How Encryption Works And How It Can Be Bypassed
How Encryption Works And How It Can Be Bypassed Alleywatch The debate between privacy and national security has never been more heated, with apple and other tech firms going up against the government. so how are text messages encrypted, and what are. When the contents of the ram disappear, the encryption key is lost and the attackers will need your encryption passphrase to decrypt your data. this is how encryption is generally assumed to work, and it's why smart corporations encrypt laptops and smartphones with sensitive data on them.
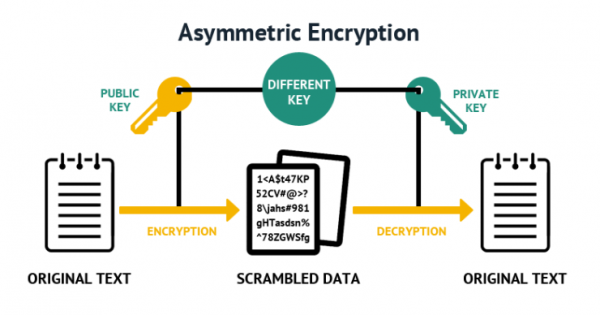
Understanding How Encryption Works So how are text messages encrypted, and what are the controversial "backdoors" that could allow access to them?. Encryption is the method by which information is converted into secret code that hides the information's true meaning. the science of encrypting and decrypting information is called cryptography. encryption has long been used to protect sensitive information. historically, it was used by militaries and governments. We define an encryption workaround as any lawful government effort to reveal unencrypted plaintext of a target’s data that has been concealed by encryption. this article provides an overview of encryption workarounds. it begins with a taxonomy of the different ways investigators might try to bypass encryption schemes. Encryption uses complex mathematical equations to hide information from outsiders, converting documents, messages and files into incomprehensible gibberish. normally, encrypted files require a key to decipher, but in some cases hackers can bypass encryption schemes to steal privileged information.
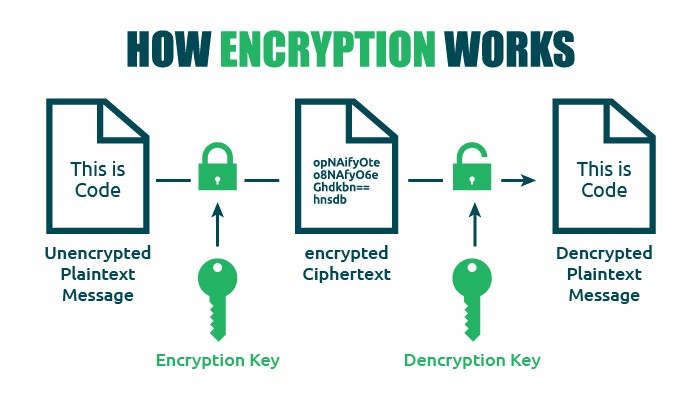
How Encryption Works We define an encryption workaround as any lawful government effort to reveal unencrypted plaintext of a target’s data that has been concealed by encryption. this article provides an overview of encryption workarounds. it begins with a taxonomy of the different ways investigators might try to bypass encryption schemes. Encryption uses complex mathematical equations to hide information from outsiders, converting documents, messages and files into incomprehensible gibberish. normally, encrypted files require a key to decipher, but in some cases hackers can bypass encryption schemes to steal privileged information. The technical consensus is clear: adding ‘backdoors’ to encryption algorithms weakens everyone’s security. so what are the police and intelligence agencies to do?. How encryption works — and how it can be bypassed the debate between privacy and national security has never been more heated, with apple and other tech firms going up against the government. The debate between privacy and national security has never been more heated, with apple and other tech firms going up against the government. so how are text messages encrypted, and what are the controversial “backdoors” that could allow access to them. Encryption is increasingly used to protect national security information, for digital commerce, and on your personal devices, but it can also be used to hide crimes or threats. countries around the world are debating how best to govern it — and have been for decades.
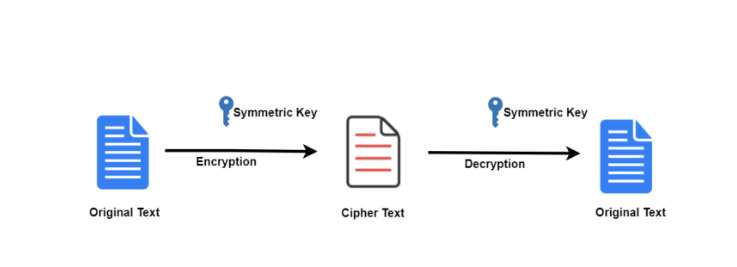
Understanding How Encryption Works The technical consensus is clear: adding ‘backdoors’ to encryption algorithms weakens everyone’s security. so what are the police and intelligence agencies to do?. How encryption works — and how it can be bypassed the debate between privacy and national security has never been more heated, with apple and other tech firms going up against the government. The debate between privacy and national security has never been more heated, with apple and other tech firms going up against the government. so how are text messages encrypted, and what are the controversial “backdoors” that could allow access to them. Encryption is increasingly used to protect national security information, for digital commerce, and on your personal devices, but it can also be used to hide crimes or threats. countries around the world are debating how best to govern it — and have been for decades.
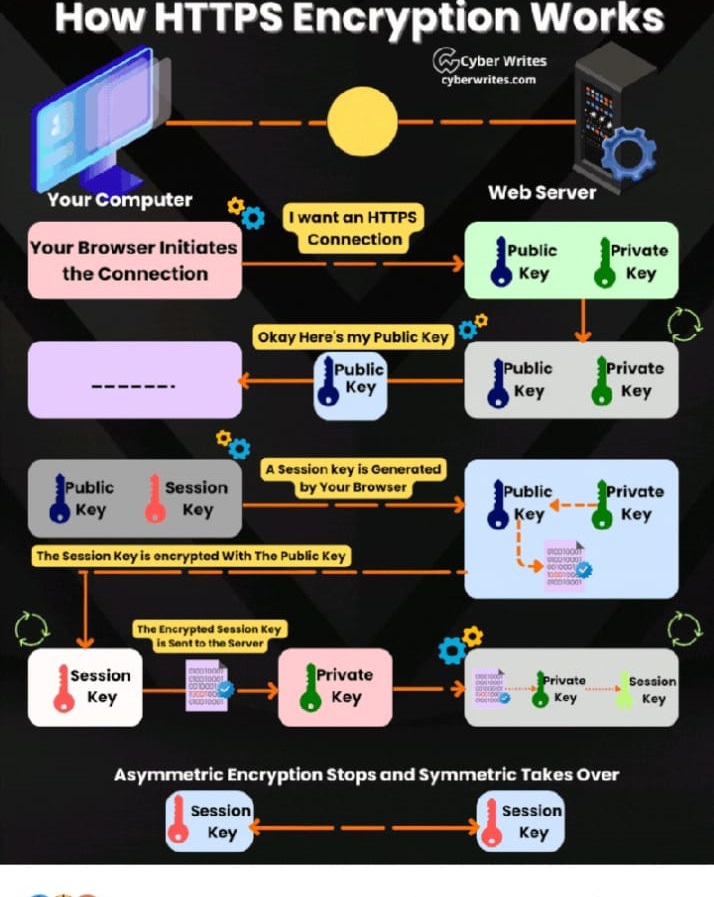
Solved How Https Encryption Works And How Https Encryption Chegg The debate between privacy and national security has never been more heated, with apple and other tech firms going up against the government. so how are text messages encrypted, and what are the controversial “backdoors” that could allow access to them. Encryption is increasingly used to protect national security information, for digital commerce, and on your personal devices, but it can also be used to hide crimes or threats. countries around the world are debating how best to govern it — and have been for decades.

How Encryption Works
Comments are closed.