How To Detect And Mitigate Botnet Attacks

How To Detect And Mitigate Botnet Attacks There are several ways to identify botnet attacks: 1. signature based detection. signature based detection is a traditional method that identifies botnets by matching known signatures or patterns in data streams. it's effective against known threats with established signatures. Detecting and mitigating botnet attacks is essential for protecting your devices and data from harm. in this article, we will discuss how botnets work, the common signs of a botnet attack, and steps you can take to detect and mitigate these threats. understanding botnets.

Different Techniques To Detect Botnet Pdf Internet Bot Computer Want to know how to prevent botnet attacks? learn how botnet attacks work and how to prevent and mitigate botnet attacks on your websites and servers. Understand how to prevent botnet attacks and the steps they take to originate. protect your users, endpoints, and networks. achieve strong security and speed up incident response to botnet invasions. a botnet attack uses a mix of robots and networks to launch mass scale attacks on organizations. Botnets reach and damage thousands of different computers every day, which makes preventing and detecting botnet attacks a very important security issue. early detection of botnets plays a crucial role in hazard management as it will minimize damage. In 2025, botnets have become more sophisticated, using advanced encryption, p2p command structures, and stealth techniques that make detection harder. detecting botnet infections requires monitoring unusual outbound traffic, dns anomalies, and endpoint behavior.
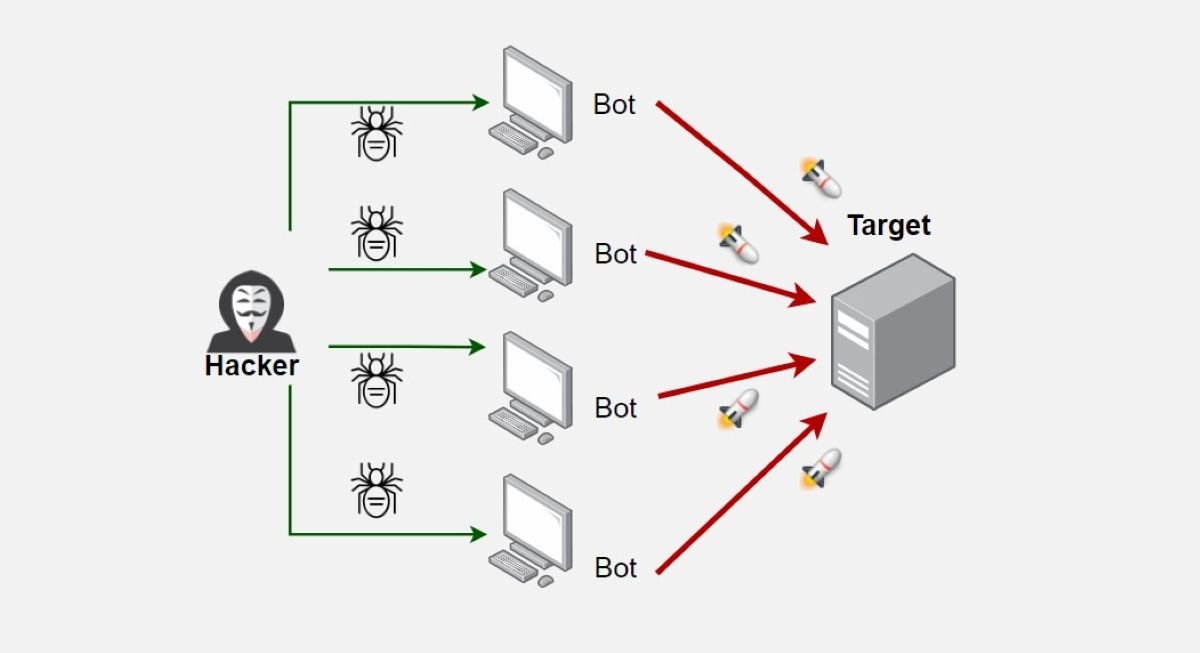
How To Detect And Mitigate Botnet Attacks Botnets reach and damage thousands of different computers every day, which makes preventing and detecting botnet attacks a very important security issue. early detection of botnets plays a crucial role in hazard management as it will minimize damage. In 2025, botnets have become more sophisticated, using advanced encryption, p2p command structures, and stealth techniques that make detection harder. detecting botnet infections requires monitoring unusual outbound traffic, dns anomalies, and endpoint behavior. In this article, we explore how botnets work, how to effectively detect botnets, how your cybersecurity team can remove botnets, and the main tools used in the detection and prevention of botnet attacks. read on to learn more. what is a botnet?. How does a botnet attack work? a hacker or gang of cyber criminals typically seizes control of a network of malware infected computers. these devices are then remotely controlled to simultaneously carry out a synchronized attack, such as the following. To combat botnet attacks, deploying effective detection mechanisms is paramount. intrusion detection systems (ids) and intrusion prevention systems (ips) play crucial roles in monitoring network traffic. ids tools analyze traffic patterns and generate alerts for suspicious activity, while ips systems can automatically block malicious traffic. To prevent a botnet attack, it's important to understand the different stages involved in the attack process. a botnet attack follows a series of steps, to escalate the attack. by recognizing these stages, organizations can form measures at each stage to reduce the risk and impact of a botnet infection.

How To Detect And Mitigate Botnet Attacks In this article, we explore how botnets work, how to effectively detect botnets, how your cybersecurity team can remove botnets, and the main tools used in the detection and prevention of botnet attacks. read on to learn more. what is a botnet?. How does a botnet attack work? a hacker or gang of cyber criminals typically seizes control of a network of malware infected computers. these devices are then remotely controlled to simultaneously carry out a synchronized attack, such as the following. To combat botnet attacks, deploying effective detection mechanisms is paramount. intrusion detection systems (ids) and intrusion prevention systems (ips) play crucial roles in monitoring network traffic. ids tools analyze traffic patterns and generate alerts for suspicious activity, while ips systems can automatically block malicious traffic. To prevent a botnet attack, it's important to understand the different stages involved in the attack process. a botnet attack follows a series of steps, to escalate the attack. by recognizing these stages, organizations can form measures at each stage to reduce the risk and impact of a botnet infection.
Comments are closed.