Network Security Architecture Best Practices Tools
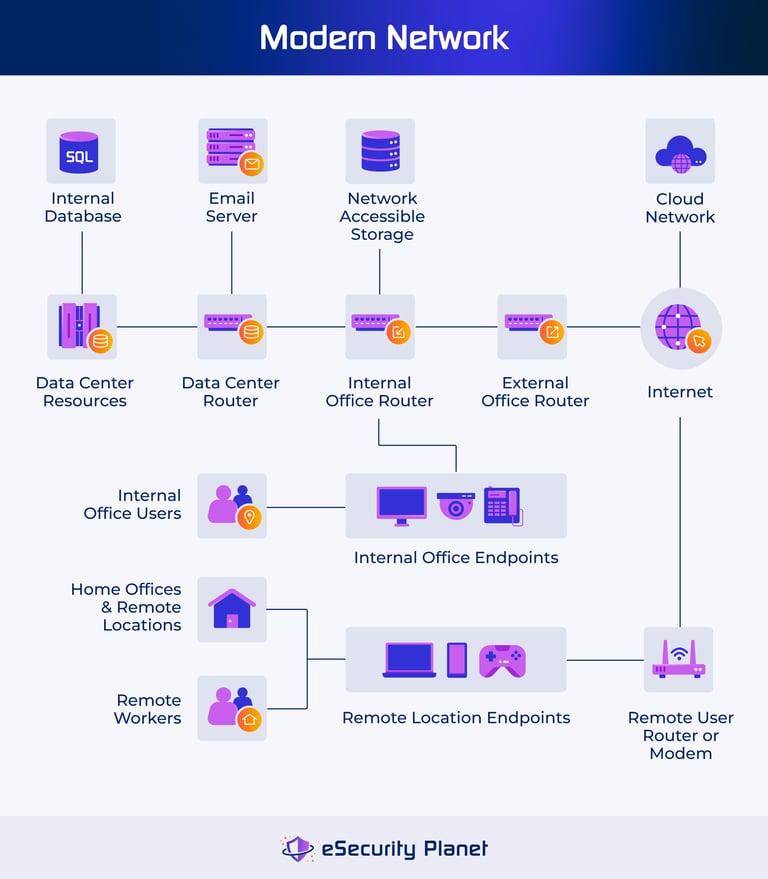
Network Security Architecture Best Practices Tools This article explores network security architecture components, goals, best practices, frameworks, implementation, and benefits as well as where you can learn more about network. Learn how to design, implement and optimize your network security architecture. including framework, metrics, trends and expert insights.
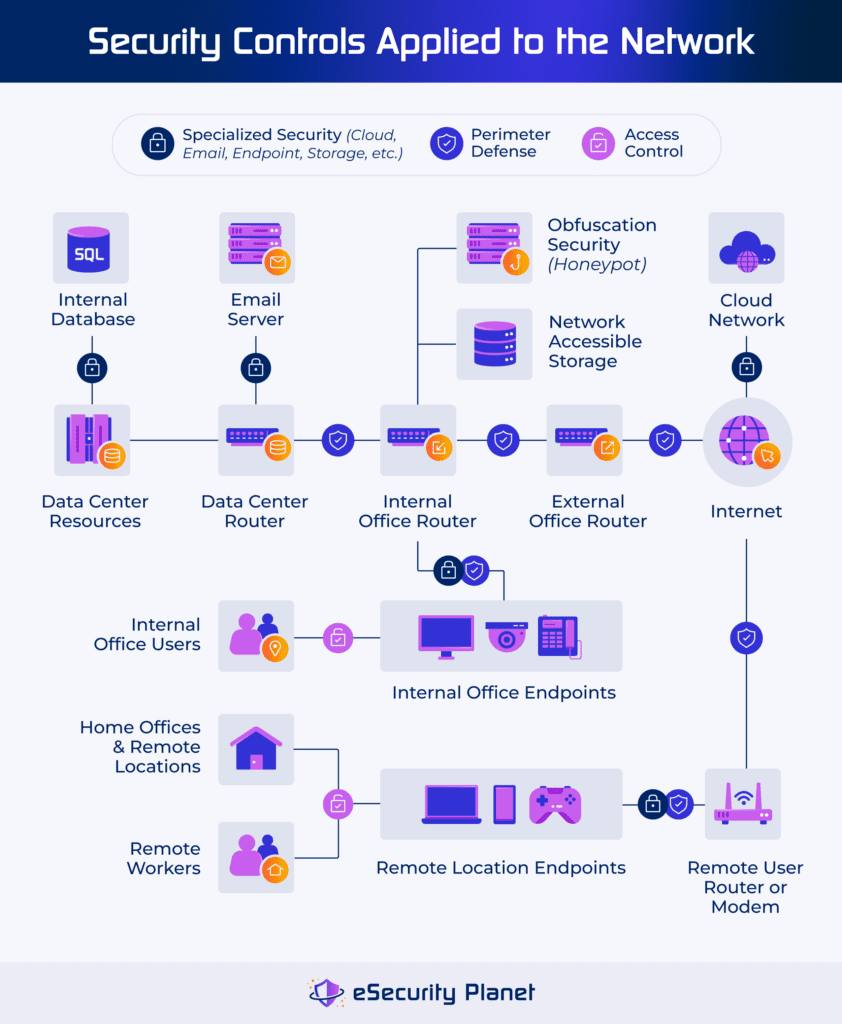
Network Security Architecture Best Practices Tools Itl develops tests, test methods, reference data, proof of concept implementations, and technical analyses to advance the development and productive use of information technology. Aligning network security architecture with established frameworks and standards ensures best practices are followed, bolstering security and compliance. standards like iso 27001, nist, and cis provide guidelines for creating effective security measures and managing risk. These tools are essential for safeguarding networks and data from cyber threats and breaches. from defining and understanding the functionality to choosing the right tools and implementing them successfully, this article will provide a comprehensive guide to security architecture tools. Great hardware and software, like the gear from cisco meraki, give you the tools you need. they make it easy to set up the detailed, identity based rules and micro segmentation that are the heart of a real zero trust model. for example, a university can use this to create separate security zones.

Network Security Best Practices A 15 Point Checklist These tools are essential for safeguarding networks and data from cyber threats and breaches. from defining and understanding the functionality to choosing the right tools and implementing them successfully, this article will provide a comprehensive guide to security architecture tools. Great hardware and software, like the gear from cisco meraki, give you the tools you need. they make it easy to set up the detailed, identity based rules and micro segmentation that are the heart of a real zero trust model. for example, a university can use this to create separate security zones. Network security architecture is a critical component of an organization's overall cybersecurity strategy. by integrating various technologies, protocols, and best practices, it provides a robust defense against cyber threats and ensures the protection of sensitive data. Discover best practices for maintaining robust security measures and stay updated on future trends like ai, blockchain, and iot. enhance your understanding of how to safeguard against evolving cyber threats. Using network security architecture best practices helps protect businesses. it keeps threats away and aligns security with business goals. this includes protecting data with strong protocols and following strict standards like hipaa for healthcare in the us. This comprehensive guide demystifies the critical tools needed to safeguard your network. whether you’re a seasoned it professional or just starting to build your cybersecurity defenses, understanding these tools is crucial for staying ahead of the curve in 2025.
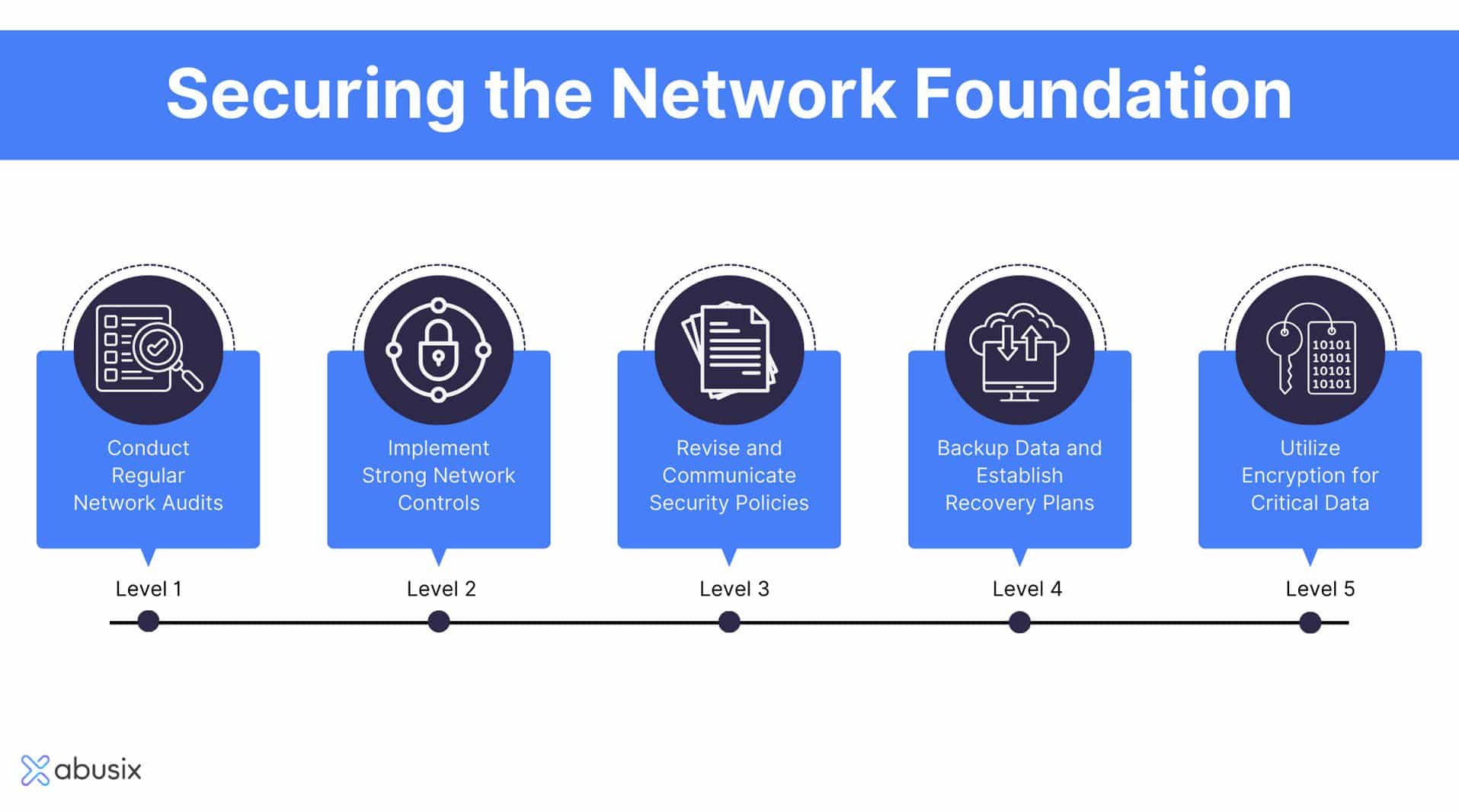
Protect Your Network With These 14 Network Security Best Practices Network security architecture is a critical component of an organization's overall cybersecurity strategy. by integrating various technologies, protocols, and best practices, it provides a robust defense against cyber threats and ensures the protection of sensitive data. Discover best practices for maintaining robust security measures and stay updated on future trends like ai, blockchain, and iot. enhance your understanding of how to safeguard against evolving cyber threats. Using network security architecture best practices helps protect businesses. it keeps threats away and aligns security with business goals. this includes protecting data with strong protocols and following strict standards like hipaa for healthcare in the us. This comprehensive guide demystifies the critical tools needed to safeguard your network. whether you’re a seasoned it professional or just starting to build your cybersecurity defenses, understanding these tools is crucial for staying ahead of the curve in 2025.
Comments are closed.