Solved A Perform Aes Subbytes Transformation On The Matrix Chegg
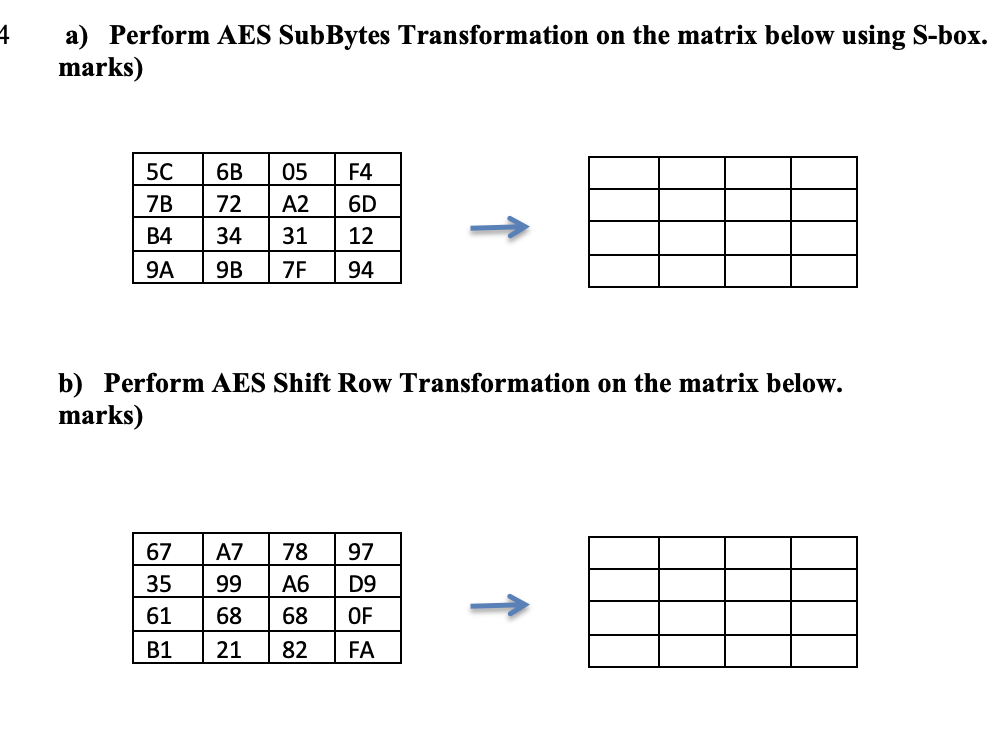
Solved A Perform Aes Subbytes Transformation On The Matrix Chegg There are 2 steps to solve this one. aes subbyt a) perform aes subbytes transformation on the matrix below using s box. marks) b) perform aes shift row transformation on the matrix below. marks) not the question you’re looking for? post any question and get expert help quickly. How to solve aes sub bytes transformation | sub bytes in aes | sub bytes transformation in aes | solved example | aes sub bytes | aes sub bytes solved example |.
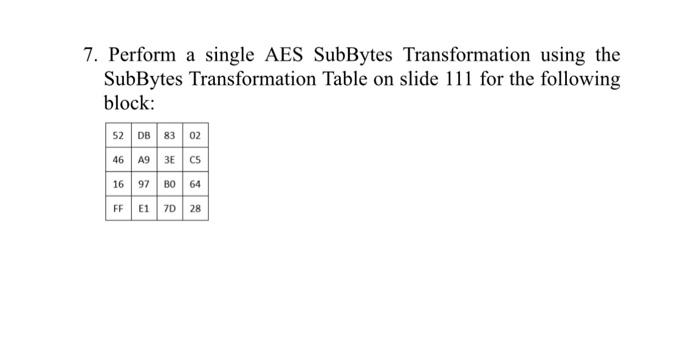
Solved Perform A Single Aes Subbytes Transformation Using Chegg Subword: subbytes fn is applied to all four bytes. (diffusion) for aes 192 and aes 256, the key expansion is more complex. aes encrypts 128 bit blocks with 128 bit, 192 bit or 256 bit keys using 10, 12, or 14 rounds, respectively. each round = 4 steps of subbytes, shiftrows, mixcolumns, and addroundkey. last round has only 3 steps. Applying the transformation: for each byte in the input block, we use the first hexadecimal digit as the row index and the second hexadecimal digit as the column index to find the corresponding value in the s box. During the subbytes transformation, each byte in the state matrix is changed to match a byte from the s box. every byte in the state matrix is replaced individually, resulting in the creation of a new state matrix. Aes subbytes () transformation. given a 16x2 input character hexadecimal array representing the aes state, execute the aes algorithm subbytes () transformation and output a 16x2 character hexadecimal array. refer to this link: csrc.nist.gov csrc media publications fips 197 final documents fips 197.pdf. for example: link is not working.

Solved The Mix Column Transformation Of Aes Consists Of Chegg During the subbytes transformation, each byte in the state matrix is changed to match a byte from the s box. every byte in the state matrix is replaced individually, resulting in the creation of a new state matrix. Aes subbytes () transformation. given a 16x2 input character hexadecimal array representing the aes state, execute the aes algorithm subbytes () transformation and output a 16x2 character hexadecimal array. refer to this link: csrc.nist.gov csrc media publications fips 197 final documents fips 197.pdf. for example: link is not working. Perform all aes steps for one round of encryption: 1 construct the state matrix. Let's go through a couple of concrete examples where we apply the aes subbytes transformation to small arrays of plaintext using the s box substitution table. this will demonstrate the process and give you a clear understanding of how it works. As you can see, there are fou r operations in the aes, i.e., subbytes, shiftrows,. The final round of the aes encryption algorithm includes the subbytes, shiftrows, and addroundkey steps. notably, the mixcolumns step is omitted in the final round to complete the series of transformations, resulting in the final encrypted data known as ciphertext.

The Invmixcolumns Transformation Of Aes Consists Of A Chegg Perform all aes steps for one round of encryption: 1 construct the state matrix. Let's go through a couple of concrete examples where we apply the aes subbytes transformation to small arrays of plaintext using the s box substitution table. this will demonstrate the process and give you a clear understanding of how it works. As you can see, there are fou r operations in the aes, i.e., subbytes, shiftrows,. The final round of the aes encryption algorithm includes the subbytes, shiftrows, and addroundkey steps. notably, the mixcolumns step is omitted in the final round to complete the series of transformations, resulting in the final encrypted data known as ciphertext.
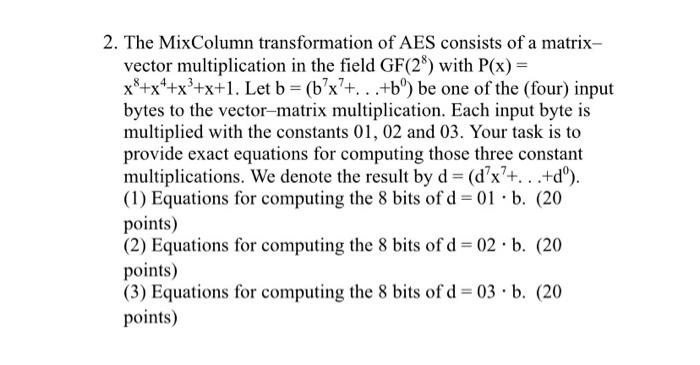
Solved 2 The Mixcolumn Transformation Of Aes Consists Of A Chegg As you can see, there are fou r operations in the aes, i.e., subbytes, shiftrows,. The final round of the aes encryption algorithm includes the subbytes, shiftrows, and addroundkey steps. notably, the mixcolumns step is omitted in the final round to complete the series of transformations, resulting in the final encrypted data known as ciphertext.
Comments are closed.