Hacking Status 3

Pin On Hacking Status Radware’s live threat map presents near real time information about cyberattacks as they occur, based on our global threat deception network and cloud systems event information. Penetration tester ⚡😈 | hacker attitude status | hacking status | hacker status | hacking status more.
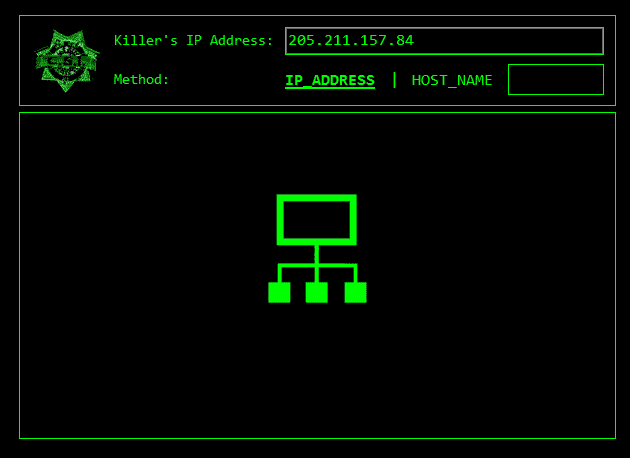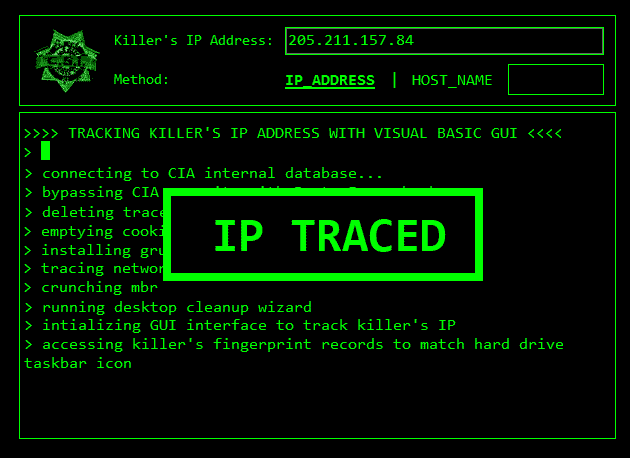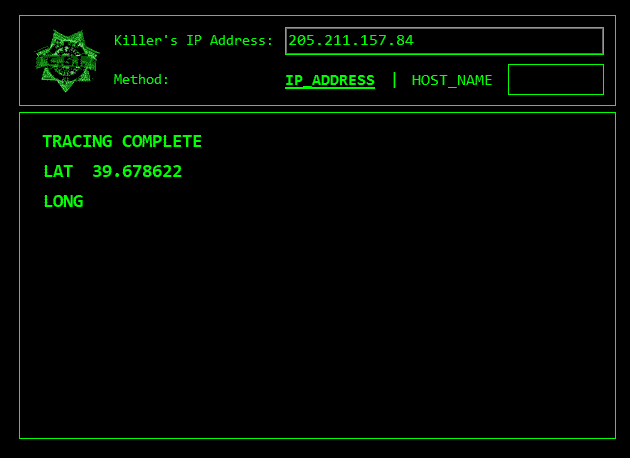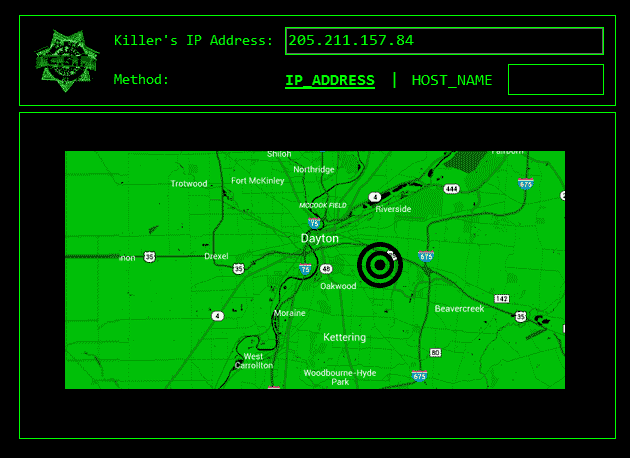
5 Phases Of Hacking Thanks to the cyber attack map by httpcs, discover the latest cyber attacks & cyber threats in real time vulnerabilities malware phishing hacked data malicious website. This repository is primarily maintained by omar santos (@santosomar) and includes thousands of resources related to ethical hacking, bug bounties, digital forensics and incident response (dfir), artificial intelligence security, vulnerability research, exploit development, reverse engineering, and more. h4cker cheat sheets hping3 cheatsheet. While this status code does not carry much information by itself, it signals to attackers that their attempt—whether automated or manual—was successful. in essence, it tells attackers that they have found a way to legitimately receive responses from the server. These are all signs of hacking. take immediate action, change passwords on other services, try to recover the account through official channels, and report the incident to support teams.

Hacking Described Source Https Twitter 4ever Waiting Status While this status code does not carry much information by itself, it signals to attackers that their attempt—whether automated or manual—was successful. in essence, it tells attackers that they have found a way to legitimately receive responses from the server. These are all signs of hacking. take immediate action, change passwords on other services, try to recover the account through official channels, and report the incident to support teams. Problem is, most of them appear to be scripts that scan, and i am still technically returning a http status code of 200 with the small message. i want to be more forward with the status code, but i am not sure which one best applies. Hacksite network service status uptime statusuptime aug 13 aug 14 aug 15 aug 16 aug 17 aug 18 aug 19 powered by hetrixtools uptime monitor. Uncover the secrets behind the 'hack status' phenomenon. learn how to protect your digital identity and stay secure online. this article explores the latest threats, offers expert tips, and provides essential insights to keep your data safe from potential hacks. Blue or guarded indicates a general risk of increased hacking, virus, or other malicious activity. the potential exists for malicious cyber activities, but no known exploits have been identified, or known exploits have been identified but no significant impact has occurred.

Hacking In Progress Problem is, most of them appear to be scripts that scan, and i am still technically returning a http status code of 200 with the small message. i want to be more forward with the status code, but i am not sure which one best applies. Hacksite network service status uptime statusuptime aug 13 aug 14 aug 15 aug 16 aug 17 aug 18 aug 19 powered by hetrixtools uptime monitor. Uncover the secrets behind the 'hack status' phenomenon. learn how to protect your digital identity and stay secure online. this article explores the latest threats, offers expert tips, and provides essential insights to keep your data safe from potential hacks. Blue or guarded indicates a general risk of increased hacking, virus, or other malicious activity. the potential exists for malicious cyber activities, but no known exploits have been identified, or known exploits have been identified but no significant impact has occurred.

Premium Photo Attacked Hacked System System Hacking Concept Hacked Uncover the secrets behind the 'hack status' phenomenon. learn how to protect your digital identity and stay secure online. this article explores the latest threats, offers expert tips, and provides essential insights to keep your data safe from potential hacks. Blue or guarded indicates a general risk of increased hacking, virus, or other malicious activity. the potential exists for malicious cyber activities, but no known exploits have been identified, or known exploits have been identified but no significant impact has occurred.
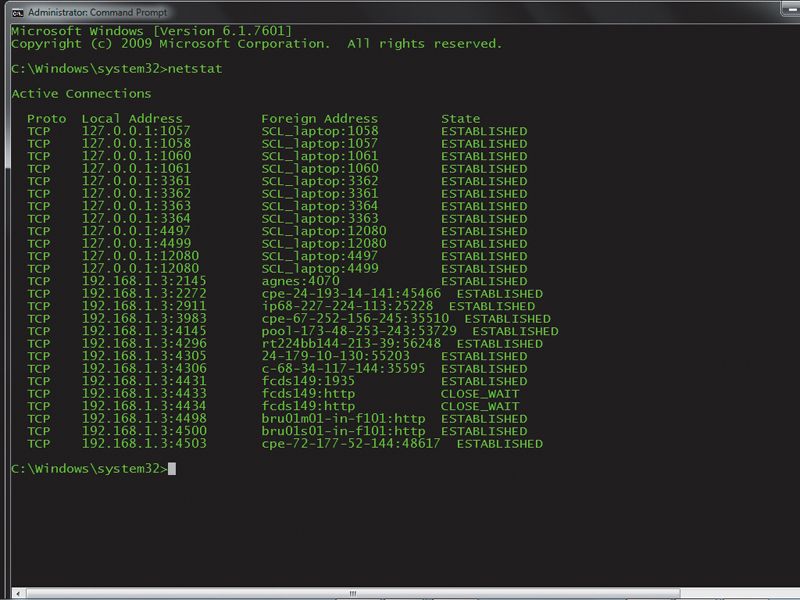
How To Recover From A Hacking Attack Techradar
Comments are closed.