Secure Code Review Checklist Pdf Http Cookie File Transfer Protocol

Secure Code Review Checklist Pdf Http Cookie File Transfer Protocol The document provides a checklist for reviewing code security. it contains questions organized into sections on input validation, authentication and user management, authorization, session management, encryption and cryptography, exception handling, and reducing the attack surface. Applica tions. the development guide will show your project how to archi tect and build a secure application, the code review guide will tell you how to verify the security of your application’s source code, and this testing guide will show you how to verify the security of your runn.
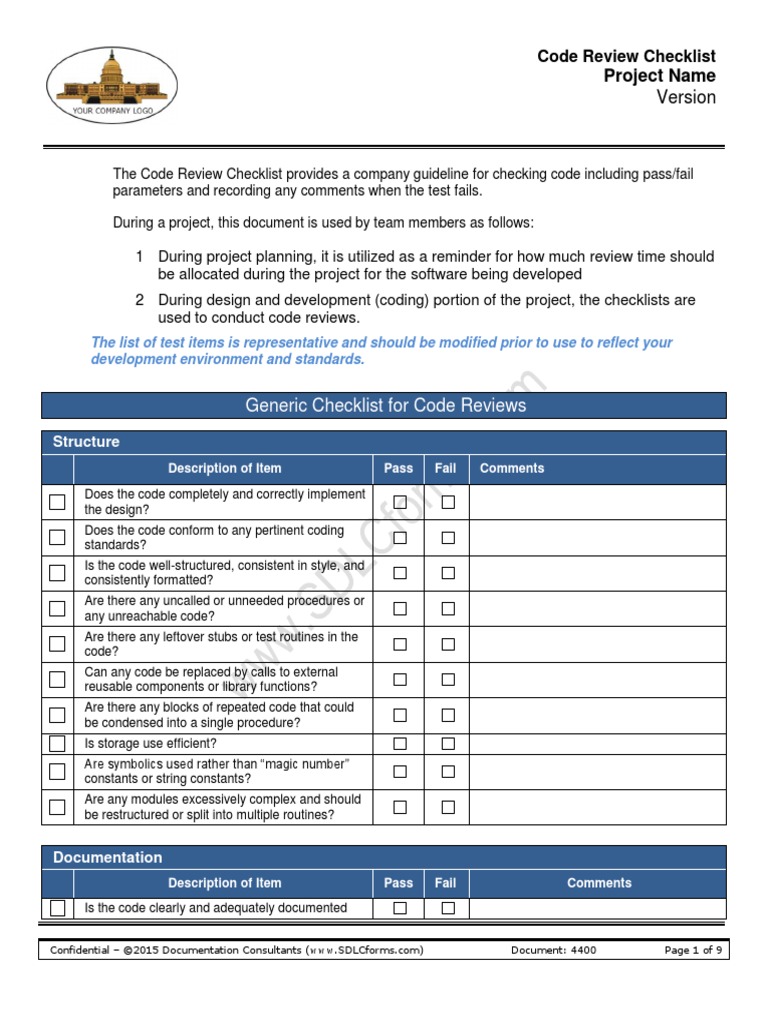
Code Review Checklist Pdf Control Flow Pointer Computer Programming A starter secure code review checklist. contribute to softwaresecured secure code review checklist development by creating an account on github. Knowledge of common programming paradigms (model view controllers) and communication protocols, such as http and ssl tls. this document details the activities performed during a secure code review. Using a secure code review checklist helps you find security vulnerabilities systematically during code review, and is a code review best practice. with this security code review checklist, you know exactly which security flaws to look for and how to implement secure coding practices. Securityboat workbook is an open source repository of knowledge cultivated through years of penetration testing and expertise contributed by security professionals at securityboat.
covering comprehensive security topics, including application, api, network, cloud, and hardware security, this workbook provides valuable insights and.
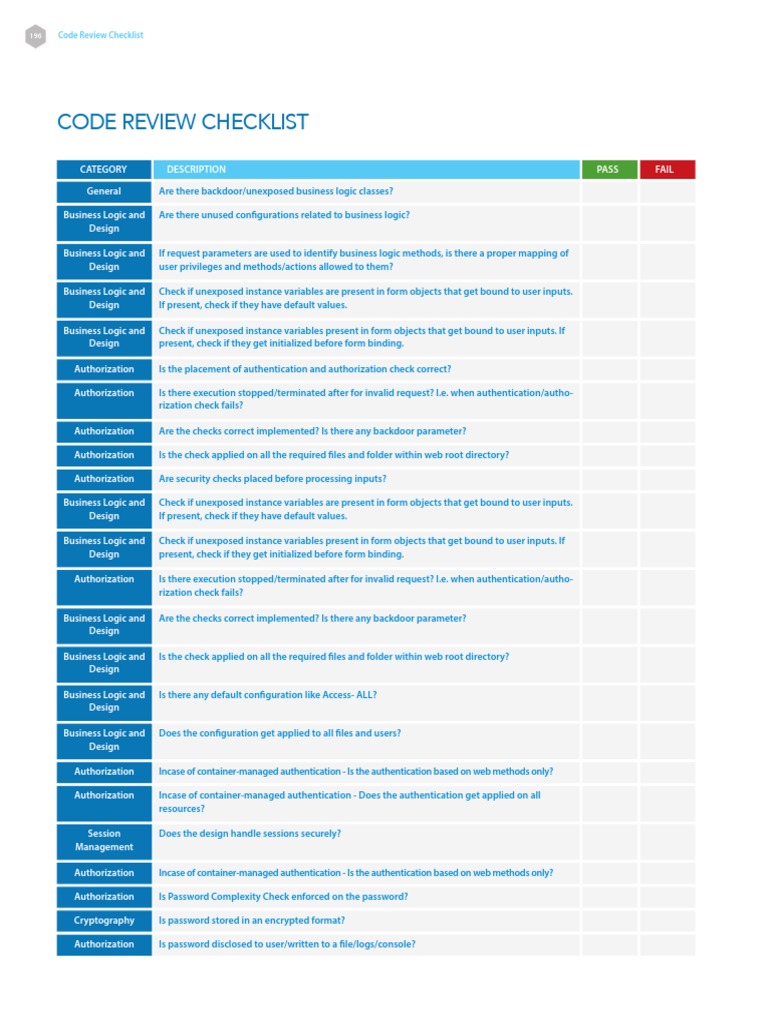
Code Review Checklist Pdf Http Cookie World Wide Web Using a secure code review checklist helps you find security vulnerabilities systematically during code review, and is a code review best practice. with this security code review checklist, you know exactly which security flaws to look for and how to implement secure coding practices. Securityboat workbook is an open source repository of knowledge cultivated through years of penetration testing and expertise contributed by security professionals at securityboat.
covering comprehensive security topics, including application, api, network, cloud, and hardware security, this workbook provides valuable insights and. Is the code easy to read and comprehend? does it make clear what the business requirements are (code is written to be read by a human, not by a computer)? are tests concise enough? are variables, functions and classes named appropriately? do the domain models cleanly map the real world to reduce cognitive load? does it use consistent coding. Secure code review identifies flaws in application features and design to help ensure that software is developed with security in mind. this is applied during merging of pull requests and checks that written code follows security and logical controls. Methodology the methodology section goes into more detail on how to integrate secure review techniques into de velopment organizations s sdlc and how the personnel reviewing the code can ensure they have the correct context to conduct an efec. Before submitting code to peers, developers should ensure their work is ready for a code review. reviewers must be able to understand why the code was written and whether the submitted code satisfies those requirements.

Cookie Compliance Checklist En Pdf Http Cookie Privacy Is the code easy to read and comprehend? does it make clear what the business requirements are (code is written to be read by a human, not by a computer)? are tests concise enough? are variables, functions and classes named appropriately? do the domain models cleanly map the real world to reduce cognitive load? does it use consistent coding. Secure code review identifies flaws in application features and design to help ensure that software is developed with security in mind. this is applied during merging of pull requests and checks that written code follows security and logical controls. Methodology the methodology section goes into more detail on how to integrate secure review techniques into de velopment organizations s sdlc and how the personnel reviewing the code can ensure they have the correct context to conduct an efec. Before submitting code to peers, developers should ensure their work is ready for a code review. reviewers must be able to understand why the code was written and whether the submitted code satisfies those requirements.

Secure Coding Checklist Pdf Coding Security Best Practices By Viraj Methodology the methodology section goes into more detail on how to integrate secure review techniques into de velopment organizations s sdlc and how the personnel reviewing the code can ensure they have the correct context to conduct an efec. Before submitting code to peers, developers should ensure their work is ready for a code review. reviewers must be able to understand why the code was written and whether the submitted code satisfies those requirements.
Github Mgreiler Secure Code Review Checklist
Comments are closed.