Tokenization For Improved Data Security Overview And Process Of
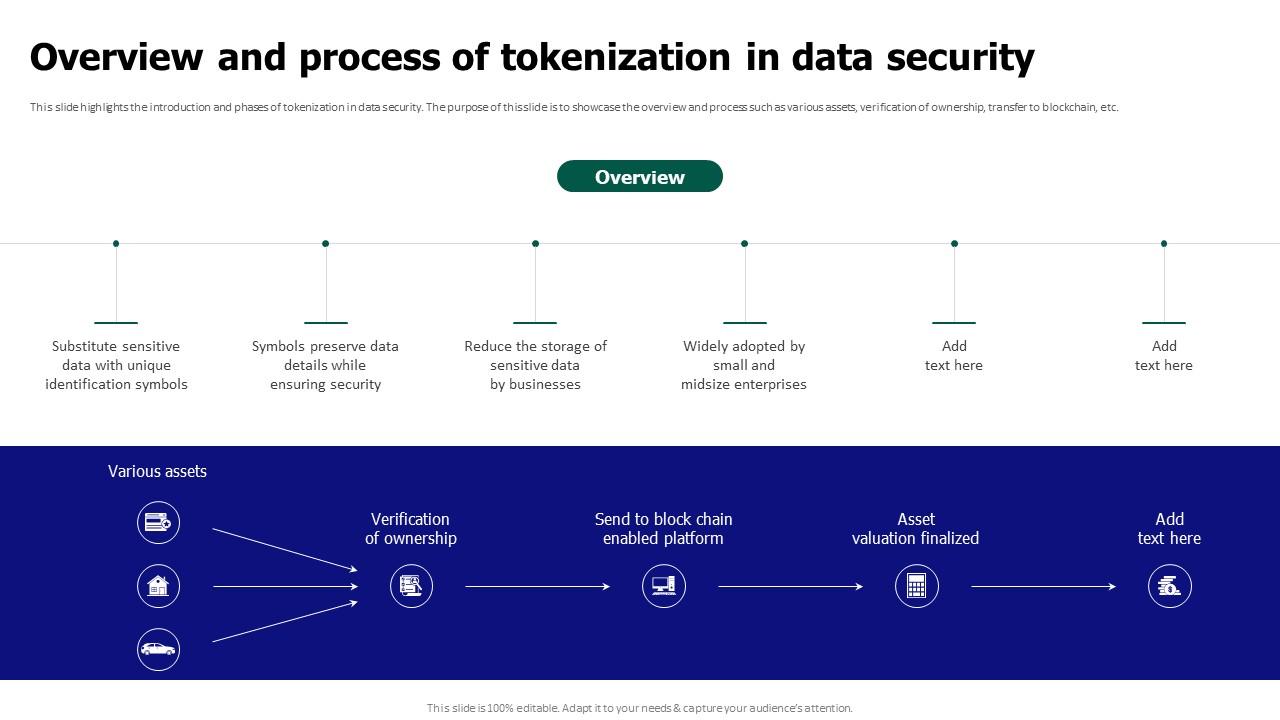
Tokenization For Improved Data Security Overview And Process Of By replacing sensitive data with non sensitive tokens, tokenization offers a highly secure method to store, process, and transmit data, reducing the risk of data breaches and helping organizations meet industry standards. In data security, tokenization is the process of converting sensitive data into a nonsensitive digital replacement, called a token, that maps back to the original. tokenization can help protect sensitive information. for example, sensitive data can be mapped to a token and placed in a digital vault for secure storage.

Tokenization For Improved Data Security Overview Of Security Industries subject to financial, data security, regulatory, or privacy compliance standards are increasingly looking for tokenization solutions to minimize distribution of sensitive data, reduce risk of exposure, improve security posture, and alleviate compliance obligations. Tokenization, when applied to data security, is the process of substituting a sensitive data element with a non sensitive equivalent, referred to as a token, that has no intrinsic or exploitable meaning or value. Data tokenization is a data security process that replaces sensitive data with a non sensitive value, called a token. tokens can be random numbers, strings of characters, or any other non identifiable value. when sensitive data is tokenized, the original data is stored securely in a token vault. Learn how to implement tokenization to protect sensitive data and enhance your system's security. this guide covers the tokenization process, benefits, and best practices.
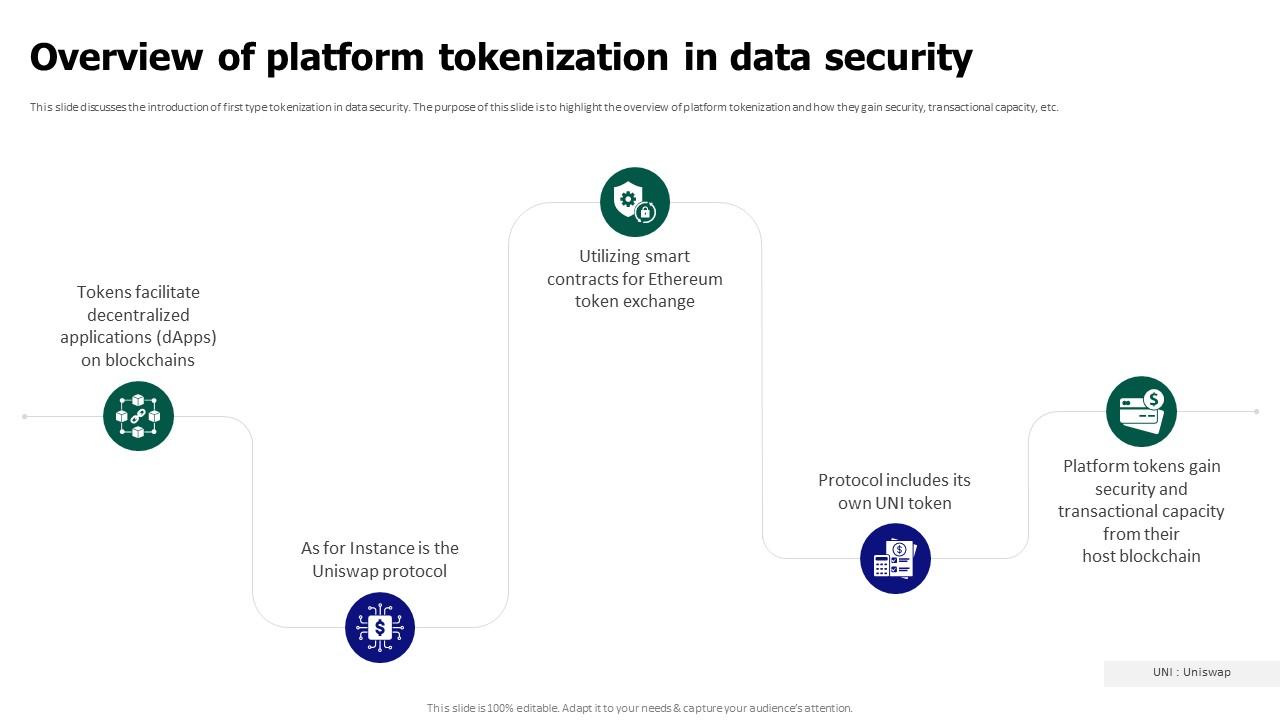
Tokenization For Improved Data Security Overview Of Platform Data tokenization is a data security process that replaces sensitive data with a non sensitive value, called a token. tokens can be random numbers, strings of characters, or any other non identifiable value. when sensitive data is tokenized, the original data is stored securely in a token vault. Learn how to implement tokenization to protect sensitive data and enhance your system's security. this guide covers the tokenization process, benefits, and best practices. At its core, tokenization is the process of exchanging sensitive data for non sensitive data called tokens. these tokens retain certain elements of the original data, such as length and format, but are undecipherable and irreversible. Data tokenization replaces sensitive data with random tokens, ensuring security by preventing unauthorized access during storage and transmission. tokenization not only supports regulatory compliance but also reduces risks from insider threats, enhancing overall data protection and customer trust. As businesses navigate an increasingly challenging and complex web of privacy regulations, data tokenization – a method that replaces sensitive data with non sensitive placeholders, offering enhanced security without compromising usability – looks set to be the future of digital security. This comprehensive article delves into the critical role of tokenization in modern data security, exploring its core concepts, operational mechanisms, and distinct advantages over traditional encryption methods.

Tokenization For Improved Data Security Main Data Security Tokenization At its core, tokenization is the process of exchanging sensitive data for non sensitive data called tokens. these tokens retain certain elements of the original data, such as length and format, but are undecipherable and irreversible. Data tokenization replaces sensitive data with random tokens, ensuring security by preventing unauthorized access during storage and transmission. tokenization not only supports regulatory compliance but also reduces risks from insider threats, enhancing overall data protection and customer trust. As businesses navigate an increasingly challenging and complex web of privacy regulations, data tokenization – a method that replaces sensitive data with non sensitive placeholders, offering enhanced security without compromising usability – looks set to be the future of digital security. This comprehensive article delves into the critical role of tokenization in modern data security, exploring its core concepts, operational mechanisms, and distinct advantages over traditional encryption methods.
Tokenization For Improved Data Security Tokenization Process Activities As businesses navigate an increasingly challenging and complex web of privacy regulations, data tokenization – a method that replaces sensitive data with non sensitive placeholders, offering enhanced security without compromising usability – looks set to be the future of digital security. This comprehensive article delves into the critical role of tokenization in modern data security, exploring its core concepts, operational mechanisms, and distinct advantages over traditional encryption methods.
Comments are closed.