How To Use Interactivity In A Malware Sandbox
How To Use Interactivity In A Malware Sandbox This article will explore how malware researchers, soc teams, or dfir team members can benefit from an interactive sandbox. we’ll also look at the advantages of this type of software. Today, we'll show you benefits of interactivity in a sandbox and how it can improve your malware analysis and streamline operations.

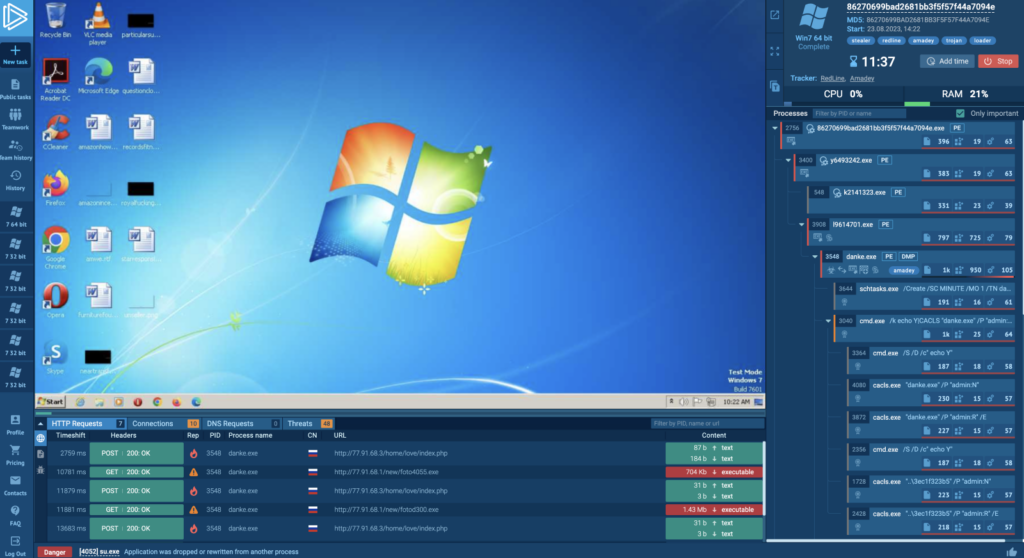
How To Use Interactivity In A Malware Sandbox How to use interactivity in a malware sandbox 3 cases when interactive sandboxes are more reliable than automatic ones ☝️ 1️⃣ recording complex chain of system events, such as during dll hijacking 2️⃣ simulating user behavior, like clipboard interactions, to trigger malware 3️⃣analyzing phishing campaigns see examples 👉 here. Malware sandboxes can be two types: automatic and interactive. automated sandboxes perform analysis autonomously. after uploading samples and starting the analysis, we have no control over the emulation process. the sandbox tries to activate the malware itself and reports back to us after some time. Malware sandboxes are essential tools for cybersecurity professionals to analyze and understand malicious software in a safe environment. here are some of the top interactive malware sandboxes used in the industry:. Malware attacks have never felt more relentless, but i finally found peace of mind through strategic sandboxing techniques. these methods create virtual walls between threats and my system, letting me browse and test files with complete confidence. i took sandboxing more seriously after realizing.

How To Use Interactivity In A Malware Sandbox Malware sandboxes are essential tools for cybersecurity professionals to analyze and understand malicious software in a safe environment. here are some of the top interactive malware sandboxes used in the industry:. Malware attacks have never felt more relentless, but i finally found peace of mind through strategic sandboxing techniques. these methods create virtual walls between threats and my system, letting me browse and test files with complete confidence. i took sandboxing more seriously after realizing. How interactive malware sandboxes work? when a sample is uploaded to the sandbox, the environment is immediately prepared to execute the malware. what sets interactive sandboxes apart is the ability for the analyst to step in and guide the process. Learn about interactive malware sandboxes and see how they help cybersecurity professionals study malware and phishing threats. With interactivity, security teams can manually perform various user interactions, such as clicking on links, entering data, or opening files within the sandbox. Check out this sandbox session in the any.run sandbox that shows how interactivity is used for analyzing the entire chain of attack, starting from a phishing email that contains a pdf attachment. the link inside the .pdf leads to a file sharing website where a password protected .zip is hosted.
Github Areizen Android Malware Sandbox Android Malware Sandbox How interactive malware sandboxes work? when a sample is uploaded to the sandbox, the environment is immediately prepared to execute the malware. what sets interactive sandboxes apart is the ability for the analyst to step in and guide the process. Learn about interactive malware sandboxes and see how they help cybersecurity professionals study malware and phishing threats. With interactivity, security teams can manually perform various user interactions, such as clicking on links, entering data, or opening files within the sandbox. Check out this sandbox session in the any.run sandbox that shows how interactivity is used for analyzing the entire chain of attack, starting from a phishing email that contains a pdf attachment. the link inside the .pdf leads to a file sharing website where a password protected .zip is hosted.
Comments are closed.