Solved Needs Grading What Is The Output Of The Aes Subbytes Chegg
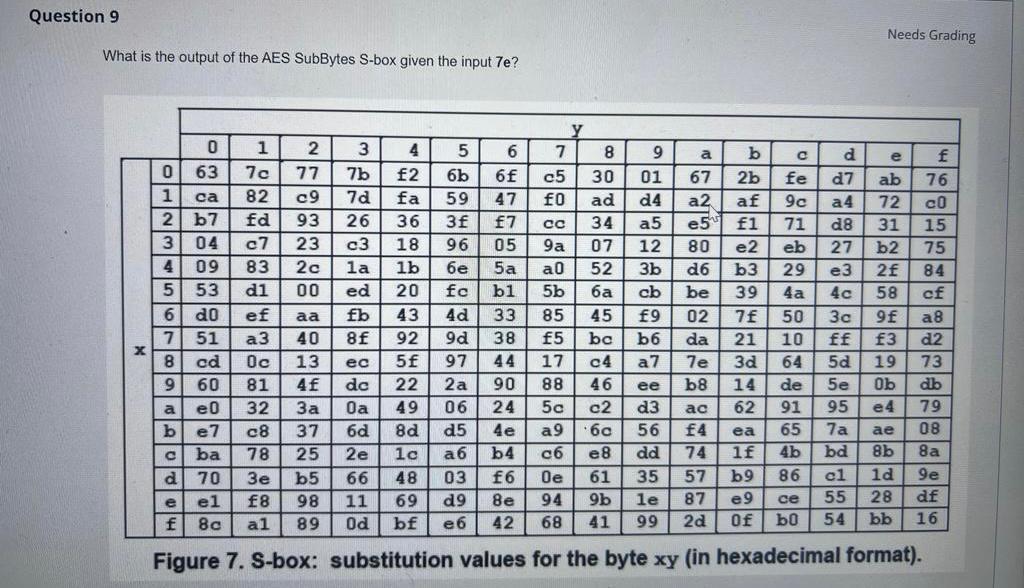
Solved Needs Grading What Is The Output Of The Aes Subbytes Chegg Question: needs grading what is the output of the aes subbytes s box given the input 7e? figure 7. s box: substitution values for the byte xy (in hexadecimal format). there are 2 steps to solve this one. To review the overall structure of aes and to focus particularly on the four steps used in each round of aes: (1) byte substitution, (2) shift rows, (3) mix columns, and (4) add round key.
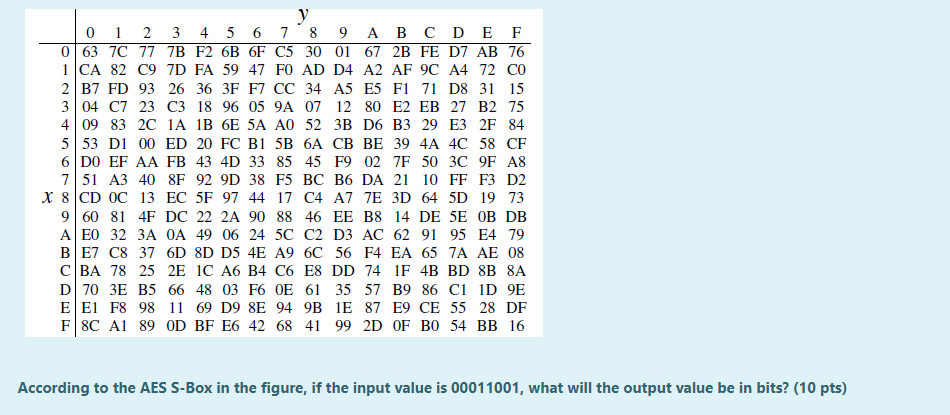
Solved According To The Aes S Box In The Figure If The Chegg During the subbytes transformation, each byte in the state matrix is changed to match a byte from the s box. every byte in the state matrix is replaced individually, resulting in the creation of a new state matrix. Unlike des, aes uses the same s box for all bytes. the aes s box implements inverse multiplication in galois field 28. here, each byte of our key is passed through the subbyte and a new output is being generated. this operation provides the non linearity in the cipher. How to solve aes sub bytes transformation | sub bytes in aes | sub bytes transformation in aes | solved example | aes sub bytes | aes sub bytes solved example |. In this lecture we will look at the basic stages of aes encryption. the basic stages are given next. with aes we have blocks of 16 bytes (128 bits) and with key sizes of 16, 24, 32 bytes. we go through a number of processes and where we operate on 16 bytes as an input and output.
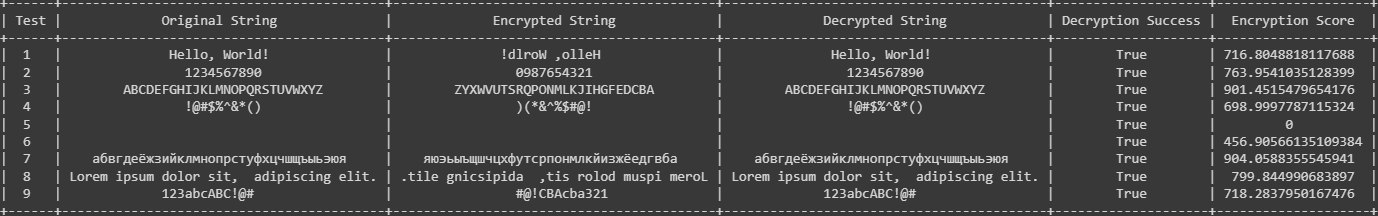
Solved For This Output I Am Using This Aes Algorithm Given Chegg How to solve aes sub bytes transformation | sub bytes in aes | sub bytes transformation in aes | solved example | aes sub bytes | aes sub bytes solved example |. In this lecture we will look at the basic stages of aes encryption. the basic stages are given next. with aes we have blocks of 16 bytes (128 bits) and with key sizes of 16, 24, 32 bytes. we go through a number of processes and where we operate on 16 bytes as an input and output. The subbytes transformation is integral to aes’s defense against linear cryptanalysis and algebraic attacks. by applying a non linear substitution using an s box, it injects confusion into the cipher, which is essential for secure symmetric encryption. To determine the subbytes value for an element in the input state, take the hexadecimal value of the element, split it into two halves to get the row and column indices, and use these indices to look up the corresponding value from the subbytes transformation table. Summary aes encrypts 128 bit blocks with 128 bit, 192 bit or 256 bit keys using 10, 12, or 14 rounds, respectively. is not a feistel cipher all 128 bits are encrypted each round = 4 steps of subbytes, shiftrows, mixcolumns, and addroundkey. last round has only 3 steps. no mixcolumns. Problem 45211. aes subbytes () transformation. given a 16x2 input character hexadecimal array representing the aes state, execute the aes algorithm subbytes () transformation and output a 16x2 character hexadecimal array. refer to this link: csrc.nist.gov csrc media publications fips 197 final documents fips 197.pdf. for example:.
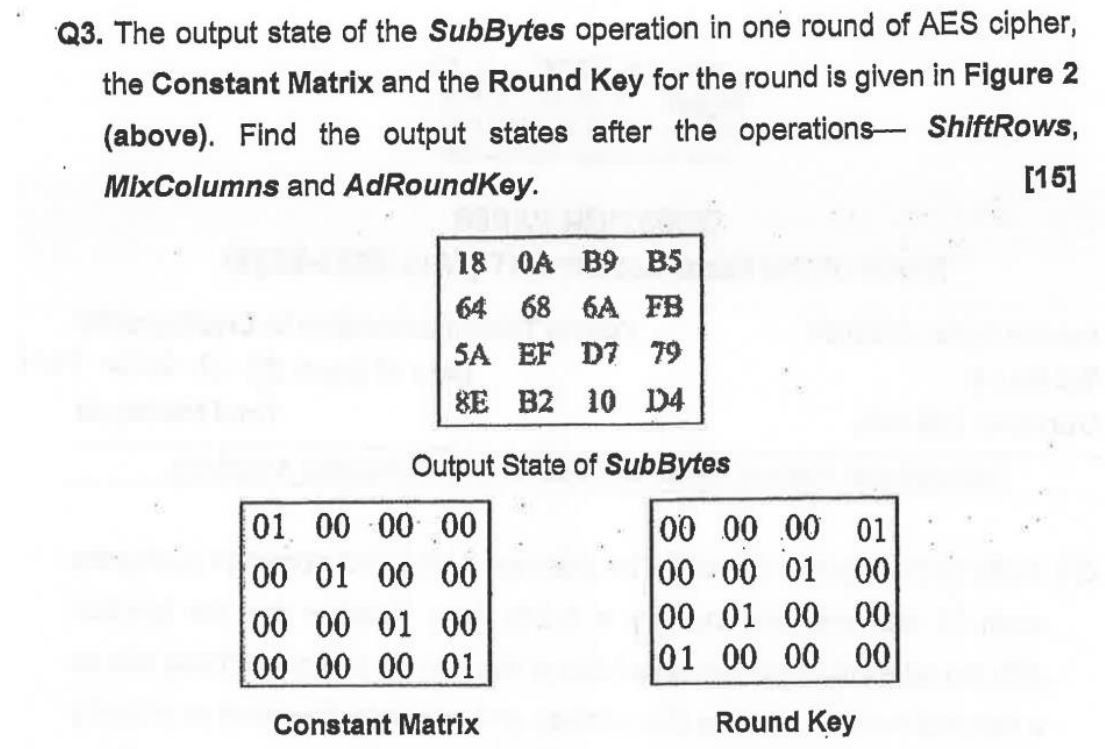
Solved Q3 The Output State Of The Subbytes Operation In One Chegg The subbytes transformation is integral to aes’s defense against linear cryptanalysis and algebraic attacks. by applying a non linear substitution using an s box, it injects confusion into the cipher, which is essential for secure symmetric encryption. To determine the subbytes value for an element in the input state, take the hexadecimal value of the element, split it into two halves to get the row and column indices, and use these indices to look up the corresponding value from the subbytes transformation table. Summary aes encrypts 128 bit blocks with 128 bit, 192 bit or 256 bit keys using 10, 12, or 14 rounds, respectively. is not a feistel cipher all 128 bits are encrypted each round = 4 steps of subbytes, shiftrows, mixcolumns, and addroundkey. last round has only 3 steps. no mixcolumns. Problem 45211. aes subbytes () transformation. given a 16x2 input character hexadecimal array representing the aes state, execute the aes algorithm subbytes () transformation and output a 16x2 character hexadecimal array. refer to this link: csrc.nist.gov csrc media publications fips 197 final documents fips 197.pdf. for example:.
Comments are closed.