Hackerone Report Explained Stored Xss Via Image Payload %f0%9f%93%81 Real Bug Bounty Poc

Xss Loader Xss Scanner And Payload Generator Geeksforgeeks 🚨 new hackerone bug bounty report breakdown!in this video, we walk through a real world stored xss vulnerability via an image payload in a messaging featur. Summary : stored attacks are those where the injected script is permanently stored on the target servers, such as in a database, in a message forum, visitor log, comment field, etc. the victim then retrieves the malicious script from the server when it requests the stored information.

Xss Loader Xss Scanner And Payload Generator Geeksforgeeks Today i will tell you how to exploit cookie based xss vulnerabilities, and also give an example from one company testing, from which i received $7,300 in general for the research. This hackerone report describes a security vulnerability in gitlab that allows an attacker to exploit a stored cross site scripting (xss) vulnerability. Late last year on hackerone during an lhe (this is only important later due to an extreme time crunch), i found an extremely challenging vulnerability on a major brand's web site involving several layers of exploitation ultimately resulting in a stored xss payload that was able to take over a victim's account simply by visiting a specific. All reports' raw info stored in data.csv. scripts to update this file are written in python 3 and require chromedriver and chromium executables at path. every script contains some info about how it works.
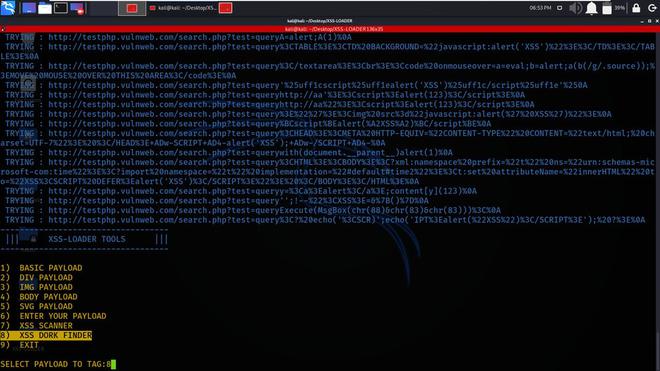
Xss Loader Xss Scanner And Payload Generator Geeksforgeeks Late last year on hackerone during an lhe (this is only important later due to an extreme time crunch), i found an extremely challenging vulnerability on a major brand's web site involving several layers of exploitation ultimately resulting in a stored xss payload that was able to take over a victim's account simply by visiting a specific. All reports' raw info stored in data.csv. scripts to update this file are written in python 3 and require chromedriver and chromium executables at path. every script contains some info about how it works. This lists the top xss vulnerability reports submitted to hackerone between 2000 and 2022. the top reports include stored and reflected xss issues in websites and platforms like paypal, github, reddit, twitter and more. successful reports were rewarded between $0 to $20,000. ## summary it has been identified that a known and previously reported stored xss vulnerability is still possible to be exploited and abused in the recent version of acronis cyber protect (*15.0.31791*), released last march 7, 2023, (*evidence attached*). In this video, we walk through a real hackerone xss report, clone the vulnerable repository, and show how to exploit the reflected xss vulnerability through unsanitized headers .more. Security researcher nguyenlv7 discovered a dom based xss vulnerability on hackerone’s careers page, leading to a $500 bounty reward. the issue resided in the way the page handled ? lever parameters in the url and dynamically appended them into the dom without proper sanitization.
Comments are closed.