Teleport For Ssh Kubectl Explanation Privileged Access Management Pam Jump Host Bastion

Privileged Access Management Pam Teleport Teleport is a gateway for managing access to clusters of linux servers via ssh or the kubernetes api. it is intended to be used instead of traditional openss. Discover how to integrate teleport's node service with pam for secure, unified infrastructure access. follow ben arent's step by step guide for seamless implementation.

Privileged Access Management Pam Teleport The plugin automatically check if there are any ssh agents started running by the plugin, and starts ssh agent if it doesn't find any ssh agent running and adds ssh identity key into the agent before ssh login. Use kubectl to access your cluster. the magic thing here is that teleport will update your ~ .kube config file in order to access your cluster. it really works well and you should consider giving it a try. in the case you're using chef, i have made a cookbook for teleport. This article explores privileged access management (pam), explaining its importance in securing critical systems and sensitive data. it covers best practices, common pitfalls, practical applications, and future trends like zero trust and ai integration. To implement fine grained access controls using teleport, the first step is to register your kubernetes clusters with the teleport service. here are the steps to achieve this:.
Modernize Privileged Access Management With Teleport Secure Zero This article explores privileged access management (pam), explaining its importance in securing critical systems and sensitive data. it covers best practices, common pitfalls, practical applications, and future trends like zero trust and ai integration. To implement fine grained access controls using teleport, the first step is to register your kubernetes clusters with the teleport service. here are the steps to achieve this:. Teleport has been offering an elegant way to provide ssh access across all clouds to all approved employees, but with this release, we are finally extending these powerful features to all major kubernetes vendors. Gravitational teleport provides privileged access management (pam) for cloud native infrastructure. teleport is an access and authentication proxy for ssh and kubernetes api access. it’s meant as a replacement for sshd and it works with existing openssh clients and servers as is. Many organizations have successfully implemented privileged access management (pam) for ssh access. these use cases demonstrate the effectiveness of pam in securing critical systems and mitigating the risks associated with privileged access. To address this, teleport provides a robust solution for implementing just in time (jit) privileged access, ensuring that users have the necessary permissions only when they need them and for.

Privileged Access Management Pam Teleport Teleport has been offering an elegant way to provide ssh access across all clouds to all approved employees, but with this release, we are finally extending these powerful features to all major kubernetes vendors. Gravitational teleport provides privileged access management (pam) for cloud native infrastructure. teleport is an access and authentication proxy for ssh and kubernetes api access. it’s meant as a replacement for sshd and it works with existing openssh clients and servers as is. Many organizations have successfully implemented privileged access management (pam) for ssh access. these use cases demonstrate the effectiveness of pam in securing critical systems and mitigating the risks associated with privileged access. To address this, teleport provides a robust solution for implementing just in time (jit) privileged access, ensuring that users have the necessary permissions only when they need them and for.
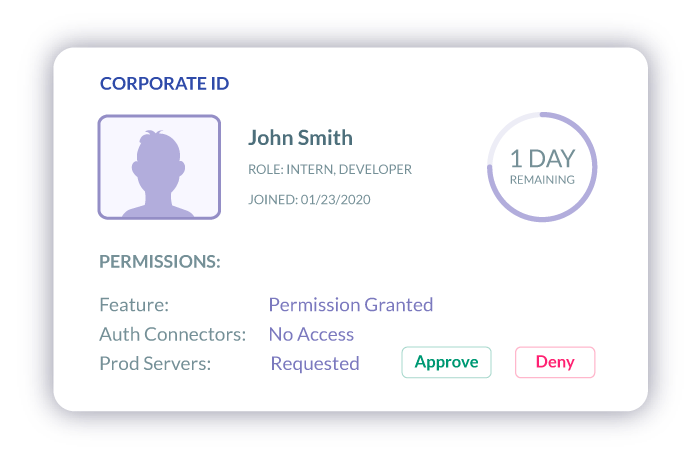
Teleport Ssh Jump Server Teleport Many organizations have successfully implemented privileged access management (pam) for ssh access. these use cases demonstrate the effectiveness of pam in securing critical systems and mitigating the risks associated with privileged access. To address this, teleport provides a robust solution for implementing just in time (jit) privileged access, ensuring that users have the necessary permissions only when they need them and for.
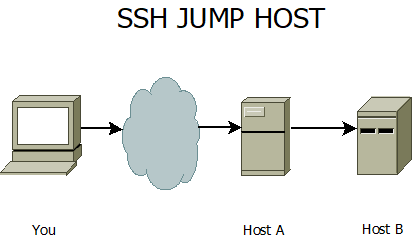
Jump Host Ssh Computer How To
Comments are closed.