Teleport Matches Page Explained Link Skus To 3d Files
Teleport 3d Models Sketchfab By eliminating anonymous computing and implementing a task based access control model, teleport significantly improves infrastructure resiliency and reduces the risk of human error and compromise. Teleport is the easiest, most secure way to access and protect all your infrastructure. the teleport infrastructure identity platform implements trusted computing at scale, with unified cryptographic identities for humans, machines and workloads, endpoints, infrastructure assets, and ai agents.

Teleport 3d Models Sketchfab Dive into our guide for a clear understanding of teleport’s foundational concepts and architecture. learn about the teleport platform's structure, how teleport clusters operate, and what users can expect from the teleport experience. Download teleport for the easiest, most secure way to access and protect all of your infrastructure. get started now!. Discover teleport's scalable and secure infrastructure access solutions for organizations of all sizes. enjoy advanced security features, compliance controls, and priority support with our cloud or self hosted plans. How to install teleport and teleport's client tools on your platform, including binaries and instructions for docker and helm.

Teleport 3d Models Sketchfab Discover teleport's scalable and secure infrastructure access solutions for organizations of all sizes. enjoy advanced security features, compliance controls, and priority support with our cloud or self hosted plans. How to install teleport and teleport's client tools on your platform, including binaries and instructions for docker and helm. The changelog provides a comprehensive description of the changes introduced by each teleport release. Explore teleport's comprehensive features, including certificate based authentication, single sign on, and advanced security protocols. discover how teleport enhances infrastructure management for both open source and enterprise users. Teleport modernizes access control for both users and machines with cryptographic identity, zero trust, and ephemeral privileges, removing credentials and standing privileges as an attack vector. Teleport the easiest, most secure way to access and protect all of your infrastructure.
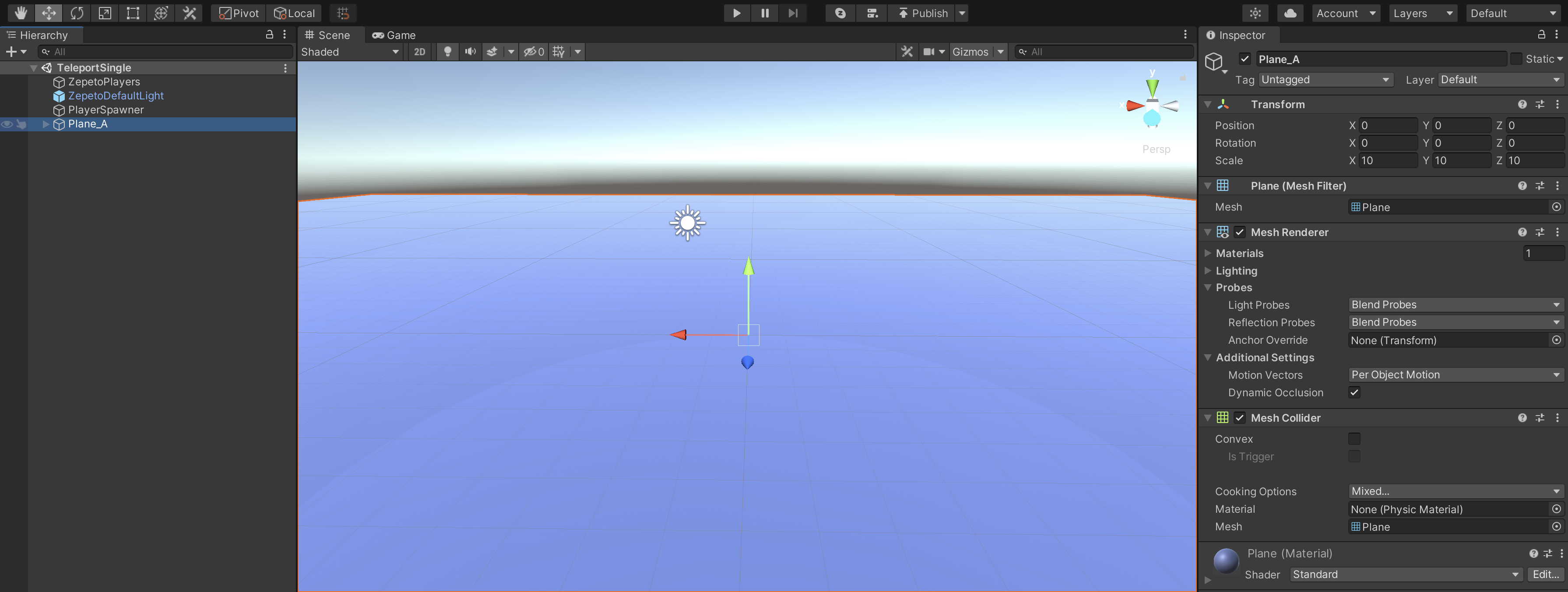
Teleport Implementation The changelog provides a comprehensive description of the changes introduced by each teleport release. Explore teleport's comprehensive features, including certificate based authentication, single sign on, and advanced security protocols. discover how teleport enhances infrastructure management for both open source and enterprise users. Teleport modernizes access control for both users and machines with cryptographic identity, zero trust, and ephemeral privileges, removing credentials and standing privileges as an attack vector. Teleport the easiest, most secure way to access and protect all of your infrastructure.

Teleport 3d Models Download Free3d Teleport modernizes access control for both users and machines with cryptographic identity, zero trust, and ephemeral privileges, removing credentials and standing privileges as an attack vector. Teleport the easiest, most secure way to access and protect all of your infrastructure.

Teleport 3d Models Download Free3d
Comments are closed.