On Manually Reverse Engineering Communication Protocols Of Linux Based

On Manually Reverse Engineering Communication Protocols Of Linux Based In this article, we systematically present the first manual reverse engineering framework for discovering communication protocols of embedded linux based iot systems. In this paper, we propose a framework of manually reverse engineering communication protocols of embedded linux based iot systems so that automation techniques can be ap plied over the discovered protocols for vulnerability discovery and security analysis.
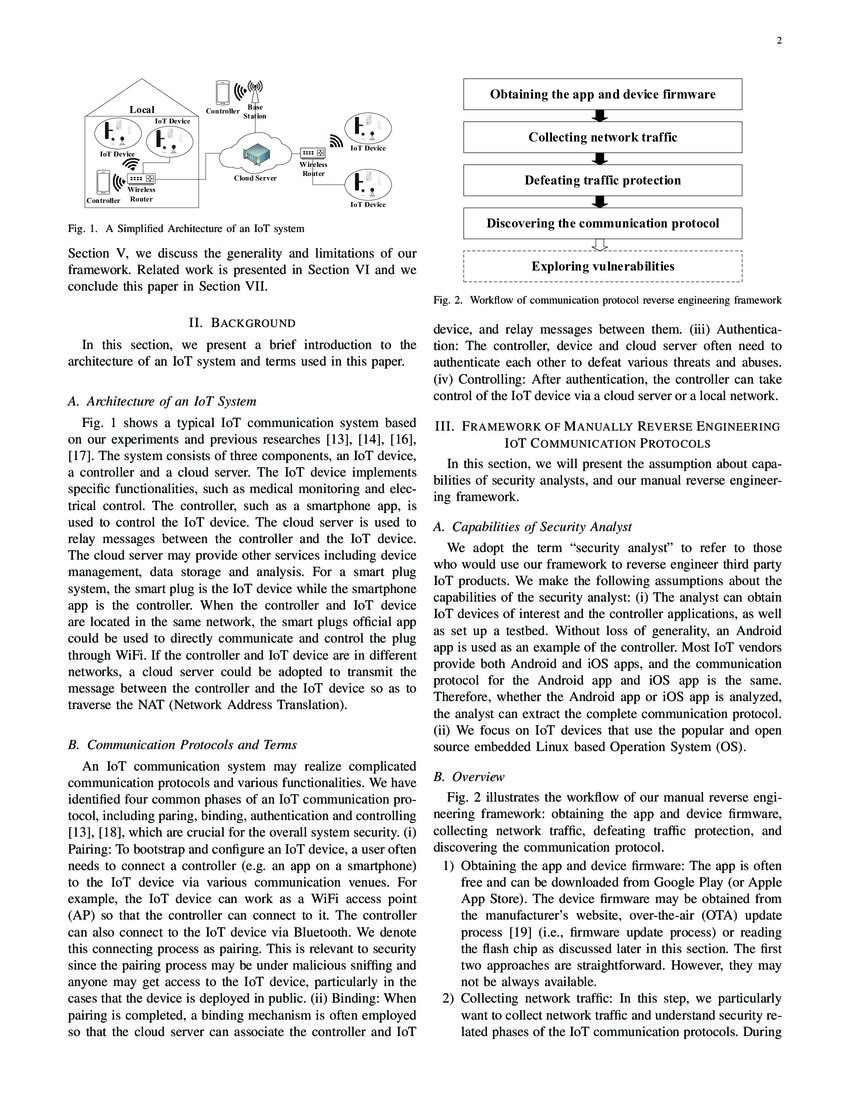
On Manually Reverse Engineering Communication Protocols Of Linux Based Netzob is an open source tool for reverse engineering, modelization, traffic generation and fuzzing of communication protocols. netzob is suitable for reversing network protocols, structured files and system and process flows (ipc and communication with drivers and devices). Most of the existing protocol security analysis techniques rely on a well understanding of the underlying communication protocols. in this talk, we systematically present the first manual. In this article, we system atically present the first manual reverse engineering framework for discovering communication protocols of embedded linux based iot systems. we have. This article systematically presents the first manual reverse engineering framework for discovering communication protocols of embedded linux based iot systems and applies it to both read only and writable embedded linux filesystems.

On Manually Reverse Engineering Communication Protocols Of Linux Based In this article, we system atically present the first manual reverse engineering framework for discovering communication protocols of embedded linux based iot systems. we have. This article systematically presents the first manual reverse engineering framework for discovering communication protocols of embedded linux based iot systems and applies it to both read only and writable embedded linux filesystems. The aim of this paper is 1) to present an overview of the main challenges related to reverse engineering, and 2) to introduce the use of obfuscation techniques to make the reverse engineering process more complex and di cult in particular to malicious users. Osti.gov journal article: on manually reverse engineering communication protocols of linux based iot systems. As an example, this paper presents a complete protocol analysis of the wemo smart plug and identifies severe design flaws that allow attackers to control victim plugs and deny the service of victim plugs. we also briefly discuss how we apply the framework to a few other iot systems.

On Manually Reverse Engineering Communication Protocols Of Linux Based The aim of this paper is 1) to present an overview of the main challenges related to reverse engineering, and 2) to introduce the use of obfuscation techniques to make the reverse engineering process more complex and di cult in particular to malicious users. Osti.gov journal article: on manually reverse engineering communication protocols of linux based iot systems. As an example, this paper presents a complete protocol analysis of the wemo smart plug and identifies severe design flaws that allow attackers to control victim plugs and deny the service of victim plugs. we also briefly discuss how we apply the framework to a few other iot systems.

On Manually Reverse Engineering Communication Protocols Of Linux Based As an example, this paper presents a complete protocol analysis of the wemo smart plug and identifies severe design flaws that allow attackers to control victim plugs and deny the service of victim plugs. we also briefly discuss how we apply the framework to a few other iot systems.
Comments are closed.