Malware Hunting On Macos A Practical Guide

Threat Hunting Malware Pdf Malware Information Retrieval Do you want to know if your mac is infected by malware? what should you look for and where should you look for it? find out in this practical guide. Over the past year, i’ve been hard at work writing threat hunting macos —a book that shares the insights i wish i had when i first started threat hunting on a less commonly targeted platform.

Threat Hunting Macos Pdf Malware Command Line Interface Jaron bradley’s upcoming book, threat hunting macos, highlights the need for deeper macos security expertise. this article provides actionable techniques, verified commands, and detection strategies for macos threat hunting. In the art of mac malware, volume 2, patrick wardle distills years of research and real world incident response into a playbook for detecting modern mac threats. In the following pages, you will find practical tips with examples on how to use r2 to deal with macos malware that deploys anti analysis techniques, how to decrypt encrypted strings, how to compare and diff binaries, and how to write and iterate your yara hunting rules. What does malware do to maintain persistence? what does malware want to hide? what does getting a foothold look like? where do malware processes (and their artifacts) live? what does c2 look like? what operating system features does malware use? what does recon look like?.
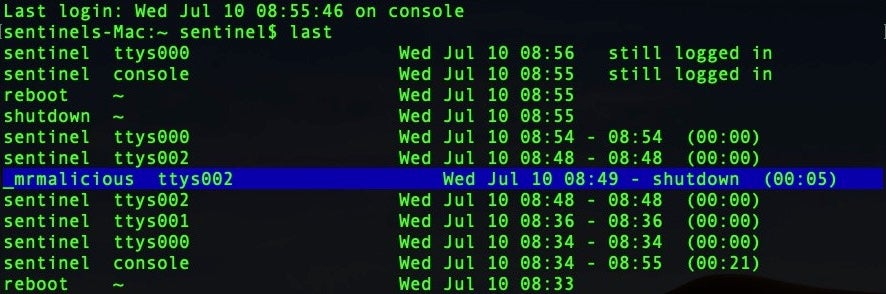
Malware Hunting On Macos A Practical Guide In the following pages, you will find practical tips with examples on how to use r2 to deal with macos malware that deploys anti analysis techniques, how to decrypt encrypted strings, how to compare and diff binaries, and how to write and iterate your yara hunting rules. What does malware do to maintain persistence? what does malware want to hide? what does getting a foothold look like? where do malware processes (and their artifacts) live? what does c2 look like? what operating system features does malware use? what does recon look like?. If you are interested in learning how to hunt malware infections on macos, whether it’s cryptominers, adware, backdoors or nation state actors, the steps outlined above should give you a good start on where to look and what to look for. Learn to detect and respond to macos malware with expert threat hunting techniques. get the essential guide to strengthen your incident response skills. This is a lesson and review of 5 macos malware techniques & how to hunt them using osquery. At macos’s core lies xprotect, apple’s signature based antivirus engine, which is updated independently of system updates. it scans apps at launch, after modifications, and following signature updates, quarantining detected threats like adware.
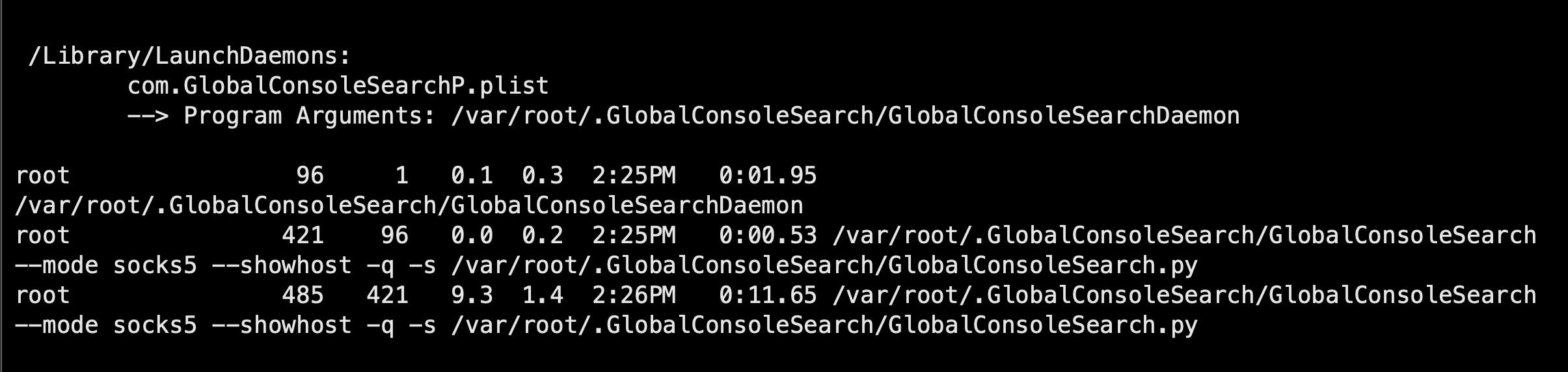
Malware Hunting On Macos A Practical Guide If you are interested in learning how to hunt malware infections on macos, whether it’s cryptominers, adware, backdoors or nation state actors, the steps outlined above should give you a good start on where to look and what to look for. Learn to detect and respond to macos malware with expert threat hunting techniques. get the essential guide to strengthen your incident response skills. This is a lesson and review of 5 macos malware techniques & how to hunt them using osquery. At macos’s core lies xprotect, apple’s signature based antivirus engine, which is updated independently of system updates. it scans apps at launch, after modifications, and following signature updates, quarantining detected threats like adware.

Malware Hunting On Macos A Practical Guide This is a lesson and review of 5 macos malware techniques & how to hunt them using osquery. At macos’s core lies xprotect, apple’s signature based antivirus engine, which is updated independently of system updates. it scans apps at launch, after modifications, and following signature updates, quarantining detected threats like adware.
Comments are closed.