Hashing Algorithms

Hashing Pdf Algorithms And Data Structures Algorithms Hashing refers to the process of generating a small sized output (that can be used as index in a table) from an input of typically large and variable size. hashing uses mathematical formulas known as hash functions to do the transformation. A hashing algorithm is a mathematical function that garbles data and makes it unreadable. hashing algorithms are one way programs, so the text can’t be unscrambled and decoded by anyone else.

6 Hashing Pdf Algorithms And Data Structures Computer Science Hashing is the process of converting data — text, numbers, files, or anything, really — into a fixed length string of letters and numbers. data is converted into these fixed length strings, or hash values, by using a special algorithm called a hash function. Hashing is widely used in algorithms, data structures, and cryptography. in this tutorial, we’ll discuss hashing and its application areas in detail. first, we’ll discuss the core concepts and principles of hashing. second, we’ll analyze cryptographic hash functions. then, we’ll define a few hashing algorithms and possible attacks on them. In the last two chapters we studied many tail bounds, including those from markov, chebyshev, chernofand hoefding. we also studied a tail approx imation based on the central limit theorem (clt). in this chapter we will apply these bounds and approximations to an important problem in computer science: the design of hashing algorithms. Hashing allows for faster search and dynamic operations on data structures, arrays, and sorted arrays. this lecture discusses comparison models, decision trees, and hash functions. instructor: jason ku. freely sharing knowledge with learners and educators around the world. learn more.

08 Hashing Pdf Algorithms And Data Structures Computer Programming In the last two chapters we studied many tail bounds, including those from markov, chebyshev, chernofand hoefding. we also studied a tail approx imation based on the central limit theorem (clt). in this chapter we will apply these bounds and approximations to an important problem in computer science: the design of hashing algorithms. Hashing allows for faster search and dynamic operations on data structures, arrays, and sorted arrays. this lecture discusses comparison models, decision trees, and hash functions. instructor: jason ku. freely sharing knowledge with learners and educators around the world. learn more. Hashing is a data structure, where we can store the data and look up that data very quickly. hashing uses a special formula called a hash function to map data to a location in the data structure. the hash function takes the data as input and returns an index in the data structure where the data should be stored. this allows us to quickly retrieve the data by using the hash function to. Now that we have a basic idea of what a hash function is in cryptography, let's break down the internal mechanics. the first act of the hashing algorithm is to divide the large input data into blocks of equal size. further, the algorithm applies the hashing process to the data blocks one by one. Hashing is the practice of transforming a given key or string of characters into another value, all for the purpose of cybersecurity and safe data encryption. Hashing is one of the most fundamental concepts in cybersecurity—yet it’s often misunderstood or overlooked. in this blog post, you’ll get a clear, practical introduction to hashing algorithms and how they’re used in real world scenarios, from verifying file integrity to protecting stored passwords.
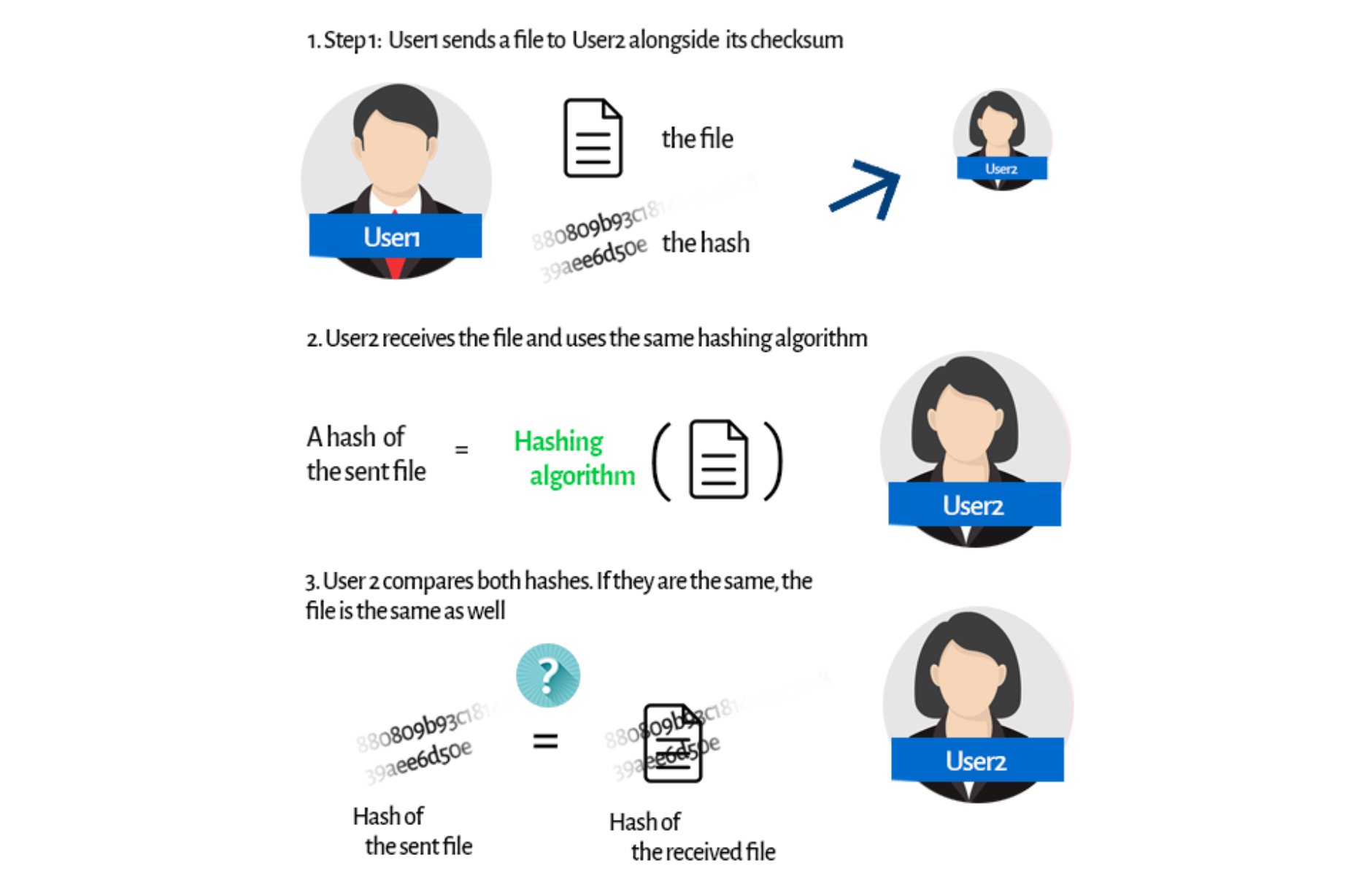
Hashing Algorithms Overview From Definitions To Usages Hashing is a data structure, where we can store the data and look up that data very quickly. hashing uses a special formula called a hash function to map data to a location in the data structure. the hash function takes the data as input and returns an index in the data structure where the data should be stored. this allows us to quickly retrieve the data by using the hash function to. Now that we have a basic idea of what a hash function is in cryptography, let's break down the internal mechanics. the first act of the hashing algorithm is to divide the large input data into blocks of equal size. further, the algorithm applies the hashing process to the data blocks one by one. Hashing is the practice of transforming a given key or string of characters into another value, all for the purpose of cybersecurity and safe data encryption. Hashing is one of the most fundamental concepts in cybersecurity—yet it’s often misunderstood or overlooked. in this blog post, you’ll get a clear, practical introduction to hashing algorithms and how they’re used in real world scenarios, from verifying file integrity to protecting stored passwords.
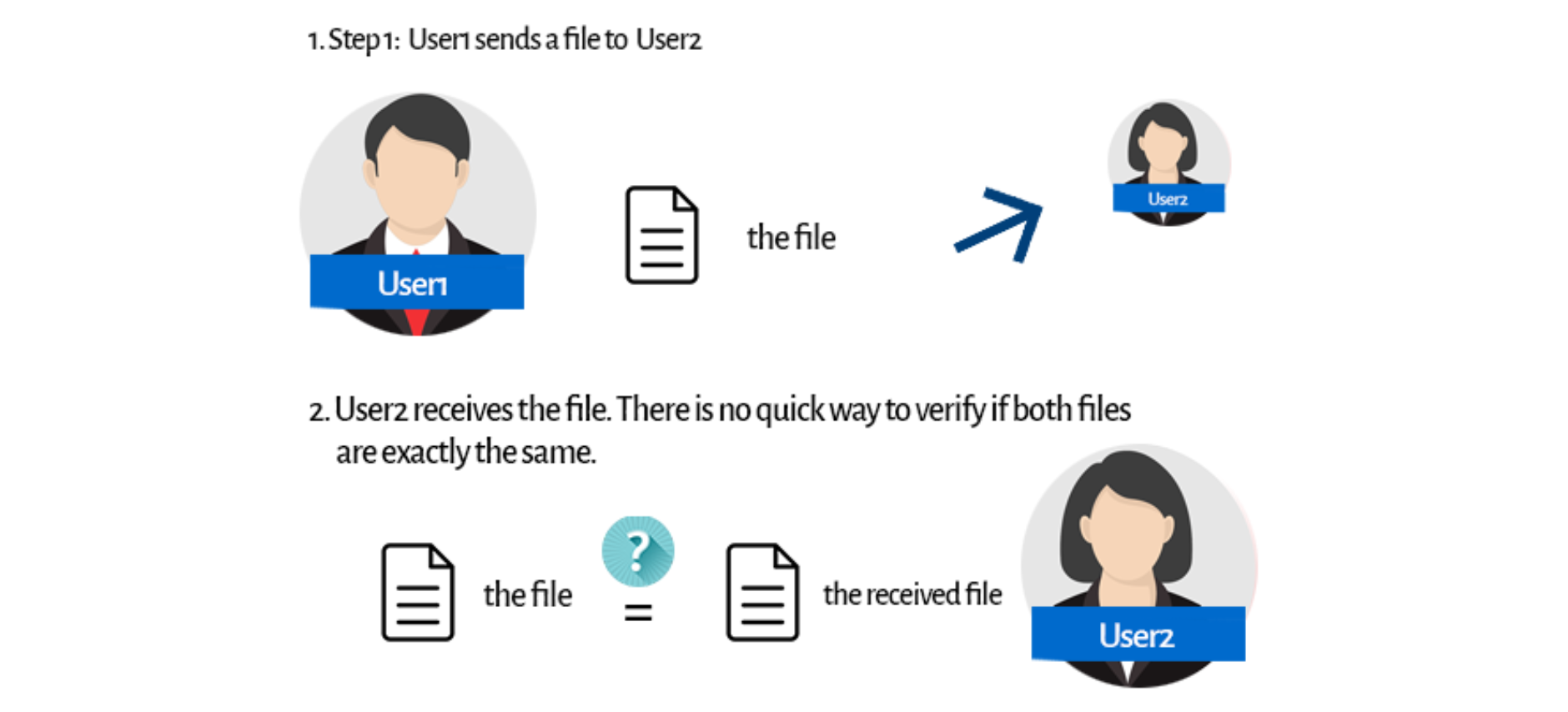
Hashing Algorithms Overview From Definitions To Usages Hashing is the practice of transforming a given key or string of characters into another value, all for the purpose of cybersecurity and safe data encryption. Hashing is one of the most fundamental concepts in cybersecurity—yet it’s often misunderstood or overlooked. in this blog post, you’ll get a clear, practical introduction to hashing algorithms and how they’re used in real world scenarios, from verifying file integrity to protecting stored passwords.
Hashing Algorithms Message Digest Working Of Md5
Comments are closed.