Reverse Eastern Secrete Convolutional Neural Network In Keras Baader

Reverse Eastern Secrete Convolutional Neural Network In Keras Baader A convolutional neural network (cnn) model represents a crucial piece of intellectual property in many applications. revealing its structure or weights would le. We provide code to build and train common rnn architectures, as well as code for understanding the dynamics of trained rnns through dynamical systems analyses. the core tools for this involve finding and analyzing approximate fixed points of the dynamics of a trained rnn.
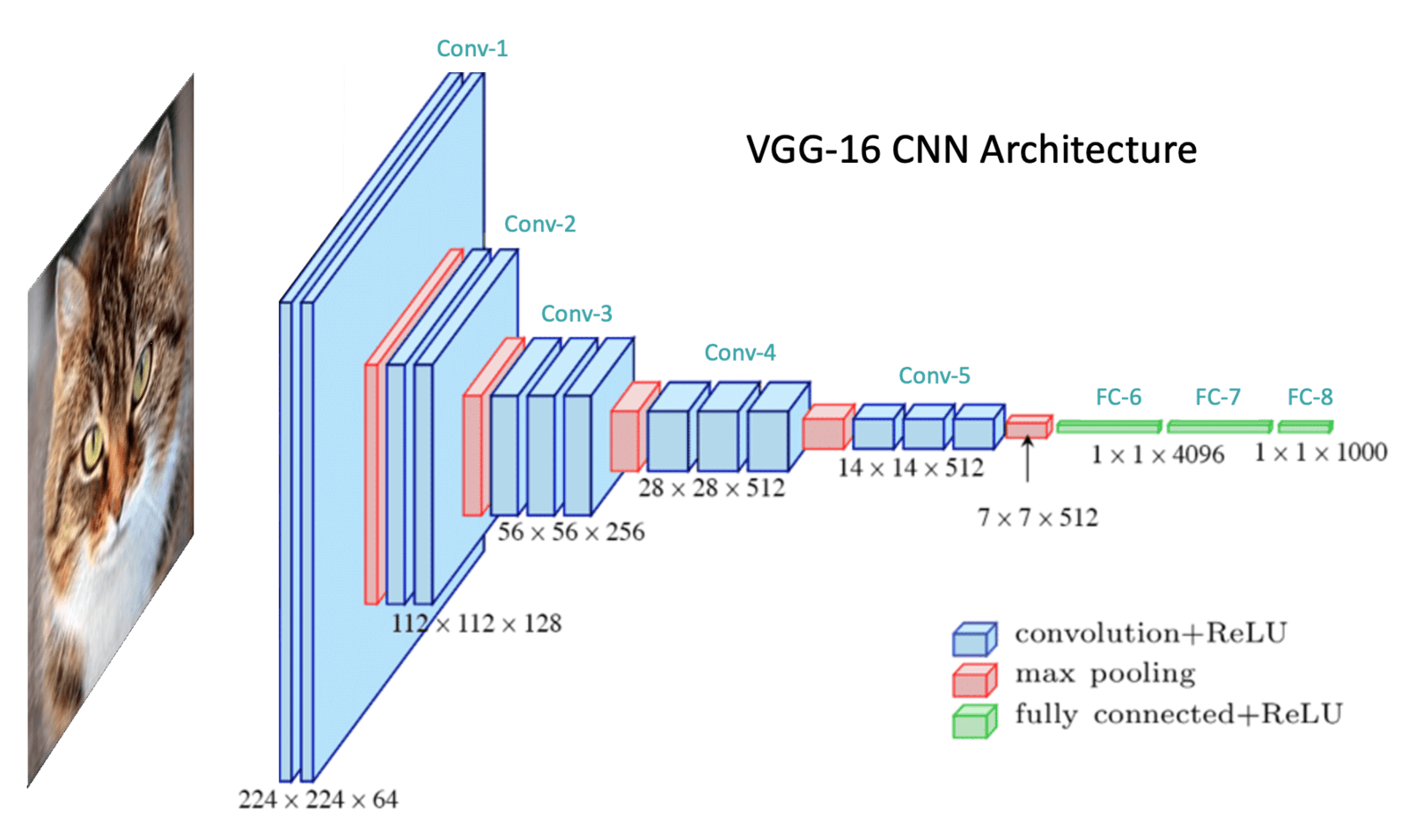
Reverse Eastern Secrete Convolutional Neural Network In Keras Baader The combination of previously developed individual techniques can thereafter result in full reverse engineering of the network. the full network recovery is performed layer by layer, and for each layer, the weights for each neuron have to be recovered one at a time. In this work, we focus on two neural network algorithms: multilayer perceptron (mlp) and convolutional neural net works (cnns). we consider feed forward neural networks and consequently, our analysis is conducted on such net works only. To fit this into the fabric of keras, i created a custom layer and called it 'recover'. it is not triggered while the model is trained, however it serves as a faux input layer for the reverse training step. Algorithm 1 summarizes the overall structure reverse engineering attack procedure.
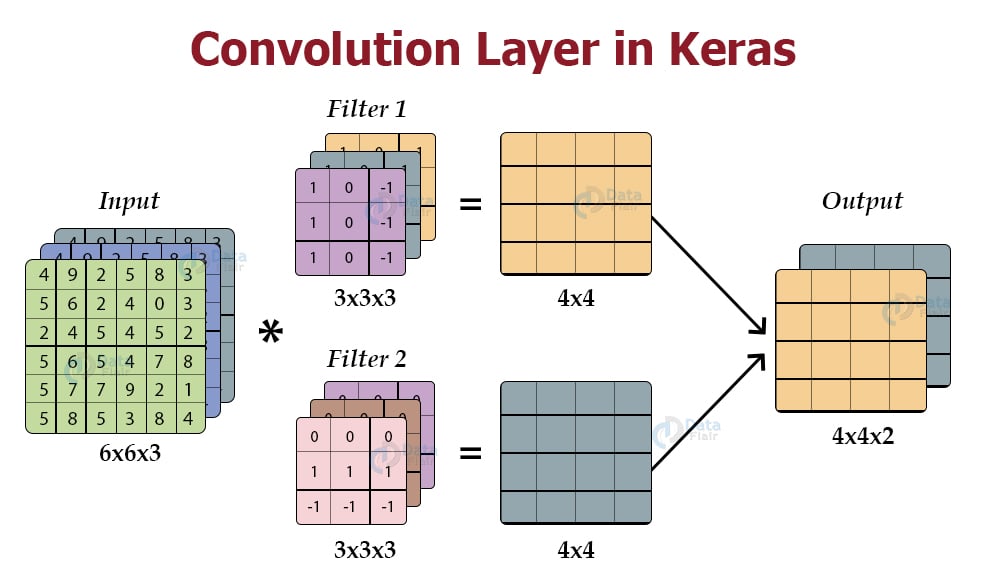
Reverse Eastern Secrete Convolutional Neural Network In Keras Baader To fit this into the fabric of keras, i created a custom layer and called it 'recover'. it is not triggered while the model is trained, however it serves as a faux input layer for the reverse training step. Algorithm 1 summarizes the overall structure reverse engineering attack procedure. In this paper, however, we attempt to provide an evaluation strategy for such information leakages through deep neural network architectures by considering a case study on convolutional neural network (cnn) based image classifier. In this work, we investigate how to reverse engineer a neural network by using side channel information such as timing and electromagnetic (em) emanations. This article demonstrates that architectural side channel attacks (i.e., memory access patterns) can help leak the parameters of a convolutional neural network. In this guide, we shall focus on one of these models. it is perhaps one of the most revolutionary and fundamental models in recent times, a convolution neural network (or cnn for short). along the way, there are some sections listed this way.
Comments are closed.