Manage Ssh With Hashicorp Vault
Manage Ssh With Hashicorp Vault Learn how to build scalable, role based ssh access with ssh certificates and hashicorp vault. Through this tutorial, we will explore how to manage ssh access with the hashicorp vault by beginning to understand the problems associated with the traditional approach and how the ssh architecture can be utilized.

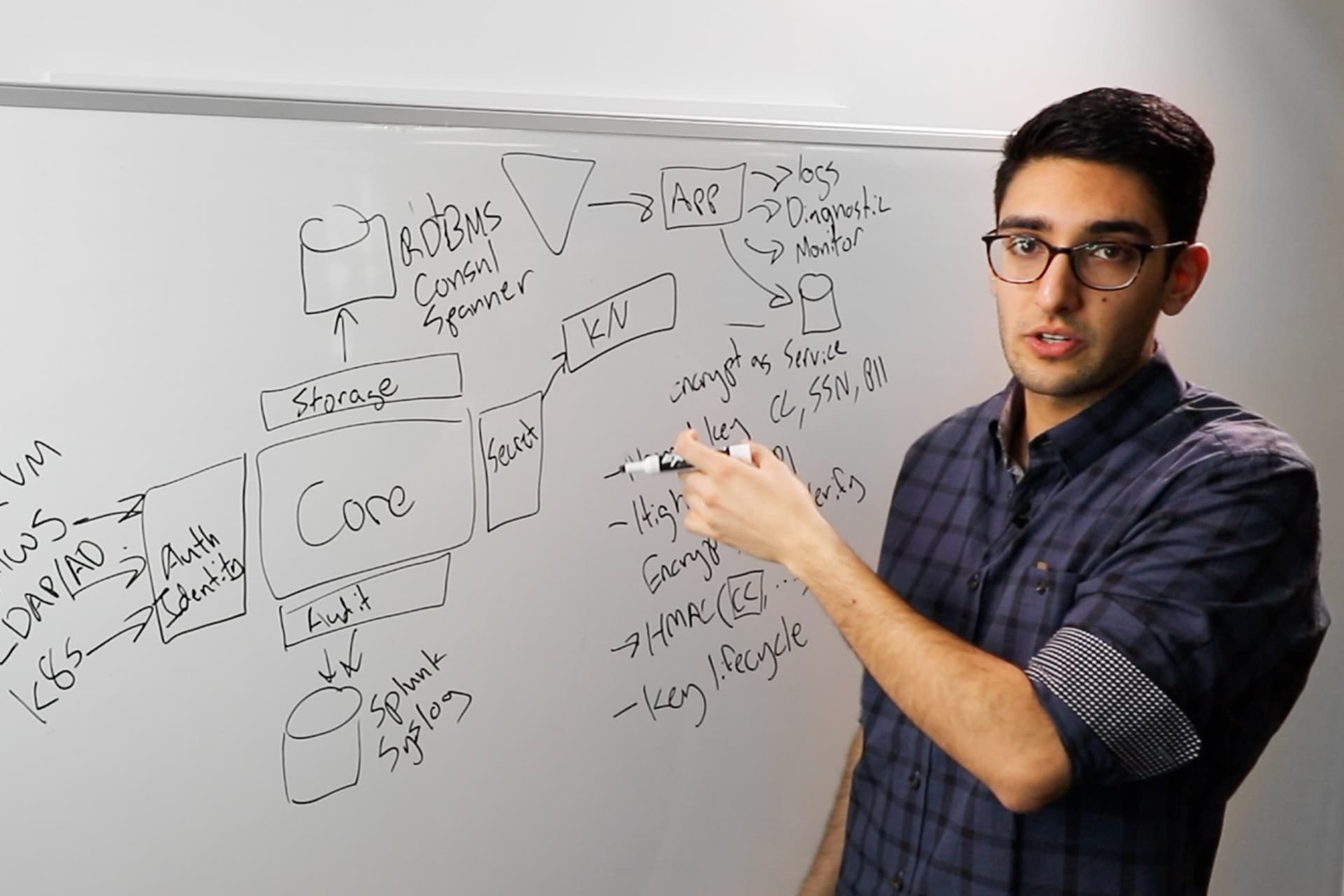
Manage Ssh With Hashicorp Vault In this article, i’m going to walk through setting up how to implement hashicorp vault ssh secrets engine for securing ssh access. administrator authenticates to vault, enables ssh secrets engine, and generates a public key. Hashicorp vault is an identity based secrets and encryption management system. a secret is anything that you want to tightly control access to, such as api encryption keys, passwords, and certificates. Below is a guide to setup vault deployment, and a walkthrough of server side and client side workflow for ssh. how does it work?. This talk will deep dive into the capabilities of vault with respect to ssh, and demo how one time passwords and signed ssh keys work.

Hashicorp Vault Below is a guide to setup vault deployment, and a walkthrough of server side and client side workflow for ssh. how does it work?. This talk will deep dive into the capabilities of vault with respect to ssh, and demo how one time passwords and signed ssh keys work. A lecture about using vault for managing ssh access. After extensive research, we selected hashicorp vault to provide ssh access management via its dynamic ssh certificates engine. why not try our 30 day free trial? fully managed, api first analytics platform. get instant access — no installation or credit card required. The vault ssh secrets engine provides secure authentication and authorization for access to machines via the ssh protocol. the vault ssh secrets engine helps manage access to machine infrastructure, providing several ways to issue ssh credentials. In this article, we’ll demonstrate how to configure hashicorp vault to sign ssh certificates and use them to access a container running an ssh server. the result: secure, dynamic ssh.
Comments are closed.