Internet Protocol Stack Network Security Presentation
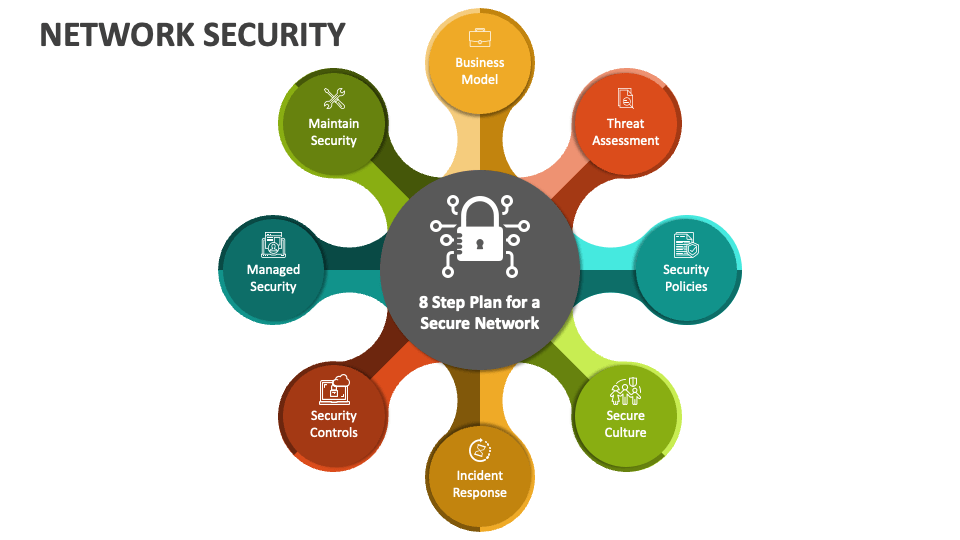
Network Security Powerpoint Presentation Slides Ppt Template Eap transport layer security (eap tls), eap for gsm subscriber identity (eap sim) and eap protected authentication protocol (eap peap) are some of the examples for establishing a secure tunnel. Explore internet security protocols like kerberos, aaa, ipsec, and more. learn about network layers, encryption, tunneling, vpns, messaging security, and web security.
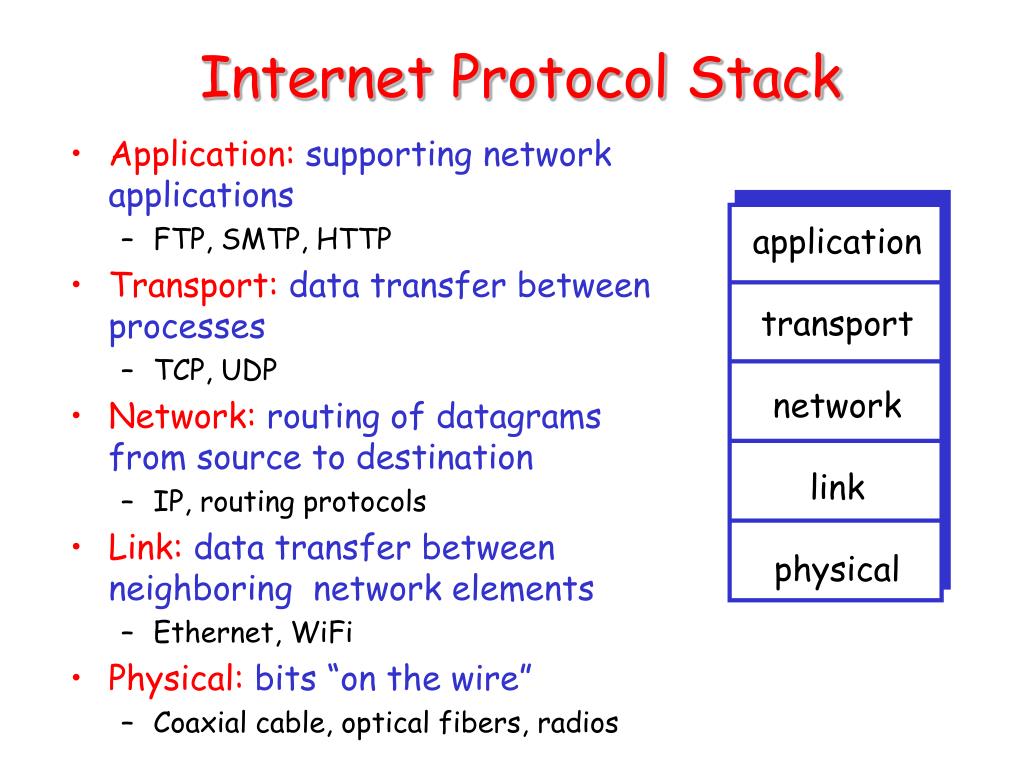
Ppt Internet Protocol Stack Powerpoint Presentation Free Download Allows a client to establish a connection to specific services (e.g., web server on port 80). provides reliable communication. responsible for packet forwarding. how to get a packet to the final destination when there are many hops along the way. how to get packet to the next hop. Presentation on internet security protocols: tcp ip, s mime, ssl tls, https, ipsec. learn about network security layers and standards. Tcp ip protocol stack network layer provides connectionless service routing (routers): determine the path a path has to traverse to reach its destination defines addressing mechanism hosts should conform to the addressing mechanism communication between layers network layer and security in most network architecture and corresponding. Today's internet is primarily comprised of : public un trusted unreliable ip networks because of this inherent lack of security, the internet is subject to various types of threats….
Ppt Protocol Stack Powerpoint Presentation Free Download Id 3406281 Tcp ip protocol stack network layer provides connectionless service routing (routers): determine the path a path has to traverse to reach its destination defines addressing mechanism hosts should conform to the addressing mechanism communication between layers network layer and security in most network architecture and corresponding. Today's internet is primarily comprised of : public un trusted unreliable ip networks because of this inherent lack of security, the internet is subject to various types of threats…. Security problems persist due to difficulties of retrofitting skype, smtp (email), http (web), halo, bittorrent. The architecture of ipsec includes protocols like ah (authentication header) and esp (encapsulation security payload) for ensuring data security during transmission. download as a pdf, pptx or view online for free. When a client or server application sends data across a network, a header (and trailer in the case of layer 2 frames) is added to each data packet from the adjacent layer below it as the data passes through the protocol stack. “network security” lectures will not follow the textbook lectures will focus on “big picture” principles and ideas of network attack and defense attend lectures! lectures will cover some material that is not in the textbook – and you will be tested on it!.
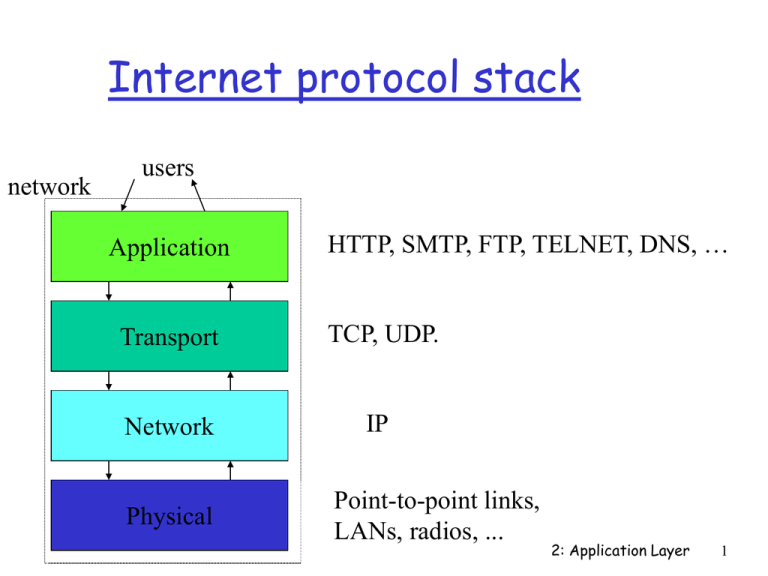
Internet Protocol Stack Network Security Presentation Security problems persist due to difficulties of retrofitting skype, smtp (email), http (web), halo, bittorrent. The architecture of ipsec includes protocols like ah (authentication header) and esp (encapsulation security payload) for ensuring data security during transmission. download as a pdf, pptx or view online for free. When a client or server application sends data across a network, a header (and trailer in the case of layer 2 frames) is added to each data packet from the adjacent layer below it as the data passes through the protocol stack. “network security” lectures will not follow the textbook lectures will focus on “big picture” principles and ideas of network attack and defense attend lectures! lectures will cover some material that is not in the textbook – and you will be tested on it!.
Comments are closed.