Google Hack Database Find Sensitive Data Google

Google Hacking Database Ghdb Google Dorks Osint Recon Pdf The ShinyHunters cybercriminal group breached Google's Salesforce system through vishing attacks, stealing business contact details and customer data Tech Major data hack nabs 184M passwords for Google, Apple and more: ‘Cybercriminal’s dream’ By Brooke Steinberg Published May 28, 2025, 2:17 pm ET

Google Hacking Database Ghdb Google Dorks Osint Recon2 Download In a blog post late on Tuesday, Google Threat Intelligence Group said one of its Salesforce database systems, used to store contact information and related notes for small and medium-sized 16 billion Google, Apple and other passwords leaked in record data breach: What you need to know "This is not just a leak - it's a blueprint for mass exploitation," researchers declared© Sergey Google (NASDAQ: GOOGL) (NASDAQ: GOOG) has confirmed a data breach that has affected some of its customers The breach was attributed to a hacking group known as ShinyHunters, also referred to as Plus: Instagram sparks a privacy backlash over its new map feature, hackers steal data from Google's customer support system, and the true scope of the Columbia University hack comes into focus

Google Hacking Database Ghdb Google Dorks Osint Recon11 Pdf Google (NASDAQ: GOOGL) (NASDAQ: GOOG) has confirmed a data breach that has affected some of its customers The breach was attributed to a hacking group known as ShinyHunters, also referred to as Plus: Instagram sparks a privacy backlash over its new map feature, hackers steal data from Google's customer support system, and the true scope of the Columbia University hack comes into focus If you lose your Android phone and are worried about leaking your sensitive data, you can use Google’s Find Hub service to remotely lock it down or factory reset it A factory reset is the most The HR tech giant said it had no indication of any unauthorized access to customer systems, but has not ruled out a breach affecting customers' personal information The database containing the compromised passwords was ironically unencrypted and not password-protected itself, a report said
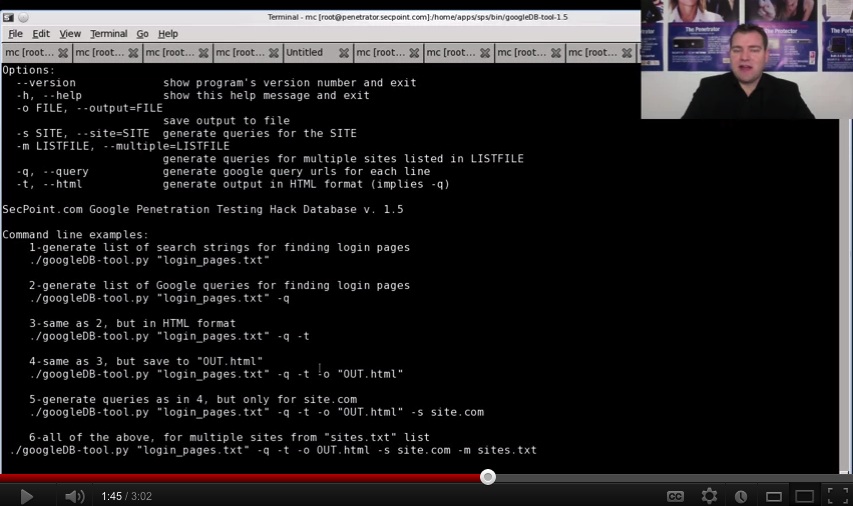
Google Hack Database Find Sensitive Data Google If you lose your Android phone and are worried about leaking your sensitive data, you can use Google’s Find Hub service to remotely lock it down or factory reset it A factory reset is the most The HR tech giant said it had no indication of any unauthorized access to customer systems, but has not ruled out a breach affecting customers' personal information The database containing the compromised passwords was ironically unencrypted and not password-protected itself, a report said
Comments are closed.