Securing Your Apps With Public Key Cryptography Digital Signature

Securing Your Apps With Public Key Cryptography Digital Signature This article provides some basic information about the security mechanisms behind public key cryptography with practical details on how it is used by some of the popular tools like pgp, ssl as well as digital signature. This document describes the proper way to use android's cryptographic facilities and includes some examples of their use. if your app requires greater key security, use the android keystore system. note: except where specified, this advice applies to all android versions.

Securing Your Apps With Public Key Cryptography Digital Signature In this project, we illustrate the basics of public key cryptography by building a simple react application that allows us to use a private key (never do this in practice) to look up user. Securing an embedded system is incredibly important, and having a digital signature plays a crucial role in that. a digital signature confirms that a specific piece of information came from a specific organization (i.e. the one with the private key as described below) and has not been modified. Explore the various applications of public key cryptography in ensuring information security, including secure communication, digital signatures, and authentication. In asymmetric encryption, a public key and a private key are used. the sender's private key encrypts the data this is the digital signature and the receiver uses the public key to decrypt it and verify it matches the attachment.

Securing Your Apps With Public Key Cryptography Digital Signature Explore the various applications of public key cryptography in ensuring information security, including secure communication, digital signatures, and authentication. In asymmetric encryption, a public key and a private key are used. the sender's private key encrypts the data this is the digital signature and the receiver uses the public key to decrypt it and verify it matches the attachment. Learn how microsoft's digital signature, asymmetric encryption, cybersecurity, and public key work together to safeguard your digital presence. Digital signatures and certificates are two key technologies that play an important role in ensuring the security and authenticity of online activities. they are essential for activities such as online banking, secure email communication, software distribution, and electronic document signing. Learn how to implement public key cryptography in ios using cryptokit. this guide covers encryption, digital signatures, and secure key exchange to protect sensitive data in our swift apps. Public key infrastructure (pki) stands as a comprehensive framework designed to secure communications across the internet. it hinges on three fundamental components: digital certificates, public and private keys, and trusted third parties. imagine pki as the digital equivalent of a passport system.
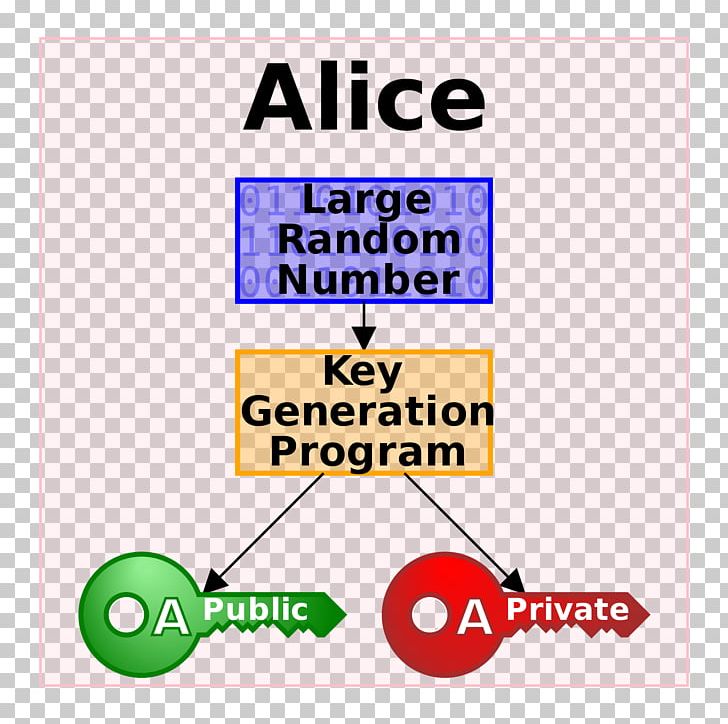
Public Key Cryptography Digital Signature Encryption Png Clipart Learn how microsoft's digital signature, asymmetric encryption, cybersecurity, and public key work together to safeguard your digital presence. Digital signatures and certificates are two key technologies that play an important role in ensuring the security and authenticity of online activities. they are essential for activities such as online banking, secure email communication, software distribution, and electronic document signing. Learn how to implement public key cryptography in ios using cryptokit. this guide covers encryption, digital signatures, and secure key exchange to protect sensitive data in our swift apps. Public key infrastructure (pki) stands as a comprehensive framework designed to secure communications across the internet. it hinges on three fundamental components: digital certificates, public and private keys, and trusted third parties. imagine pki as the digital equivalent of a passport system.
Comments are closed.