Risks Involved In Implementing System Policies Deploying Internal
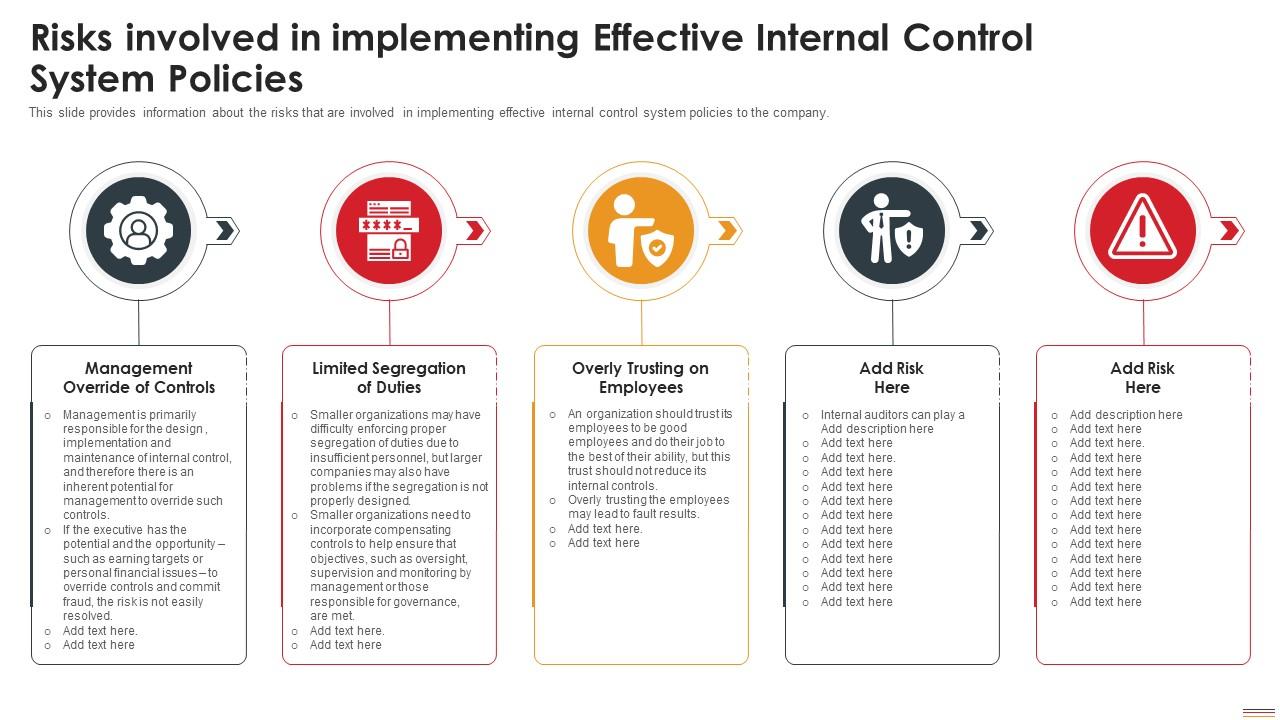
Risks Involved In Implementing System Policies Deploying Internal Risk assessments, pre implementation assessments and it risk assessments examine the project, compliance obligations, system architecture and the effects on internal controls and the business to identify potential risks and inefficiencies. Implementation risk is the potential for a development or deployment failure. in practice, the term is often used for risks related to a production launch. the following are common examples of implementation risk. a transaction between a legacy system and an erp fails in production.
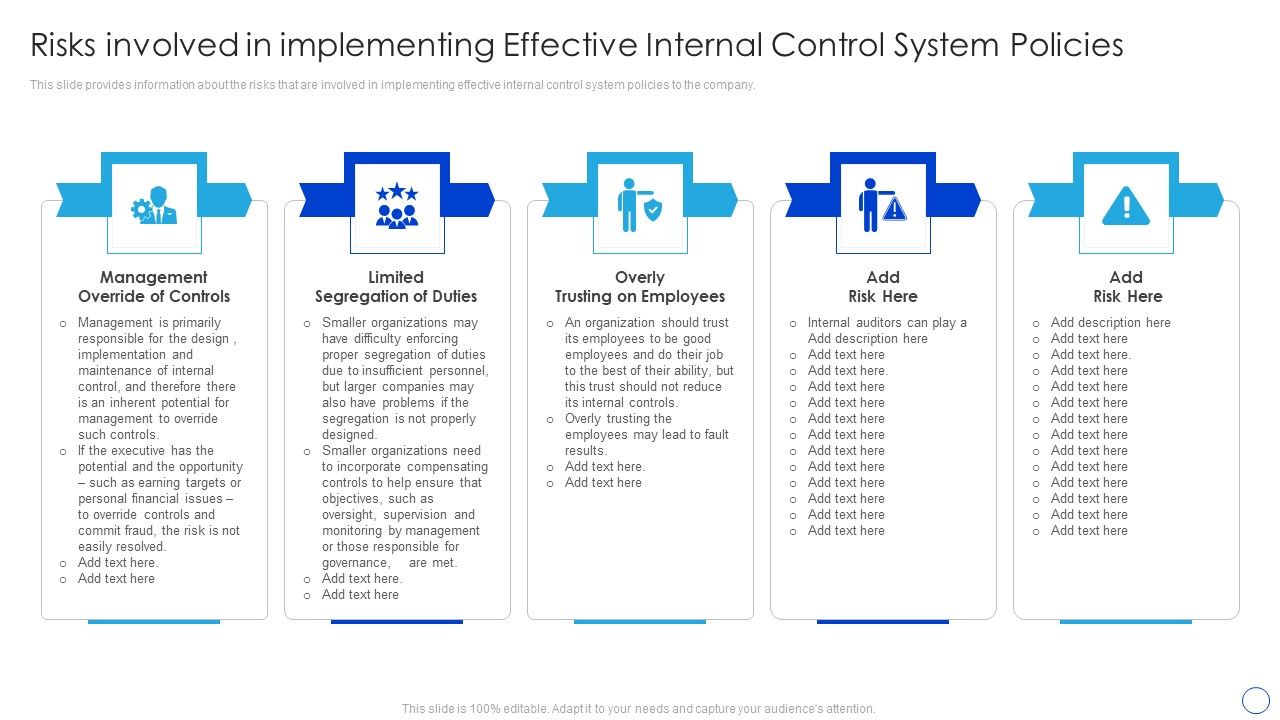
Risks Involved In Implementing Effective Internal Control System Explore the potential risks associated with implementing effective internal control system policies. understand challenges and strategies to mitigate these risks for better organizational governance. Implementing a new erp system can be a mammoth undertaking for a company of any size. the whole process can take many months, the upfront costs are significant, and there are a number of erp implementation risks that come with the territory. This article focuses on the theme of system development risks. it provides an overview of the types of risks, their causes, and how to manage them. if you want to understand system development risks and learn how to properly avoid or mitigate them, this article is for you. This should include internal and external risks, as well as any risks attached to your systems and third parties. then, organize the risks by type — like operational, financial and strategic.

Risks Involved In Implementing Effective Internal Control System This article focuses on the theme of system development risks. it provides an overview of the types of risks, their causes, and how to manage them. if you want to understand system development risks and learn how to properly avoid or mitigate them, this article is for you. This should include internal and external risks, as well as any risks attached to your systems and third parties. then, organize the risks by type — like operational, financial and strategic. Challenges to the cyber security strategy are both internal and external in nature. below we shall be touching upon the main challenges and issues. designing a cyber and or information security policy is achievable, but at times challenges arise when it comes to employees complying with the policy. Let’s review the top three information technology risks and their impact on the organization. we will also take an inventory of the top three preventive, detective, corrective, and accounting controls related to each risk. data breaches, financial losses, and reputational damage. As stated above, the deployment process is inherently risky. we’re changing a working, stable version of our application to something we don’t know will work. this can be intimidating, even if you’re a developer working and deploying code by yourself. Major changes to it systems can bring significant benefits, such as improved performance, functionality, security, or user experience. however, they can also introduce risks, such as downtime,.
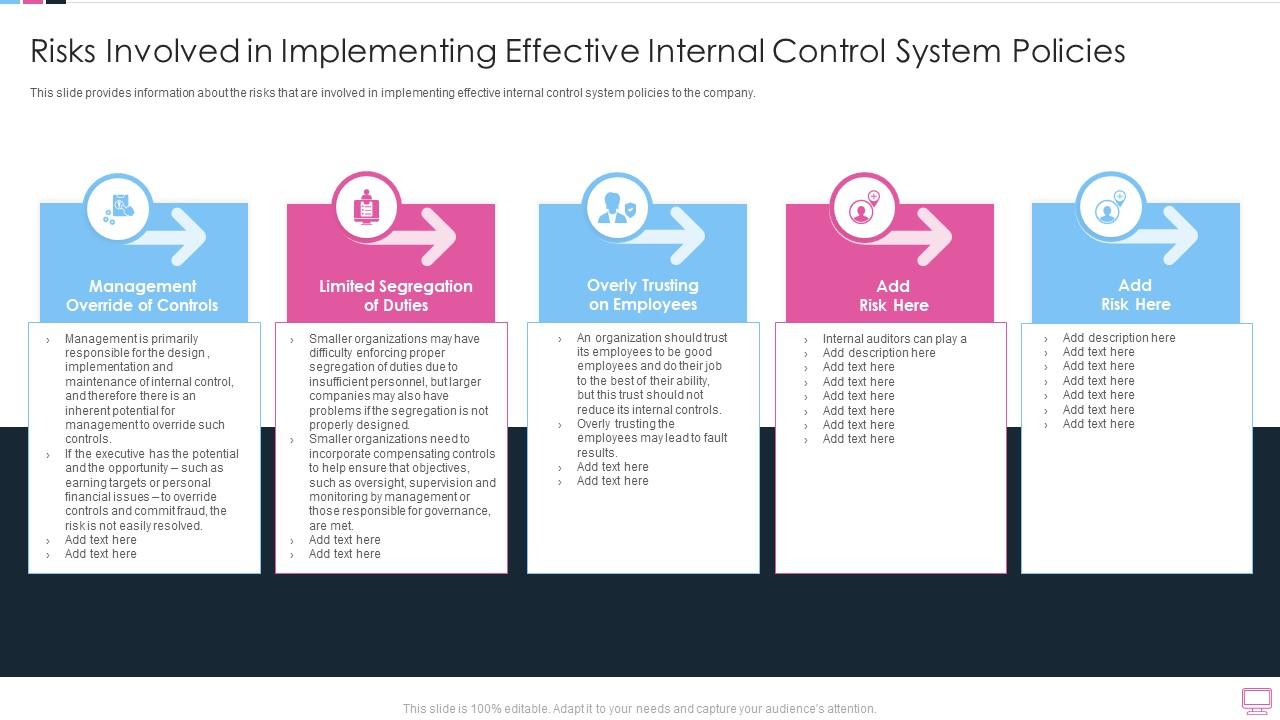
Benefits Of An Risks Involved In Implementing Effective Internal Challenges to the cyber security strategy are both internal and external in nature. below we shall be touching upon the main challenges and issues. designing a cyber and or information security policy is achievable, but at times challenges arise when it comes to employees complying with the policy. Let’s review the top three information technology risks and their impact on the organization. we will also take an inventory of the top three preventive, detective, corrective, and accounting controls related to each risk. data breaches, financial losses, and reputational damage. As stated above, the deployment process is inherently risky. we’re changing a working, stable version of our application to something we don’t know will work. this can be intimidating, even if you’re a developer working and deploying code by yourself. Major changes to it systems can bring significant benefits, such as improved performance, functionality, security, or user experience. however, they can also introduce risks, such as downtime,.

Risks Involved In Implementing Effective Internal Internal Control As stated above, the deployment process is inherently risky. we’re changing a working, stable version of our application to something we don’t know will work. this can be intimidating, even if you’re a developer working and deploying code by yourself. Major changes to it systems can bring significant benefits, such as improved performance, functionality, security, or user experience. however, they can also introduce risks, such as downtime,.

It Deployment Risks Pdf Strategic Management Strategic Planning
Comments are closed.