Hashing Algorithms And Message Integrity

Secure Hashing Algorithm Pdf Secrecy Algorithms What is hashing? a guide with examples. hashing uses an algorithm to transform input data of any size into a value of fixed length that is extremely difficult to decode. here’s how hashing is used, its benefits and downsides and why it matters in cybersecurity. This post explains hashing algorithms and message integrity. this post constitutes part 1 of a series of posts exploring how ssl and tls use cryptographic tools to secure data transmitted.

08 Hashing Pdf Algorithms And Data Structures Computer Programming To summarise what we have learned so far, the idea of a hashing algorithm used for integrity validation is to provide some assurance that a transferred message or file has arrived intact, that it has not been altered on its way to the recipient. Hashing is a one way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. in the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure. Hashing is essential for ensuring data integrity and security. whether securing passwords, verifying file integrity, or enabling blockchain technology, understanding and using hashing. In the world of secured communications, message integrity describes the concept of ensuring that data has not been modified in transit. this is typically accomplished with the use of a hashing algorithm.
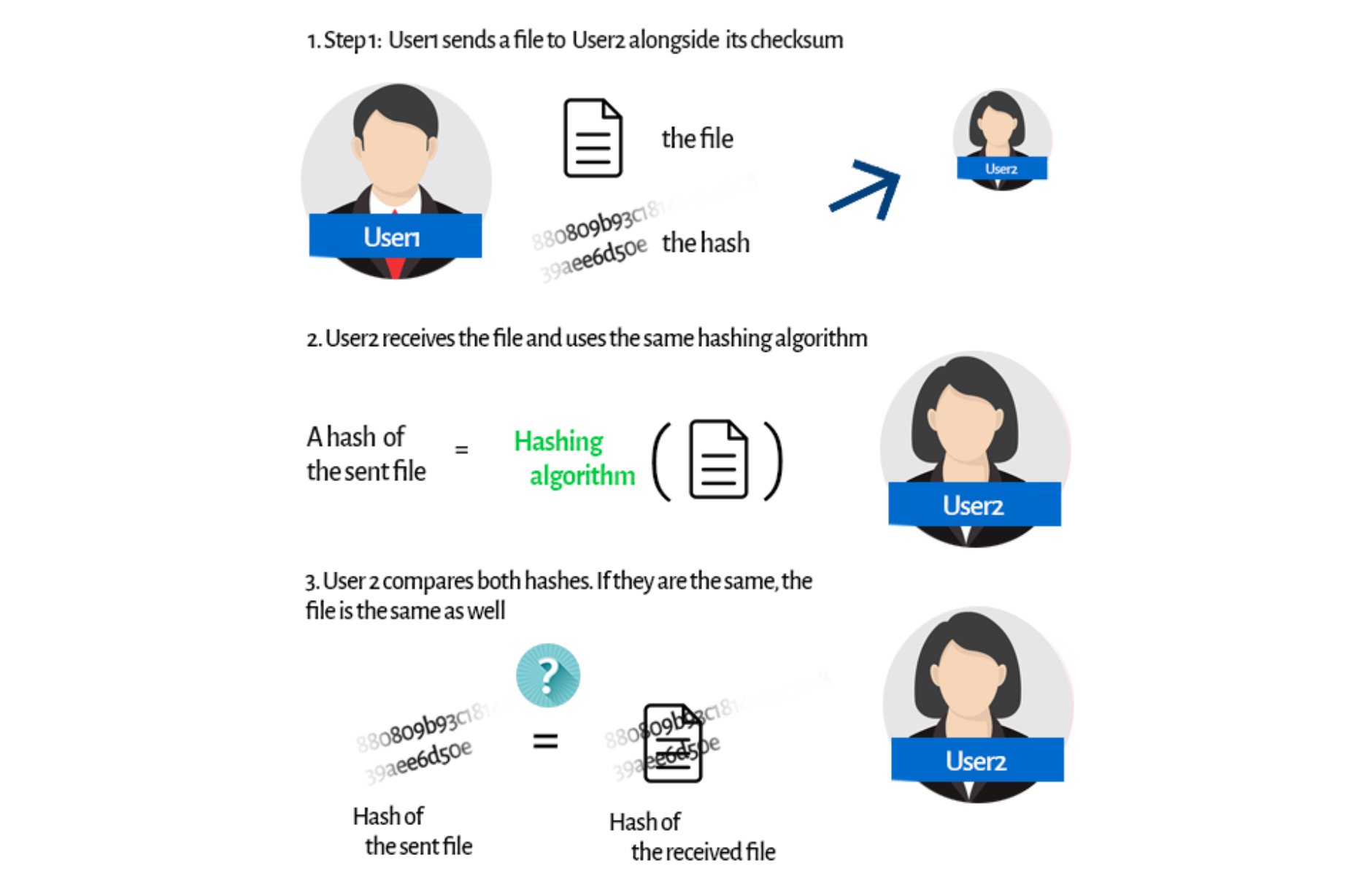
Hashing Algorithms Overview From Definitions To Usages Hashing is essential for ensuring data integrity and security. whether securing passwords, verifying file integrity, or enabling blockchain technology, understanding and using hashing. In the world of secured communications, message integrity describes the concept of ensuring that data has not been modified in transit. this is typically accomplished with the use of a hashing algorithm. In this article, you will learn about cryptographic hashing algorithms, their significance in ensuring data integrity, and how they are applied in various domains including blockchain technology, password storage, and more. Hashing algorithms also play a vital role in digital signatures, which are used to verify the authenticity and integrity of digital documents or messages. in a digital signature scheme, the signer first computes the hash value of the document using a secure hashing algorithm. Hashing in cyber security converts data into a unique string through algorithms, ensuring data integrity and security. this article explores what is hashing in cyber security, why it’s crucial in cybersecurity, and its real world applications.

Hashing Algorithms For Integrity Validation 101 Computing In this article, you will learn about cryptographic hashing algorithms, their significance in ensuring data integrity, and how they are applied in various domains including blockchain technology, password storage, and more. Hashing algorithms also play a vital role in digital signatures, which are used to verify the authenticity and integrity of digital documents or messages. in a digital signature scheme, the signer first computes the hash value of the document using a secure hashing algorithm. Hashing in cyber security converts data into a unique string through algorithms, ensuring data integrity and security. this article explores what is hashing in cyber security, why it’s crucial in cybersecurity, and its real world applications.
Hashing Algorithms Message Digest Working Of Md5 Hashing in cyber security converts data into a unique string through algorithms, ensuring data integrity and security. this article explores what is hashing in cyber security, why it’s crucial in cybersecurity, and its real world applications.
Comments are closed.