Ssh Protocol Secure Shell Dataflair

Ssh Secure Shell Protocol And Software Data Protection Internet And Ssh (secure shell) is a network protocol that establishes encrypted connections between computers for secure remote access. it operates on tcp port 22 and provides authentication, encryption, and integrity to protect data transmitted over unsecured networks. The secure shell protocol (ssh protocol) is a cryptographic network protocol for operating network services securely over an unsecured network. [1] its most notable applications are remote login and command line execution.
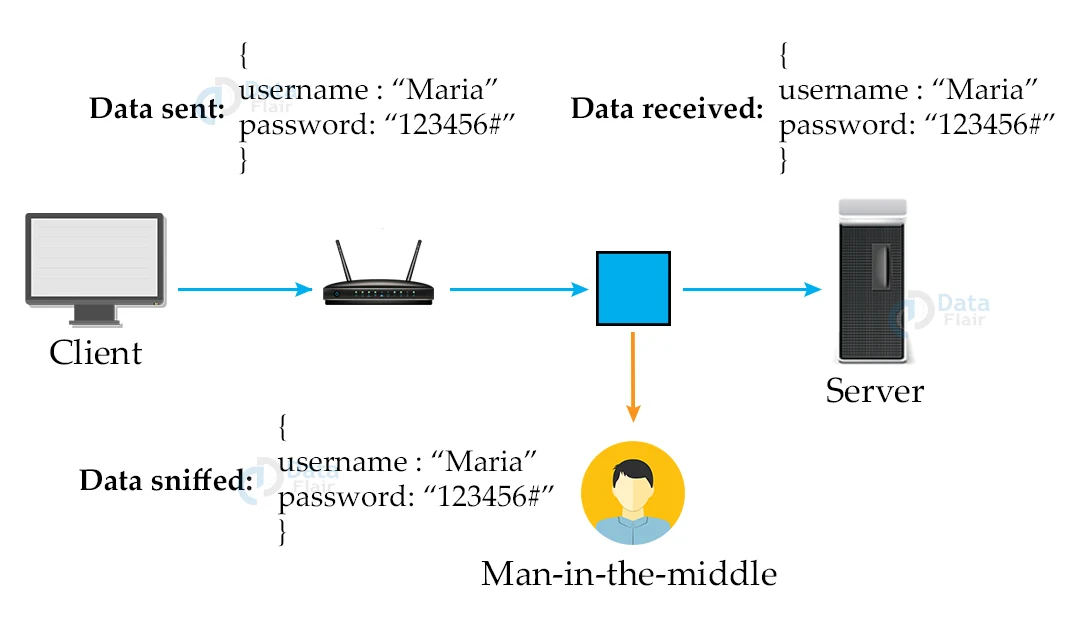
Ssh Protocol Secure Shell Dataflair In this guide, we will discuss seven critical ssh best practices you should apply to make ssh connections to your servers more secure. but before that, let’s take a quick look at the. What is the secure shell key? secure shell or ssh, is a protocol that allows you to connect securely to another computer over an unsecured network. it developed in 1995. ssh was designed to replace older methods like telnet, which transmitted data in plain text. The ssh protocol (also referred to as secure shell) is a method for secure remote login from one computer to another. it provides several alternative options for strong authentication, and it protects communications security and integrity with strong encryption. Abstract secure shell (ssh) is a protocol for secure remote login and other secure network services over an insecure network. this document describes the ssh connection protocol. it provides interactive login sessions, remote execution of commands, forwarded tcp ip connections, and forwarded x11 connections. all of these.

Ssh Protocol Secure Shell Dataflair The ssh protocol (also referred to as secure shell) is a method for secure remote login from one computer to another. it provides several alternative options for strong authentication, and it protects communications security and integrity with strong encryption. Abstract secure shell (ssh) is a protocol for secure remote login and other secure network services over an insecure network. this document describes the ssh connection protocol. it provides interactive login sessions, remote execution of commands, forwarded tcp ip connections, and forwarded x11 connections. all of these. The ssh connection protocol runs on top of the ssh transport layer protocol and assumes that a secure authentication connection is in use. that secure authentication connection, referred to as a tunnel, is used by the connection protocol to multiplex a number of logical channels. Secure shell (ssh) is a protocol for secure remote login and other secure network services over an insecure network. it replaces older protocols like telnet or rlogin. Port forwarding or ssh tunneling is one of the most useful features of ssh. using port forwarding one can convert any insecure tcp connection into a secure ssh connection.
Comments are closed.