Securing Data Using Password Hashing And Data Encryption Jcharistech

Hashing Pdf Security Engineering Computer Programming Hashing involves a one way functional approach to data protection. that means you cannot un hash once you have hashed a plaintext. the main purpose of hashing is to ensure data integrity and well as to verify data to make sure they are the same. In this tutorial we will explore libraries used to secure passwords and encrypt data in python using hashlib,passlib,cryptography,etc.udemy course : building.
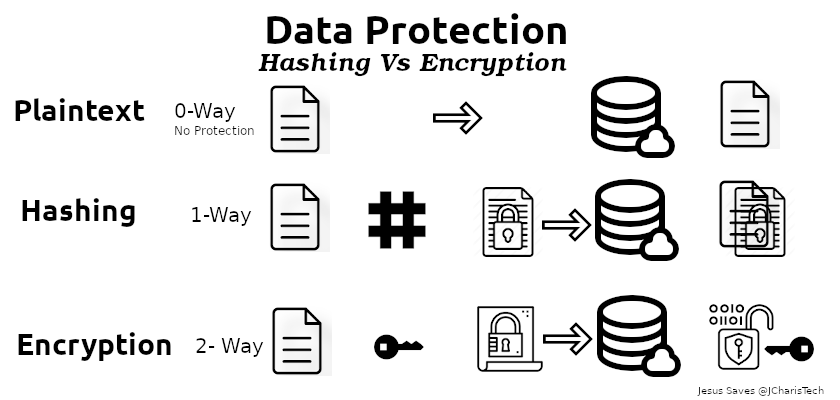
Securing Data Using Password Hashing And Data Encryption Jcharistech Password hashing is a password protection method that converts a plaintext password into a string of random characters. hashing is a one way process, meaning it’s irreversible: once a password has been hashed, you can’t access, interpret, or reverse engineer the original text. Hashing and encryption can keep sensitive data safe, but in almost all circumstances, passwords should be hashed, not encrypted. because hashing is a one way function (i.e., it is impossible to "decrypt" a hash and obtain the original plaintext value), it is the most appropriate approach for password validation. Two key techniques at the forefront of data security are hashing and encryption. while they both serve to protect data, their applications, especially in the context of password management, are distinct. let’s see when each should be used and why. hashing key characteristics: common…. In this blog, we’ll explore how encryption protects your passwords, break down other cryptographic concepts, like hashing and salting, and explain how enterprise tools like beyondtrust password safe can help your organization stay secure, especially when it comes to managing privileged passwords.
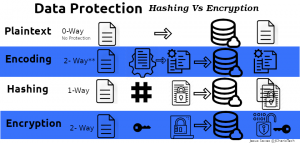
Securing Data Using Password Hashing And Data Encryption Jcharistech Two key techniques at the forefront of data security are hashing and encryption. while they both serve to protect data, their applications, especially in the context of password management, are distinct. let’s see when each should be used and why. hashing key characteristics: common…. In this blog, we’ll explore how encryption protects your passwords, break down other cryptographic concepts, like hashing and salting, and explain how enterprise tools like beyondtrust password safe can help your organization stay secure, especially when it comes to managing privileged passwords. Passwords are validated by hashing and comparing outputs. now, for most standard applications, the typical accepted practice is something as follows: the password is hashed (let’s say using argon2) and this is stored in the database (the used salt is stored as part of the argon2 hash output). Hashing is the process of converting input data (plain text) into a fixed length string of characters, called a hash value or digest, using a mathematical algorithm. a crucial property of. Password hashing algorithms are specialized mathematical functions that transform plain text passwords into unique, fixed size outputs, known as hashes, which are then stored in databases. Encryption uses a cryptographic key, which is a set of mathematical values agreed upon by both the sender and receiver of the encrypted message. just as encryption converts readable information into secure code, decryption is the process that reverses this transformation.
Securing Data Using Password Hashing And Data Encryption Jcharistech Passwords are validated by hashing and comparing outputs. now, for most standard applications, the typical accepted practice is something as follows: the password is hashed (let’s say using argon2) and this is stored in the database (the used salt is stored as part of the argon2 hash output). Hashing is the process of converting input data (plain text) into a fixed length string of characters, called a hash value or digest, using a mathematical algorithm. a crucial property of. Password hashing algorithms are specialized mathematical functions that transform plain text passwords into unique, fixed size outputs, known as hashes, which are then stored in databases. Encryption uses a cryptographic key, which is a set of mathematical values agreed upon by both the sender and receiver of the encrypted message. just as encryption converts readable information into secure code, decryption is the process that reverses this transformation.

Hashing In Data Encryption Understanding The Fundamentals Password hashing algorithms are specialized mathematical functions that transform plain text passwords into unique, fixed size outputs, known as hashes, which are then stored in databases. Encryption uses a cryptographic key, which is a set of mathematical values agreed upon by both the sender and receiver of the encrypted message. just as encryption converts readable information into secure code, decryption is the process that reverses this transformation.

Password Hashing Methods For Securing Your Ecommerce Platform
Comments are closed.