Pdf Most Common File Type In Targeted Attacks F Secure Weblog News
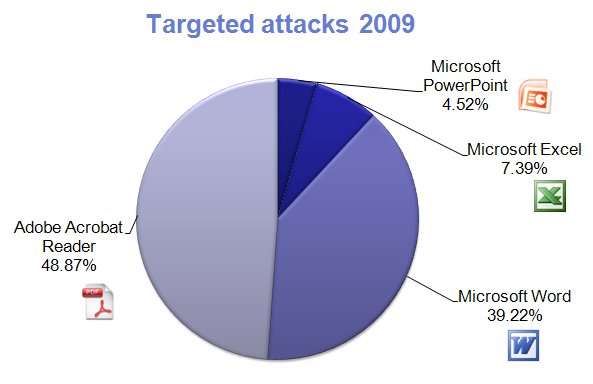
Pdf Most Common File Type In Targeted Attacks F Secure Weblog News So far in 2009 we have discovered 663 targeted attack files and the most popular file type is now pdf. why has it changed? primarily because there has been more vulnerabilities in adobe acrobat reader than in the microsoft office applications. like the two vulnerabilities we mentioned a week ago. According to checkpoint research, while 68% of all malicious attacks are delivered through email, pdf based attacks now constitute 22% of all malicious email attachments, making them a significant security concern for organizations worldwide.
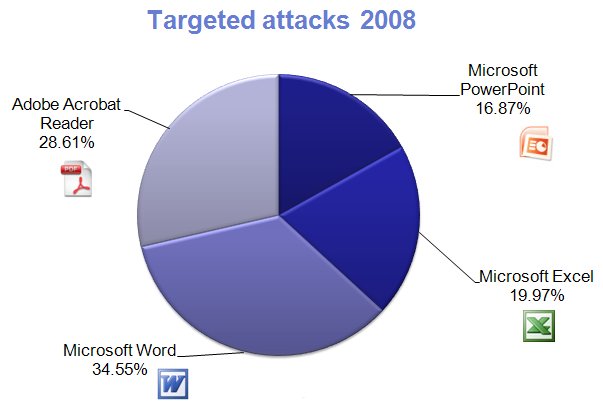
Pdf Most Common File Type In Targeted Attacks F Secure Weblog News Pdf threats are on the rise with cybercriminals spreading malware, including wikiloader, ursnif and darkgate, through pdfs, a new report by hp wolf security has found. the company’s analysis saw a 7% rise in pdf threats in q4 2023, compared to q1 of the same year. Over 87% of organizations use pdfs as a standard file format for business communication, making them ideal vehicles for attackers to hide malicious code. malicious pdfs have been cyber criminals’ favorite gateways for years but have now become even more popular. Pdf files are used similarly to microsoft office files in that criminals can sneak malware through defenses disguised as harmless documents. pdfs can run javascript and contain other dangerous code that can compromise a network or targeted system. According to check point research, 22% of malicious email attachments are now embedded in pdfs, making them one of the most commonly exploited file types in phishing and malware campaigns.

Attacks Pdf Encryption Information Security Pdf files are used similarly to microsoft office files in that criminals can sneak malware through defenses disguised as harmless documents. pdfs can run javascript and contain other dangerous code that can compromise a network or targeted system. According to check point research, 22% of malicious email attachments are now embedded in pdfs, making them one of the most commonly exploited file types in phishing and malware campaigns. The ibm x force threat intelligence index 2025 highlights a significant shift; pdfs have overtaken .zip files as the most common attachment in phishing emails. and the reasons go beyond just convenience—they tap into user psychology, technical blind spots, and security gaps. Social engineering: threat actors use social engineering to deceive users into opening pdf files, often in fake brand or service emails, aiming to extract sensitive data. these pdfs appear legitimate but serve malicious purposes. Threat actors use weaponized pdf files to exploit software vulnerabilities, enabling them to execute malicious code on a target system. pdfs provide a common and trusted format that makes them effective vehicles for delivering malware or launching phishing attacks. It's pretty awesome that opening a pdf can give someone the ability to install a malware on your machine. i wish windows would give you the ability to force certain programs to operate in a sandbox by default.

Other Attacks Pdf World Wide Web Internet Web The ibm x force threat intelligence index 2025 highlights a significant shift; pdfs have overtaken .zip files as the most common attachment in phishing emails. and the reasons go beyond just convenience—they tap into user psychology, technical blind spots, and security gaps. Social engineering: threat actors use social engineering to deceive users into opening pdf files, often in fake brand or service emails, aiming to extract sensitive data. these pdfs appear legitimate but serve malicious purposes. Threat actors use weaponized pdf files to exploit software vulnerabilities, enabling them to execute malicious code on a target system. pdfs provide a common and trusted format that makes them effective vehicles for delivering malware or launching phishing attacks. It's pretty awesome that opening a pdf can give someone the ability to install a malware on your machine. i wish windows would give you the ability to force certain programs to operate in a sandbox by default.

Targeted Attacks Exploiting Pdf Bugs Are Soaring Help Net Security Threat actors use weaponized pdf files to exploit software vulnerabilities, enabling them to execute malicious code on a target system. pdfs provide a common and trusted format that makes them effective vehicles for delivering malware or launching phishing attacks. It's pretty awesome that opening a pdf can give someone the ability to install a malware on your machine. i wish windows would give you the ability to force certain programs to operate in a sandbox by default.

Millions Of Sites Targeted In File Manager Vulnerability Attacks
Comments are closed.