Rsa Keys Security Insights From Ssh Server Signing Errors

Rsa Keys Security Insights From Ssh Server Signing Errors In this article, we delve into the intricacies of rsa keys, explore the vulnerabilities discovered by these researchers, and discuss proactive measures to fortify ssh protocols against potential threats. A team of academic researchers from universities in california and massachusetts demonstrated that it's possible under certain conditions for passive network attackers to retrieve secret rsa.

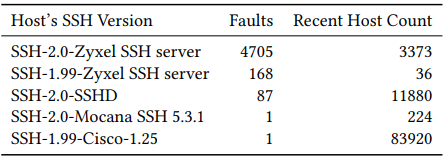
Researchers Extract Rsa Keys From Ssh Server Signing Errors Redpacket The study, which builds on previous research in tls security, demonstrates how a passive network attacker can opportunistically obtain private rsa host keys from an ssh server experiencing faults during signature computation. A paper published by the team shows that a passive network attacker can obtain a private rsa key from ssh servers that experience errors during signature computation. After researching about this error, i got to know that this is due to the recent updates from openssh which have deprecated the use of the ssh rsa signature algorithm due to security concerns related to the sha 1 hash algorithm, which ssh rsa relies on. Red hat enterprise linux 9 clients can’t connect to ssh servers that don’t support the server sig algs extension nor ecdsa hostkeys. (a, b) legacy ssh clients not supporting server sig algs extension can not connect to red hat enterprise linux 9 servers using rsa authentication keys (c, d).
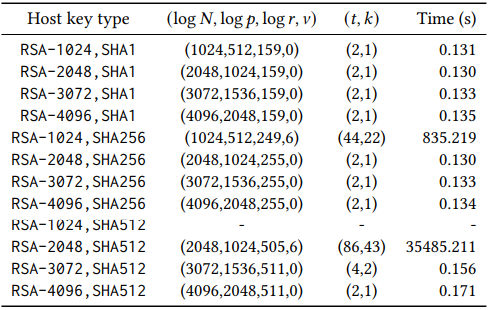
Researchers Extract Rsa Keys From Ssh Server Signing Errors Cybernoz After researching about this error, i got to know that this is due to the recent updates from openssh which have deprecated the use of the ssh rsa signature algorithm due to security concerns related to the sha 1 hash algorithm, which ssh rsa relies on. Red hat enterprise linux 9 clients can’t connect to ssh servers that don’t support the server sig algs extension nor ecdsa hostkeys. (a, b) legacy ssh clients not supporting server sig algs extension can not connect to red hat enterprise linux 9 servers using rsa authentication keys (c, d). Researchers have analyzed and found that passive network attackers can extract rsa keys from ssh servers where errors occur during signature calculation. crt rsa can reduce the size of the public key and improve decryption speed. Summary when attempting to use an ssh key generated using the ssh rsa sha 1 hash algorithm, the ssh key isn't accepted (the user receives a ' permission denied ' message), and the following message is displayed when the verbose ssh output is reviewed: debug1: send pubkey test: no mutual signature algorithm environment bitbucket data center server known operating systems impacted: fedora 33. All rsa ssh keys have the ability to use sha 1, sha 256, or sha 512. the ability to use sha 2 (that is, sha 256 or sha 512) requires three things: support from the server (which github provides), support from the client, and support from the agent (if one is being used). I'm trying to rsync backups into another machine on a lan. i've copied my key over and even using ssh manually, i get the following error, which keeps my crontabs from connecting:.
Researchers Extract Rsa Keys From Ssh Server Signing Errors Cybernoz Researchers have analyzed and found that passive network attackers can extract rsa keys from ssh servers where errors occur during signature calculation. crt rsa can reduce the size of the public key and improve decryption speed. Summary when attempting to use an ssh key generated using the ssh rsa sha 1 hash algorithm, the ssh key isn't accepted (the user receives a ' permission denied ' message), and the following message is displayed when the verbose ssh output is reviewed: debug1: send pubkey test: no mutual signature algorithm environment bitbucket data center server known operating systems impacted: fedora 33. All rsa ssh keys have the ability to use sha 1, sha 256, or sha 512. the ability to use sha 2 (that is, sha 256 or sha 512) requires three things: support from the server (which github provides), support from the client, and support from the agent (if one is being used). I'm trying to rsync backups into another machine on a lan. i've copied my key over and even using ssh manually, i get the following error, which keeps my crontabs from connecting:.
Uncovering Ssh Vulnerability Extracting Rsa Keys From Server Signing All rsa ssh keys have the ability to use sha 1, sha 256, or sha 512. the ability to use sha 2 (that is, sha 256 or sha 512) requires three things: support from the server (which github provides), support from the client, and support from the agent (if one is being used). I'm trying to rsync backups into another machine on a lan. i've copied my key over and even using ssh manually, i get the following error, which keeps my crontabs from connecting:.
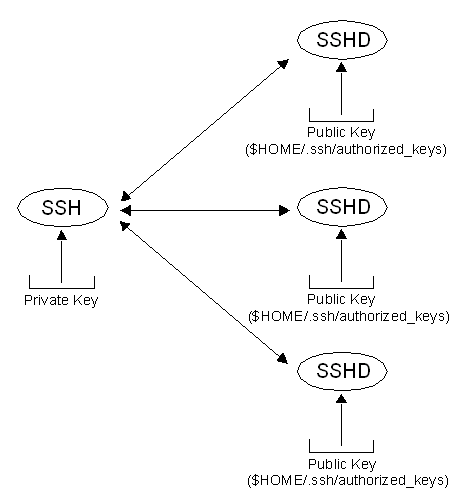
How To Generate An Rsa Based Identity For Ssh
Comments are closed.