Introduction To Digital Signature In Cryptography Pptx

Digital Signature Cryptography My2 Abhishek Praja C Download Free Explore encryption and decryption download as a pptx, pdf or view online for free. This document discusses digital signatures, including their history, basic requirements, how they work, algorithms, applications, and drawbacks. digital signatures provide authenticity, integrity, and non repudiation for electronic documents by encrypting a message hash with a private key.

Digital Signature Cryptography Monotone Icon In Powerpoint Pptx Png And Technically, digital signature is performed by a signing algorithm and it is verified by a verification algorithm. a copy of digital (conventional) signature is identical (usually distinguishable) to (from) the origin. a care has therefore to be made that a classical signature is not misused. Digital signatures are cryptographic techniques used to validate the authenticity and integrity of digital messages or documents. unlike traditional handwritten signatures, digital signatures rely on complex algorithms and public key infrastructure (pki) to create a unique digital fingerprint. By contrast, post quantum public key cryptography appears to offer much more effective mitigations for real world communications systems from the threat of future quantum computers.”. Overview purpose of a signature security concepts drawbacks of a signature email cryptography solutions do you read what you sign?.

Digital Signature Cryptography Colored Icon In Powerpoint Pptx Png And By contrast, post quantum public key cryptography appears to offer much more effective mitigations for real world communications systems from the threat of future quantum computers.”. Overview purpose of a signature security concepts drawbacks of a signature email cryptography solutions do you read what you sign?. It discusses how digital signatures work using public and private keys along with digital certificates from a certification authority. the document also outlines some applications of digital signatures like email, data storage, funds transfer, and software distribution. Dsa is the us govt approved signature scheme designed to provide strong signatures without allowing easy use for encryption. the signature scheme has advantages, being both smaller (320 vs 1024bit) and faster (much of the computation is done modulo a 160 bit number) than rsa. This chapter explores digital signatures, a fundamental aspect of cryptography for authenticating messages and ensuring security. topics covered include digital signature models, requirements, types, elgamal and schnorr digital signatures, and the digital signature standard (dss) approved by the us government. This document provides an introduction to digital signatures, including an overview of encryption, hashing, digital signature creation and verification, and different digital signature schemes like rsa, elgamal, and schnorr.
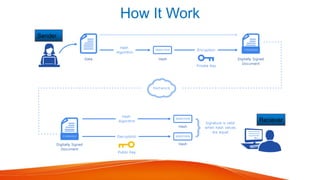
Introduction To Digital Signature In Cryptography Pptx It discusses how digital signatures work using public and private keys along with digital certificates from a certification authority. the document also outlines some applications of digital signatures like email, data storage, funds transfer, and software distribution. Dsa is the us govt approved signature scheme designed to provide strong signatures without allowing easy use for encryption. the signature scheme has advantages, being both smaller (320 vs 1024bit) and faster (much of the computation is done modulo a 160 bit number) than rsa. This chapter explores digital signatures, a fundamental aspect of cryptography for authenticating messages and ensuring security. topics covered include digital signature models, requirements, types, elgamal and schnorr digital signatures, and the digital signature standard (dss) approved by the us government. This document provides an introduction to digital signatures, including an overview of encryption, hashing, digital signature creation and verification, and different digital signature schemes like rsa, elgamal, and schnorr.
Comments are closed.