Introduction To Iot Characteristics Applications Security Issues And

Iot Security Pdf Internet Of Things Computer Security This chapter delves further into iot systems, starting with their concept, evolution, and key components. it delves further into essential applications and the expanding security difficulties they confront, namely in the areas of vulnerability analysis, intrusion detection, and malware. In addressing prevalent issues and challenges in designing and deploying iot applications, the chapter examines security threats across architectural layers, ethical considerations, user privacy concerns, and trust related issues.

Iot Security Part 1 Pdf Internet Of Things Security Additionally, a case study of healthcare in iot is presented. the study depicts the architecture, security, and privacy issues and application of learning paradigms in this sector. the research assessment is finally concluded by listing the results derived from the literature. To guarantee success, these applications need the characteristics of the environment provided by the iot framework. this essay dives deep into the iot's layered architecture, layer by layer protocols, cutting edge use cases, and pervasive security concerns. The majority of network traffic coming from internet of things devices is not encrypted which raises the risk of data breaches and security concerns. by making sure every device is encrypted and secured, these risks may be averted. The syllabus covers 4 units: an introduction to iot including its characteristics, applications and challenges; iot reference architectures and design constraints; privacy, security and governance issues; and interoperability through programming languages and platforms like arduino and raspberry pi.
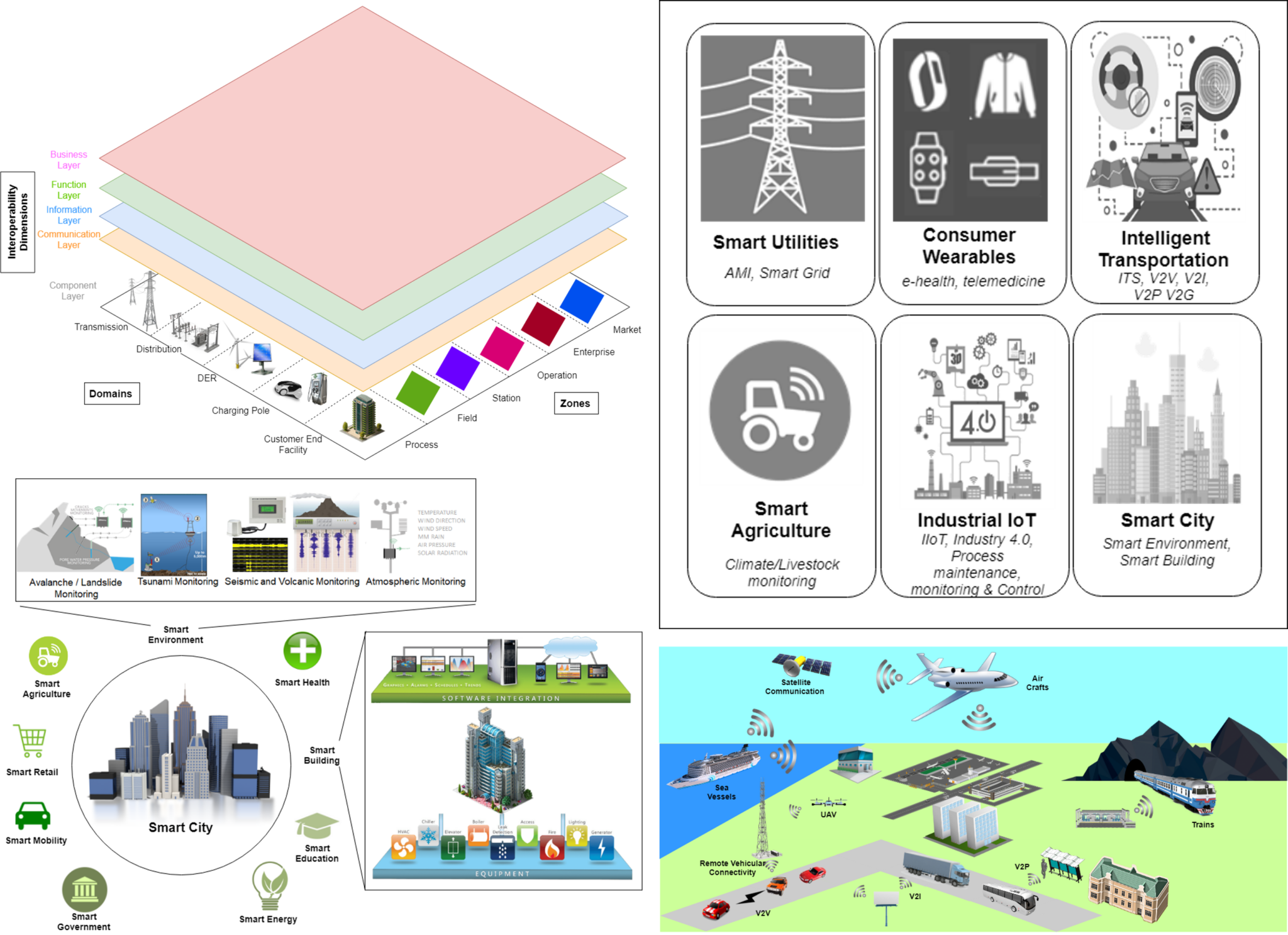
Introduction To Iot Security Netslab The majority of network traffic coming from internet of things devices is not encrypted which raises the risk of data breaches and security concerns. by making sure every device is encrypted and secured, these risks may be averted. The syllabus covers 4 units: an introduction to iot including its characteristics, applications and challenges; iot reference architectures and design constraints; privacy, security and governance issues; and interoperability through programming languages and platforms like arduino and raspberry pi. Therefore, the goal of this paper is to identify the security challenges and key issues that are likely to arise in the iot environment in order to guide authentication techniques to achieve a secure iot service. 1. introduction. in recent years, technology sector has known a real evolution. In addressing prevalent issues and challenges in designing and deploying iot applications, the chapter examines security threats across architectural layers, ethical considerations, user privacy concerns, and trust related issues. The layers of any internet of things application are the middleware layer, application layer, network layer, and sensor layer. these layers are all made up of different technologies, each of which brings with it new problems and security risks. This short paper first presents an introduction to iot and its security issues, including an overview of iot layer models and topologies, iot standardisation efforts and protocols. the.

Iot Security And Privacy Issues Download Scientific Diagram Therefore, the goal of this paper is to identify the security challenges and key issues that are likely to arise in the iot environment in order to guide authentication techniques to achieve a secure iot service. 1. introduction. in recent years, technology sector has known a real evolution. In addressing prevalent issues and challenges in designing and deploying iot applications, the chapter examines security threats across architectural layers, ethical considerations, user privacy concerns, and trust related issues. The layers of any internet of things application are the middleware layer, application layer, network layer, and sensor layer. these layers are all made up of different technologies, each of which brings with it new problems and security risks. This short paper first presents an introduction to iot and its security issues, including an overview of iot layer models and topologies, iot standardisation efforts and protocols. the.

Iot Security Kim Lab The layers of any internet of things application are the middleware layer, application layer, network layer, and sensor layer. these layers are all made up of different technologies, each of which brings with it new problems and security risks. This short paper first presents an introduction to iot and its security issues, including an overview of iot layer models and topologies, iot standardisation efforts and protocols. the.
Comments are closed.