Ssh Client Proxy Sessions
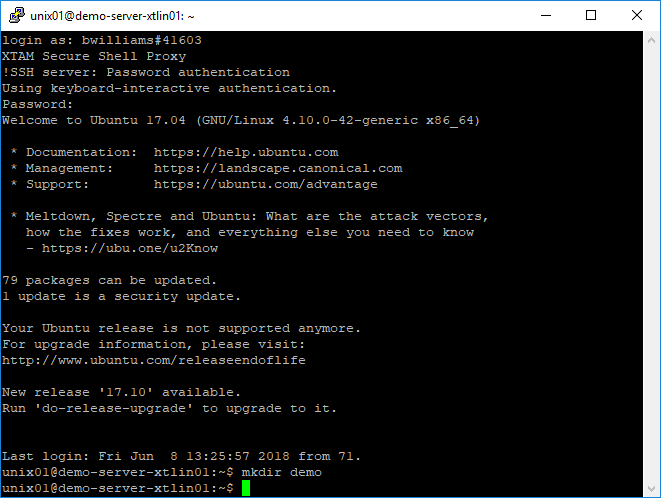
Ssh Client Proxy Sessions Squid is a web proxy, and it's telling you it doesn't know how to do ssh. you just proxy ssh connections through an ssh server instead, for example through a bastion host. Using a proxy with ssh allows you to access remote hosts that are behind firewalls or nat. this method routes your connection through a socks or https proxy server, which can help you bypass network restrictions. it is a practical solution for secure access to private networks without using a vpn.
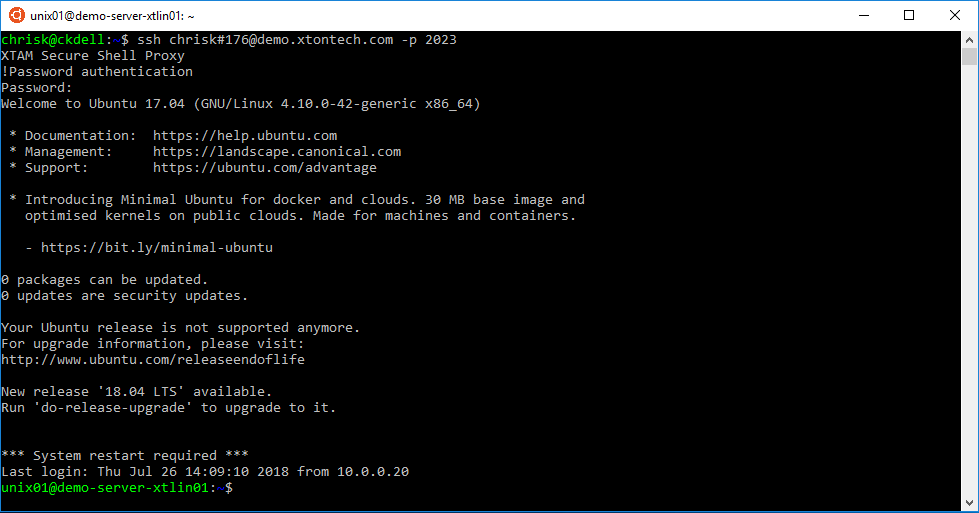
Ssh Client Proxy Sessions Navigate to admin > ssh proxy, and select the endpoints tab. in the nodes section, for each node you wish to be a proxy, click edit and configure the ssh public hostname or ip (must be an ip address, not a dns name) and the ssh bind ip address (use 0.0.0.0 to easily bind to all ipv4 ps on a server). Yet in some places the connection is restricted behind an http proxy that won’t let ssh do its magic. fortunately, it’s still possible to configure ssh for these cases and here we’ll be covering such a scenario. You need an ssh client that can issue connect requests through the company http proxy. if you're on windows, using putty is fine as it has built in support for tunneling through a http proxy. Configure ssh and rdp proxy connections in the password safe web portal, requesters can request access to use ssh or rdp remote connections. to permit remote connections, you must configure an access policy. the following section provides additional information on setting up ssh or rdp connections.
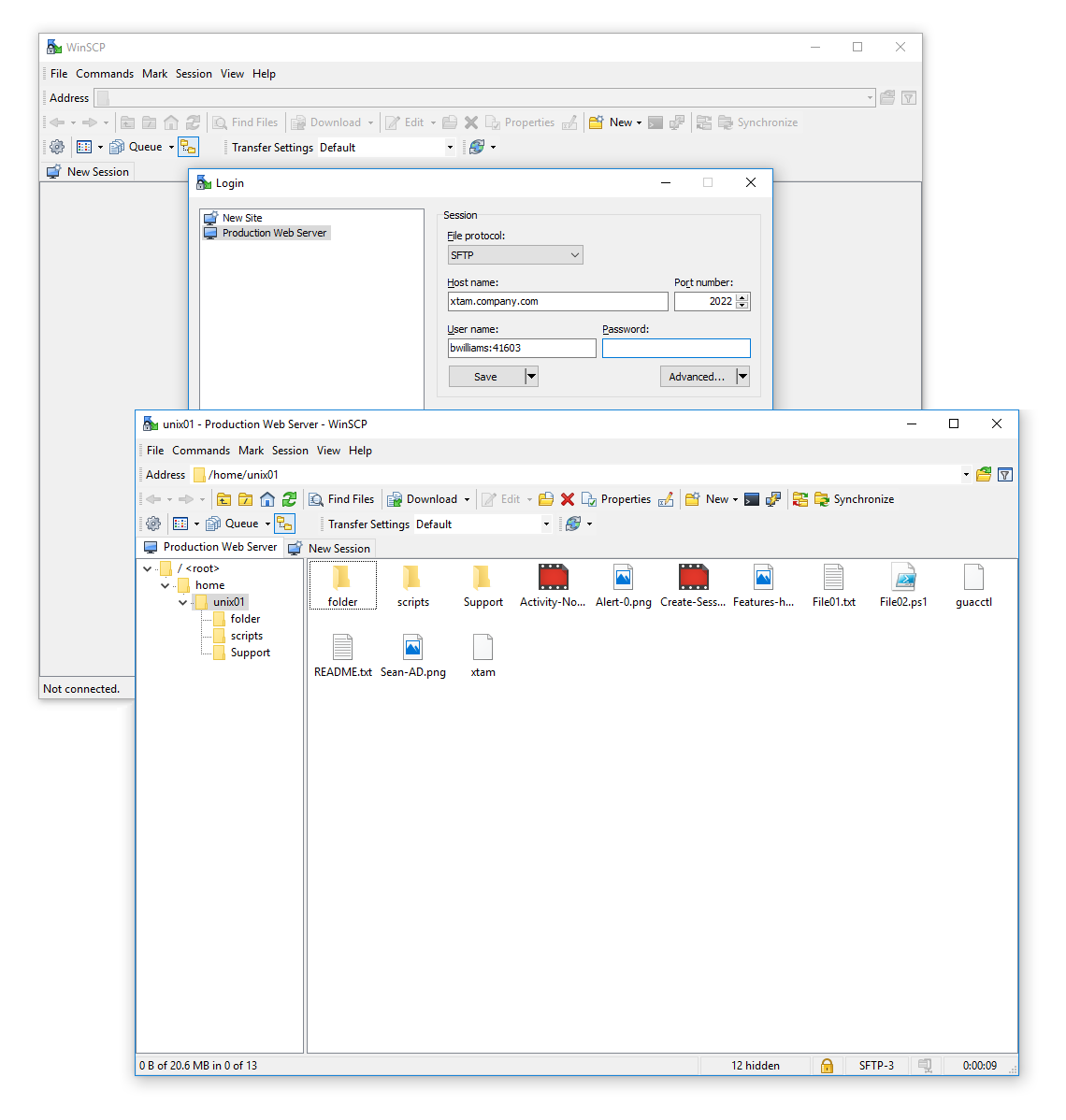
Ssh Client Proxy Sessions You need an ssh client that can issue connect requests through the company http proxy. if you're on windows, using putty is fine as it has built in support for tunneling through a http proxy. Configure ssh and rdp proxy connections in the password safe web portal, requesters can request access to use ssh or rdp remote connections. to permit remote connections, you must configure an access policy. the following section provides additional information on setting up ssh or rdp connections. Learn how to use ssh proxycommand to proxy an ssh connection using a configuration file. configure hosts using the target's id or domain. Recommendations for an ssh proxy with session recording so currently i have a client which is looking to get ready for the new pci v4 requirements and they are currently using freeipa and a regular bastion server to ssh into their servers. A simple and effective solution is to use a reverse proxy over https to tunnel your ssh connection. in this guide, i’ll walk you through setting up this method using nginx and ssl, ensuring secure and reliable access to your server. In an ssh proxy configuration, a next generation firewall (ngfw) sits between a client and a server. configuring ssh proxy enables an ngfw to decrypt inbound and outbound ssh connections, preventing attackers from using the ssh protocol to tunnel unwanted applications and content.
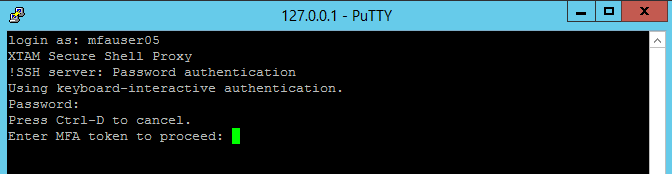
Ssh Client Proxy Sessions Learn how to use ssh proxycommand to proxy an ssh connection using a configuration file. configure hosts using the target's id or domain. Recommendations for an ssh proxy with session recording so currently i have a client which is looking to get ready for the new pci v4 requirements and they are currently using freeipa and a regular bastion server to ssh into their servers. A simple and effective solution is to use a reverse proxy over https to tunnel your ssh connection. in this guide, i’ll walk you through setting up this method using nginx and ssl, ensuring secure and reliable access to your server. In an ssh proxy configuration, a next generation firewall (ngfw) sits between a client and a server. configuring ssh proxy enables an ngfw to decrypt inbound and outbound ssh connections, preventing attackers from using the ssh protocol to tunnel unwanted applications and content.
Ssh Client Proxy Sessions A simple and effective solution is to use a reverse proxy over https to tunnel your ssh connection. in this guide, i’ll walk you through setting up this method using nginx and ssl, ensuring secure and reliable access to your server. In an ssh proxy configuration, a next generation firewall (ngfw) sits between a client and a server. configuring ssh proxy enables an ngfw to decrypt inbound and outbound ssh connections, preventing attackers from using the ssh protocol to tunnel unwanted applications and content.
Comments are closed.