How Can I Bypass Content Filtering Settings Everyday Networking

Web Filtering Bypass Web Filtering And Browse Anonymously This wikihow teaches you how to view blocked websites or content on a restricted computer, as well as on a mobile item if you're using a virtual private network (vpn). To discuss 10 ways kids might use to bypass internet filters, such as employing vpns, connecting to neighbors' wi fi, and using incognito browsing. for securing internet safety of kids, use powerful parental control programs to block porn content so that they cannot bypass internet filters.

Take Control With Web Content Filtering Software Cisco Umbrella This article provides quick tips and tricks on how to bypass content filtering, enabling users to access desired content while maintaining a secure online environment. So it’s crucial to understand the current landscape of internet censorship, which countries are most affected, how content is filtered, and most importantly, how to bypass and unblock restrictions with feasible tools through this article. Employees can use vpns, proxies, or browser tricks to bypass web filters. learn how these methods work—and how tools like browsecontrol can stop them. So, we are looking at web contact filtering security.microsoft securitysettings endpoints web content filtering policy as we are moving away from webroot, where we have dns filtering and going to huntress. as we have business premium, we dont get all scopes, so applies to all machines.
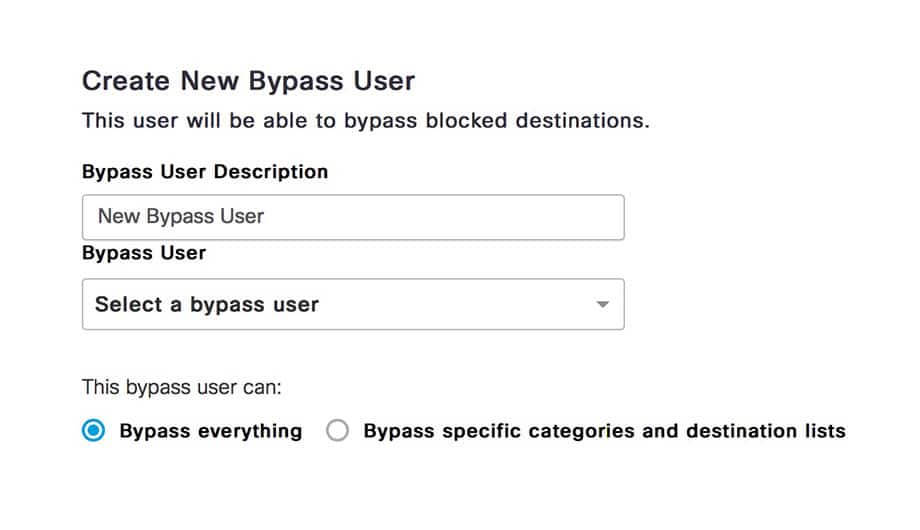
Take Control With Web Content Filtering Software Cisco Umbrella Employees can use vpns, proxies, or browser tricks to bypass web filters. learn how these methods work—and how tools like browsecontrol can stop them. So, we are looking at web contact filtering security.microsoft securitysettings endpoints web content filtering policy as we are moving away from webroot, where we have dns filtering and going to huntress. as we have business premium, we dont get all scopes, so applies to all machines. Unless you have a router that supports vlans where the grown ups computers could be on their own network with their own dhcp scope (not likely in the home router world) your best bet would be to set the dns in each of the kid's computers to opendns and yours to google dns or your own isp. Now that we understand the various forms of content filters, let’s explore the actionable techniques to bypass them. these techniques range from simple modifications to sophisticated network tunneling. This 2025 guide breaks down how network wide content filtering improves security, productivity, and compliance across all devices. Built in vpn and tor features can be used to bypass organizational network policies. built in vpn and tor features are disabled. users cannot bypass organizational network policies. ready to get started? activate your tech lockdown membership and get access to powerful content filtering and device configuration. cancel anytime.
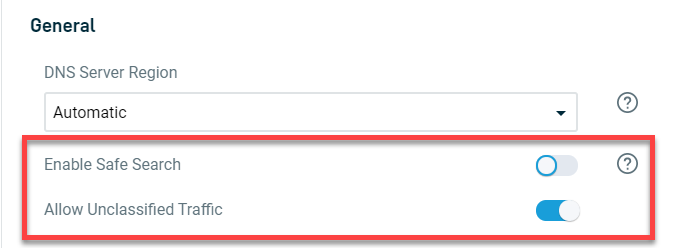
Routers Web Content Filtering Unless you have a router that supports vlans where the grown ups computers could be on their own network with their own dhcp scope (not likely in the home router world) your best bet would be to set the dns in each of the kid's computers to opendns and yours to google dns or your own isp. Now that we understand the various forms of content filters, let’s explore the actionable techniques to bypass them. these techniques range from simple modifications to sophisticated network tunneling. This 2025 guide breaks down how network wide content filtering improves security, productivity, and compliance across all devices. Built in vpn and tor features can be used to bypass organizational network policies. built in vpn and tor features are disabled. users cannot bypass organizational network policies. ready to get started? activate your tech lockdown membership and get access to powerful content filtering and device configuration. cancel anytime.

What Is Content Filtering And What Are The Different Types This 2025 guide breaks down how network wide content filtering improves security, productivity, and compliance across all devices. Built in vpn and tor features can be used to bypass organizational network policies. built in vpn and tor features are disabled. users cannot bypass organizational network policies. ready to get started? activate your tech lockdown membership and get access to powerful content filtering and device configuration. cancel anytime.

Top Practices For Effective Content Filtering
Comments are closed.