K8s Security Best Practices Owasp Kubernetes Top 10 Outdated And Vulnerable Kubernetes Component

An Overview Of The Owasp Kubernetes Top 10 Orca Security Securing k8s clusters nages the cluster, including scheduling, scaling, and monitoring. securing the cluster includes securing the control plane components, such as the api server, etcd, and kubernetes controller. For software developers and software architects, understanding the implications of outdated kubernetes components is vital. this blog explores the risks, real world examples, mitigation strategies, and best practices to ensure your kubernetes clusters remain secure and resilient. what are outdated kubernetes components?.
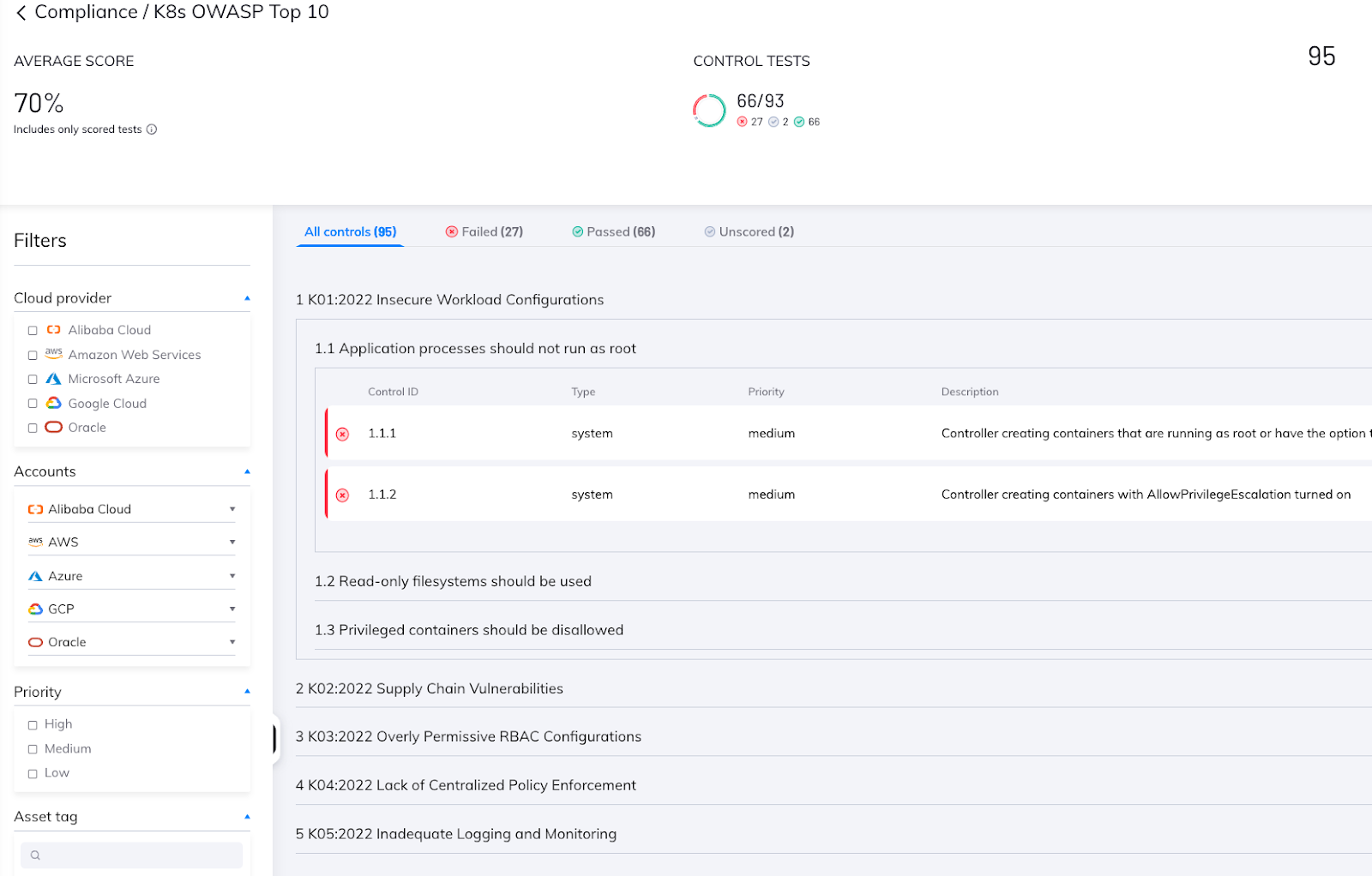
An Overview Of The Owasp Kubernetes Top 10 Orca Security In this blog post, we'll examine the owasp kubernetes top 10 list and discuss best practices for securing containerized infrastructure and addressing risks. In the visual above, we spotlight which component or part is impacted by each of the risks that appear in owasp kubernetes mapped to a generalized kubernetes threat model to aid in understanding. In this article, we’ll explore each of the owasp top 10 kubernetes risks, discuss how they can impact your environment, and provide best practices for mitigating them. Here is an in depth look at each of these top 10 risks: in kubernetes, incomplete workload configurations entail the wrong settings and approaches for application deployment and management in.

Owasp Top 10 For Docker And Kubernetes Security Eshoptrip In this article, we’ll explore each of the owasp top 10 kubernetes risks, discuss how they can impact your environment, and provide best practices for mitigating them. Here is an in depth look at each of these top 10 risks: in kubernetes, incomplete workload configurations entail the wrong settings and approaches for application deployment and management in. One key resource for security best practices is the kubernetes owasp top 10. this list highlights the most critical vulnerabilities and misconfigurations affecting kubernetes. Owasp recently published the owasp kubernetes top 10, outlining the top security risks for kubernetes. learn more about each risk, along with targeted controls to mitigate each one, in this white paper from suse. Top 10 kubernetes risks on the main website for the owasp foundation. owasp is a nonprofit foundation that works to improve the security of software. The owasp kubernetes top 10, developed by jimmy mesta, co founder and cto at ksoc, accumulates some of the most pressing risks and vulnerabilities associated with developing on kubernetes.
Comments are closed.