K8s Security Course Owasp Kubernetes Top 10 Misconfigured Cluster Components

An Overview Of The Owasp Kubernetes Top 10 Orca Security Learn about the owasp kubernetes top 10 risks and recommendations for deploying and managing containerized workloads safely. In this section, we will discuss the ten most common security misconfigurations in kubernetes and how to address them, starting with the overly permissive role based access control (rbac) assignments.
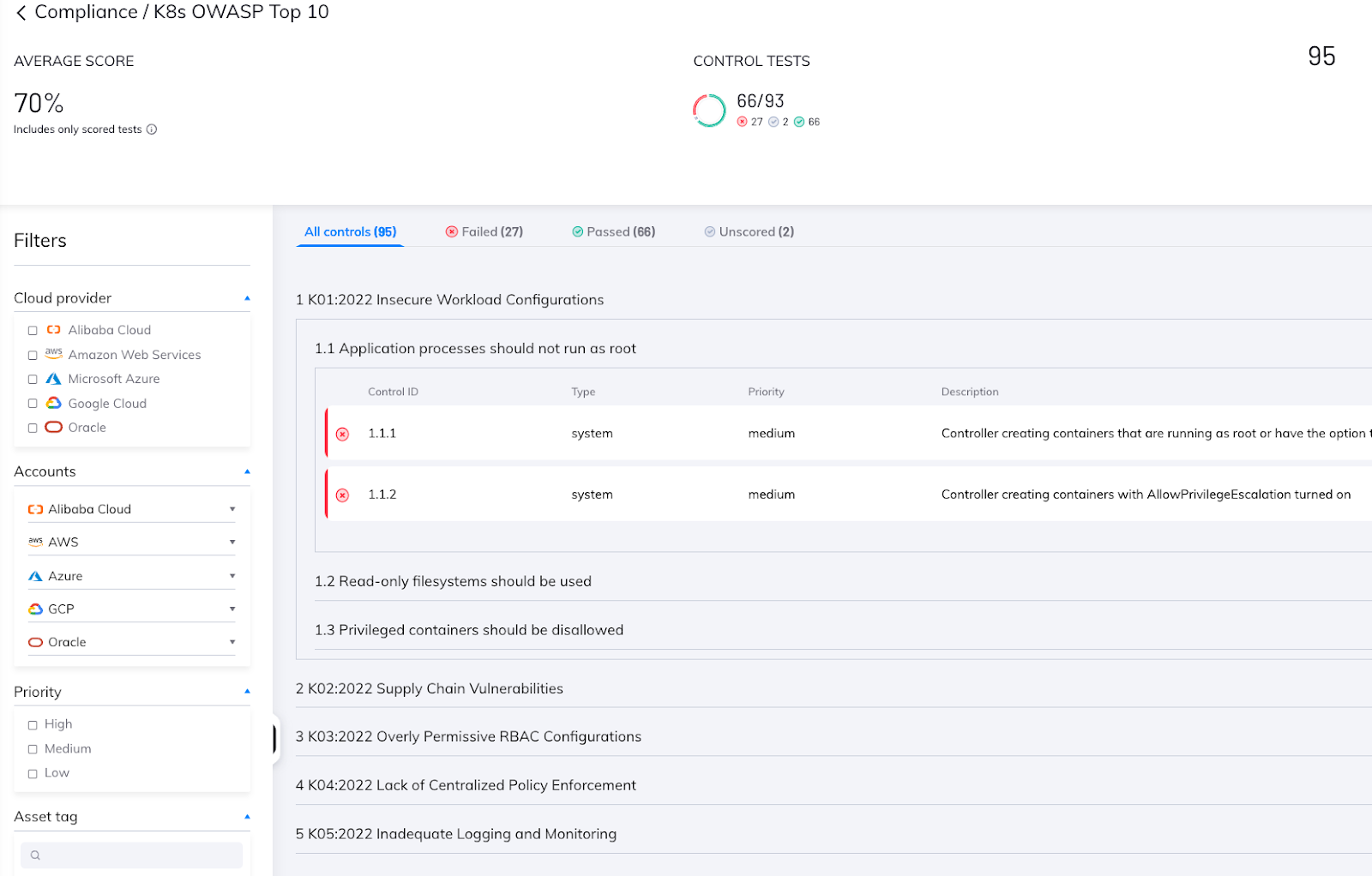
An Overview Of The Owasp Kubernetes Top 10 Orca Security Securing k8s clusters nages the cluster, including scheduling, scaling, and monitoring. securing the cluster includes securing the control plane components, such as the api server, etcd, and kubernetes controller. The examples and configurations shared here represent common scenarios i’ve encountered in real world deployments and in kubernetes goat exercises. The owasp kubernetes top ten highlights the most critical security risks facing kubernetes environments. among these, k09: misconfigured cluster components stands out as a prevalent yet often overlooked risk. This article discussed the 10 most common kubernetes security misconfigurations and their solutions. ensuring these common misconfigurations are properly configured will help keep the cluster secure.

K09 Misconfigured Cluster Components Owasp Foundation The owasp kubernetes top ten highlights the most critical security risks facing kubernetes environments. among these, k09: misconfigured cluster components stands out as a prevalent yet often overlooked risk. This article discussed the 10 most common kubernetes security misconfigurations and their solutions. ensuring these common misconfigurations are properly configured will help keep the cluster secure. The framework is based on the owasp kubernetes top 10 list of security risks and includes a set of orca’s advanced detection tests for identifying vulnerabilities and misconfigurations in k8s environments. Misconfigurations in core kubernetes components can lead to complete cluster compromise or worse. in this section we will explore some of the components that exist on the kubernetes control plane and nodes which can easily be misconfigured:. In the visual above, we spotlight which component or part is impacted by each of the risks that appear in owasp kubernetes mapped to a generalized kubernetes threat model to aid in understanding. this analysis also dives into each owasp risk, providing technical details on why the threat is prominent, as well as common mitigations.

Owasp Top 10 For Docker And Kubernetes Security Eshoptrip The framework is based on the owasp kubernetes top 10 list of security risks and includes a set of orca’s advanced detection tests for identifying vulnerabilities and misconfigurations in k8s environments. Misconfigurations in core kubernetes components can lead to complete cluster compromise or worse. in this section we will explore some of the components that exist on the kubernetes control plane and nodes which can easily be misconfigured:. In the visual above, we spotlight which component or part is impacted by each of the risks that appear in owasp kubernetes mapped to a generalized kubernetes threat model to aid in understanding. this analysis also dives into each owasp risk, providing technical details on why the threat is prominent, as well as common mitigations.
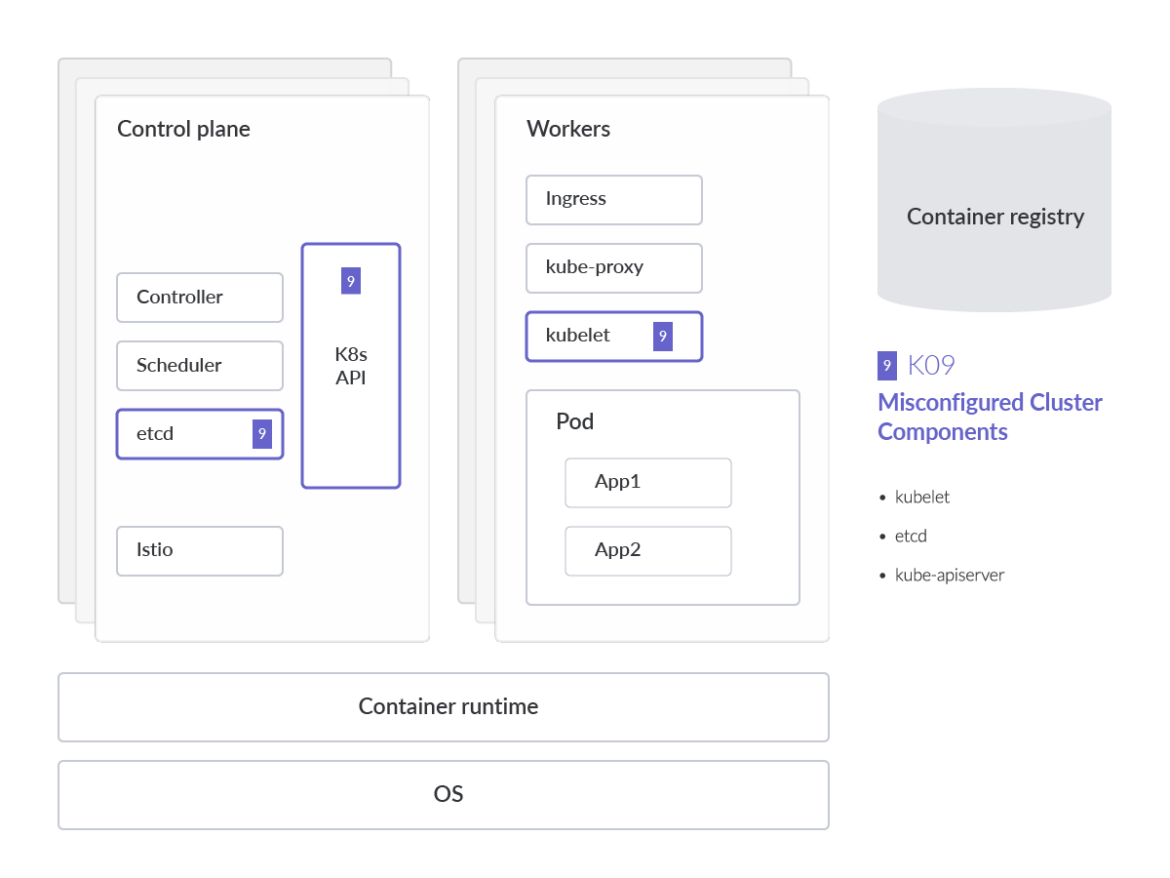
Owasp Kubernetes Top 10 In the visual above, we spotlight which component or part is impacted by each of the risks that appear in owasp kubernetes mapped to a generalized kubernetes threat model to aid in understanding. this analysis also dives into each owasp risk, providing technical details on why the threat is prominent, as well as common mitigations.
Comments are closed.