Large Language Models In Cybersecurity Gradient Flow

Large Language Models In Cybersecurity Gradient Flow Cybersecurity provides a useful example of how llms can be implemented in other domains. the result is a general playbook for how llms can be used in other domains and industries. in a previous post, we outlined different options available to teams interested in building their own custom llms. By comprehensively collecting over 30k relevant papers and systematically analyzing 127 papers from top security and software engineering venues, we aim to provide a holistic view of how llms are being used to solve diverse problems across the cybersecurity domain.

Large Language Models In Cybersecurity Gradient Flow As organizations increasingly embed llms into workflows, it’s essential to understand how their use can introduce unique vulnerabilities, such as: prompt injection attacks: malicious users can hide malicious instructions in user inputs or document metadata, making them difficult to detect. Language models remember the simple n gram language model assigns probabilities to sequences of words generate text by sampling possible next words is trained on counts computed from lots of text large language models are similar and different: assigns probabilities to sequences of words. In response to the escalating complexity of cyber threats and the rapid expansion of digital environments, traditional detection models are proving increasingly inadequate. the advent of. Large language models (llms) can easily synthesize huge amounts of threat intelligence feeds into actionable insights. they can evaluate vulnerability reports, analyze malware behavior, and predict potential attack factors beforehand based on historical and real time data.

Large Language Models In Cybersecurity Gradient Flow In response to the escalating complexity of cyber threats and the rapid expansion of digital environments, traditional detection models are proving increasingly inadequate. the advent of. Large language models (llms) can easily synthesize huge amounts of threat intelligence feeds into actionable insights. they can evaluate vulnerability reports, analyze malware behavior, and predict potential attack factors beforehand based on historical and real time data. In this survey, we conduct a comprehensive review of the literature on the application of llms in cybersecurity (llm4security). Recent research has uncovered serious vulnerabilities in llms that malicious actors could exploit to generate toxic outputs, extract private information, or otherwise coerce the models into behaving in dangerous ways contrary to their intended purpose. With the advancement of artificial intelligence, especially large language models in cybersecurity have led to various revolutionary innovations in the software world. Part ii collects a description of the most salient threats llms represent in cybersecurity, be they as tools for cybercriminals or as novel attack surfaces if integrated into existing software.

Maximizing The Potential Of Large Language Models Gradient Flow In this survey, we conduct a comprehensive review of the literature on the application of llms in cybersecurity (llm4security). Recent research has uncovered serious vulnerabilities in llms that malicious actors could exploit to generate toxic outputs, extract private information, or otherwise coerce the models into behaving in dangerous ways contrary to their intended purpose. With the advancement of artificial intelligence, especially large language models in cybersecurity have led to various revolutionary innovations in the software world. Part ii collects a description of the most salient threats llms represent in cybersecurity, be they as tools for cybercriminals or as novel attack surfaces if integrated into existing software.
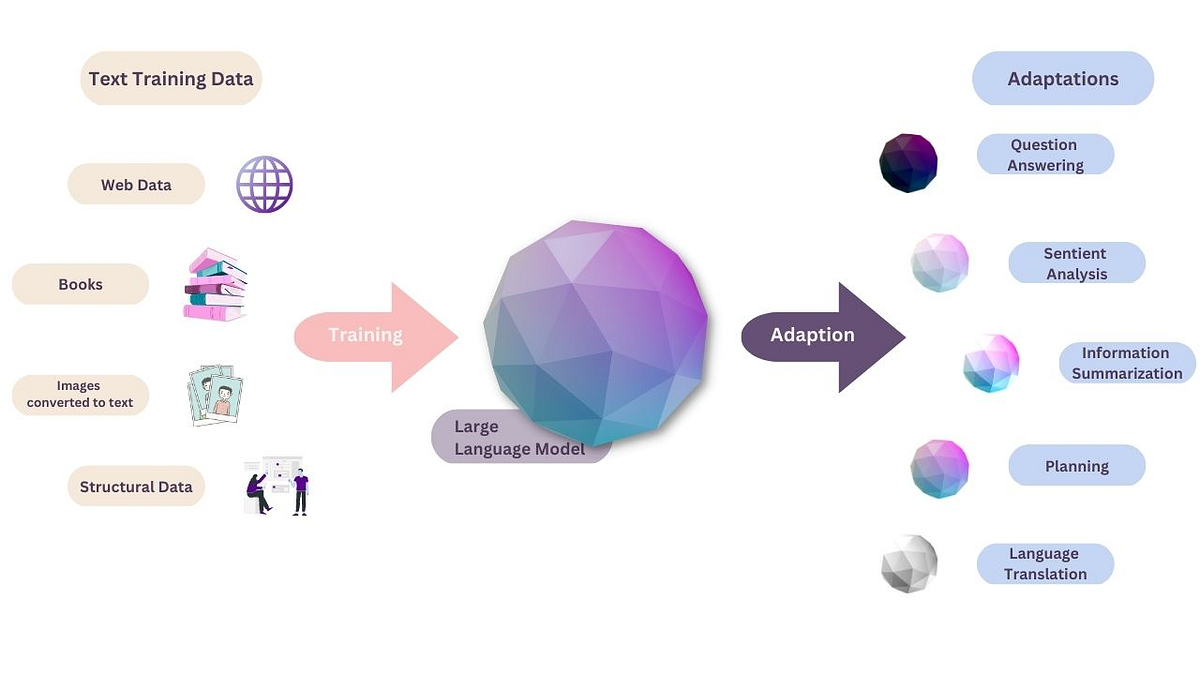
Maximizing The Potential Of Large Language Models Gradient Flow With the advancement of artificial intelligence, especially large language models in cybersecurity have led to various revolutionary innovations in the software world. Part ii collects a description of the most salient threats llms represent in cybersecurity, be they as tools for cybercriminals or as novel attack surfaces if integrated into existing software.

Leveraging Large Language Models For Smarter Cybersecurity Tentacle Blog
Comments are closed.