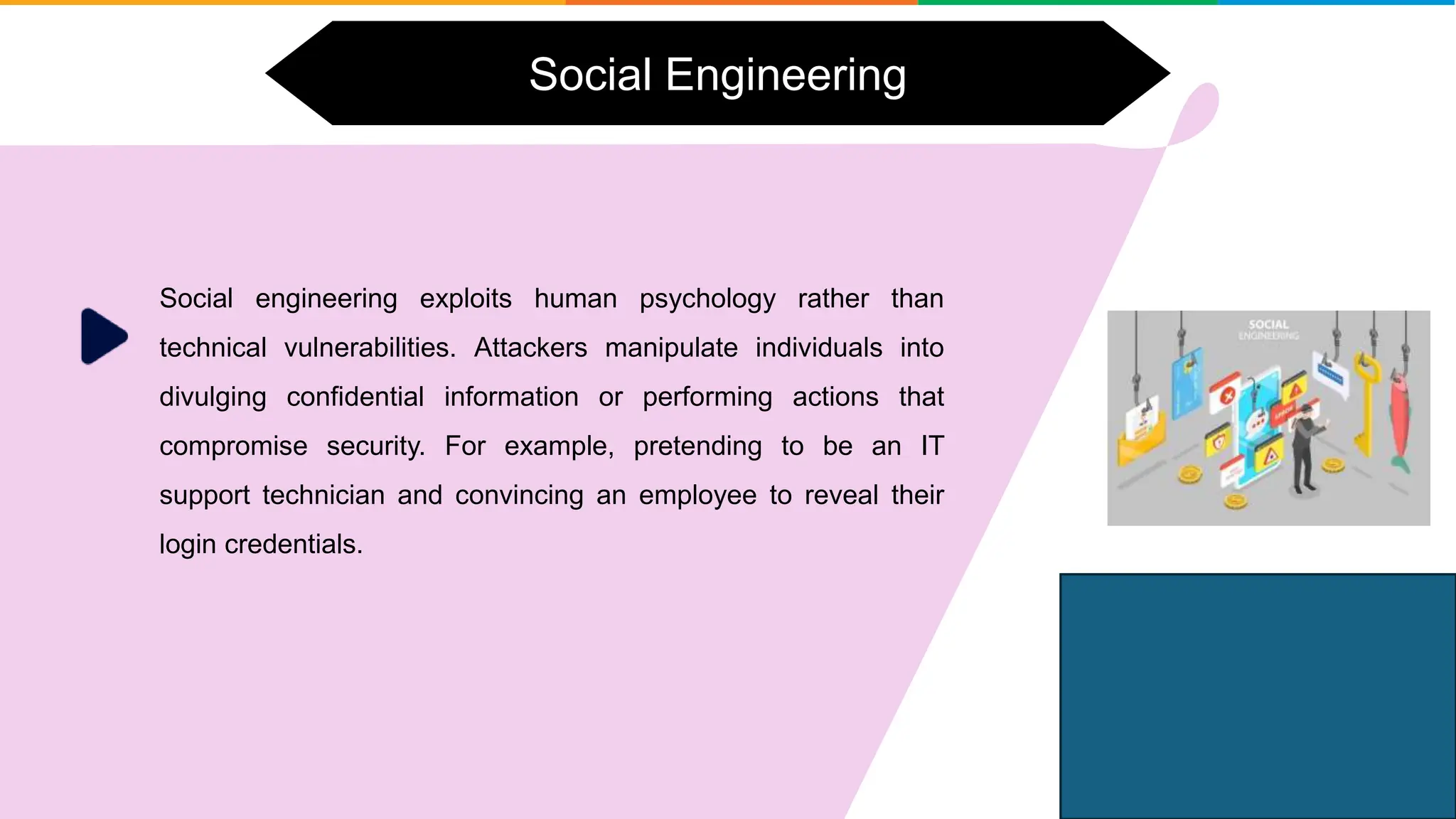
Top 10 Hacking Techniques Explained In 10 Minutes Ethical Hacking Using simple hacks, a hacker can learn about your personal unauthorized information which you might not want to reveal. knowing about these common hacking techniques like phishing, ddos,. Ethical hackers, or white hat hackers, play a crucial role in identifying and fixing security vulnerabilities before malicious hackers can exploit them. this blog unveils the top 10 ethical hacking techniques of 2025 that are revolutionizing how organizations protect their digital assets. From understanding the hacking basics to diving into advanced ethical hacking techniques, including footprinting and reconnaissance, scanning networks, enumeration, and more. Explore ethical hacking techniques, tools, trends, cyberattacks, vulnerable devices, and the history of hacking to enhance cybersecurity and protect systems. Ethical hacking is used to find potential security issues in computer systems and networks. in this post, we’ll cover a collection of techniques and procedures commonly used by ethical hackers to find vulnerabilities before malicious users can take advantage. This blog post explores 40 hacking techniques, detailing their methods, examples, and tools used by ethical hackers. it emphasizes the importance of cybersecurity awareness and the need for robust security measures to protect against these threats.
Comments are closed.