How Hackers Use Pdf Files To Hack You Stay Safe Cybersecurity Flipperzero Hackingtools

Hackers Pdf "did you know pdf files can be used to hack your device? in this short, i’ll show you how hackers exploit pdfs and share tips to protect yourself. stay safe. Hackers impersonate trusted brands like google, dropbox, and banks to steal credentials, deploy ransomware, or hijack devices for crypto mining. here’s how these scams work, who’s at risk, and how to protect yourself.

Pdf The Hacker Playbook 2 Pdf Pdf Télécharger Download Hackers use this to their advantage, hiding malicious code in javascript to exploit security vulnerabilities within a pdf. just opening a compromised pdf can set off a domino effect, with the virus infecting other files and apps on your device. Hackers are using ai powered phishing attacks via malicious pdf files to steal personal data from iphone and android users. here's how you can protect yourself against such scams. Hackers exploit vulnerabilities in pdf files using various techniques, such as embedding malicious scripts, using javascript based exploits, or utilizing cross site scripting (xss) attacks. Social engineering: threat actors use social engineering to deceive users into opening pdf files, often in fake brand or service emails, aiming to extract sensitive data. these pdfs appear legitimate but serve malicious purposes.
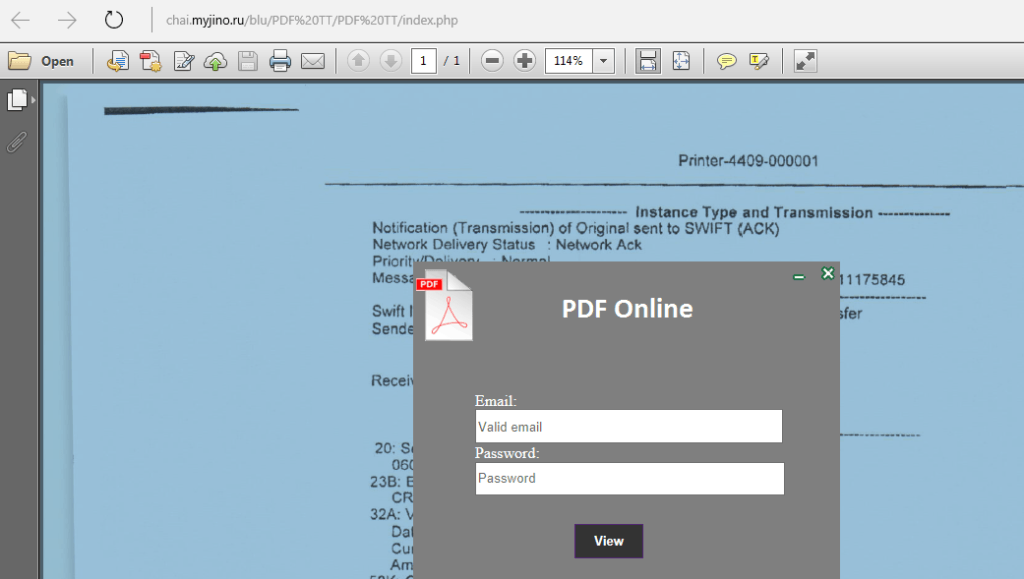
Locked Pdf Phishing Attack Cybrac Hackers exploit vulnerabilities in pdf files using various techniques, such as embedding malicious scripts, using javascript based exploits, or utilizing cross site scripting (xss) attacks. Social engineering: threat actors use social engineering to deceive users into opening pdf files, often in fake brand or service emails, aiming to extract sensitive data. these pdfs appear legitimate but serve malicious purposes. Hackers have begun hiding malicious documents in pdf files as a means to spread malware while avoiding detection by security software. as reported by bleepingcomputer, japan’s computer. The new attack, called pdfex, comes in two variations and in testing, it was successfully able to steal data from pdf files in some of the best free pdf readers across 27 desktop and web t. Flipper zero can be used to break into devices with zero level of security. while traditionally, keysight shows ways to break much more robust implementations, we should not forget that sooner rather than later any attack method becomes accessible to wider audiences. Several different methods can be employed, but the most common form of the pdf exploit is a classic buffer overflow attack. in simple terms, a buffer overflow happens when data exceeding the buffer's capacity is inputted into the system, causing it to overflow.
Comments are closed.