Solved Hacking With Google Google Hacking Also Known As Chegg

Solved Hacking With Google Google Hacking Also Known As Chegg Our expert help has broken down your problem into an easy to learn solution you can count on. question: hacking with google google hacking, also known as google dorking, is an information gathering technique used by leveraging the advanced google search techniques. Google hacking, also known as "google dorking", is the technique of using advanced search operators on google and other search engines to locate hard to find pages, vulnerable systems, and exposed sensitive data on websites.

Solved Hacking With Google Google Hacking Also Known As Chegg To start with, you should understand what google hacking, also known as google dorking, involves using advanced search operators and queries in search engines to uncover hidden or unintended information on web. Google has confirmed it has been hacked — but what user information was compromised? here's what you need to know. In this article, we’ll delve into how google hacking techniques work, their applications, and the major search operators used to find specific content such as login pages, sensitive files, and error messages. Google hacking involves using advanced operators in the google search engine to locate specific strings of text within search results. some of the more popular examples are finding specific versions of vulnerable web applications. the following search query would locate all web pages that have that particular text contained within them.
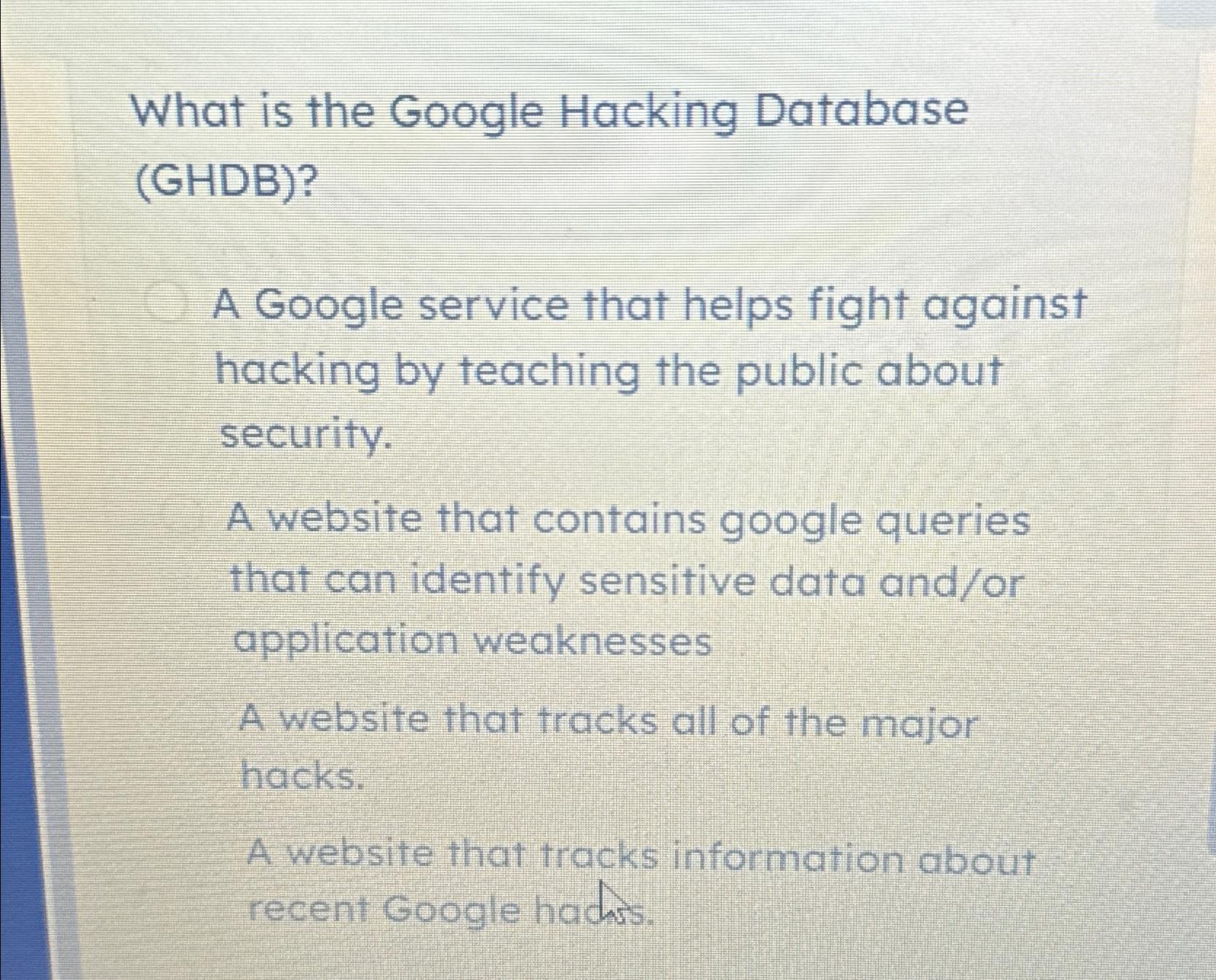
Solved What Is The Google Hacking Database Ghdb A Google Chegg In this article, we’ll delve into how google hacking techniques work, their applications, and the major search operators used to find specific content such as login pages, sensitive files, and error messages. Google hacking involves using advanced operators in the google search engine to locate specific strings of text within search results. some of the more popular examples are finding specific versions of vulnerable web applications. the following search query would locate all web pages that have that particular text contained within them. What is google hacking? google hacking is the term used when a hacker tries to find vulnerable targets or sensitive data by using the google search engine. in google hacking hackers use search engine commands or complex search queries to locate sensitive data and vulnerable devices on the internet. This comprehensive guide will explore what ghdb is, how google dorking works, its ethical and legal implications, how attackers misuse it, and how to protect your website from google based reconnaissance attacks. The term this practice has become known by is google hacking. google hacking involves manipulating a search string with additional specific operators to search for vulnerabilities. Learn how ethical hackers use advanced google search techniques to uncover vulnerabilities and secure sensitive data. google isn’t just for finding recipes or binge worthy netflix shows .

Solved Course Ethical Hacking Please Do Not Copy Paste Chegg What is google hacking? google hacking is the term used when a hacker tries to find vulnerable targets or sensitive data by using the google search engine. in google hacking hackers use search engine commands or complex search queries to locate sensitive data and vulnerable devices on the internet. This comprehensive guide will explore what ghdb is, how google dorking works, its ethical and legal implications, how attackers misuse it, and how to protect your website from google based reconnaissance attacks. The term this practice has become known by is google hacking. google hacking involves manipulating a search string with additional specific operators to search for vulnerabilities. Learn how ethical hackers use advanced google search techniques to uncover vulnerabilities and secure sensitive data. google isn’t just for finding recipes or binge worthy netflix shows .
Comments are closed.