Github And Gitlab Cdns Abused To Spread Malware Gridinsoft Blog

Github And Gitlab Cdns Abused To Spread Malware Gridinsoft Blog Recent research around new spreading approaches of one stealer malware family revealed a new way to abuse github. instead of creating repositories that contain malware files, hackers push the files they need through the issue reporting mechanism in the repository menu. On saturday, bleepingcomputer reported how threat actors have been abusing github comments to push malware while making it seem like the malicious files were hosted on official source code.
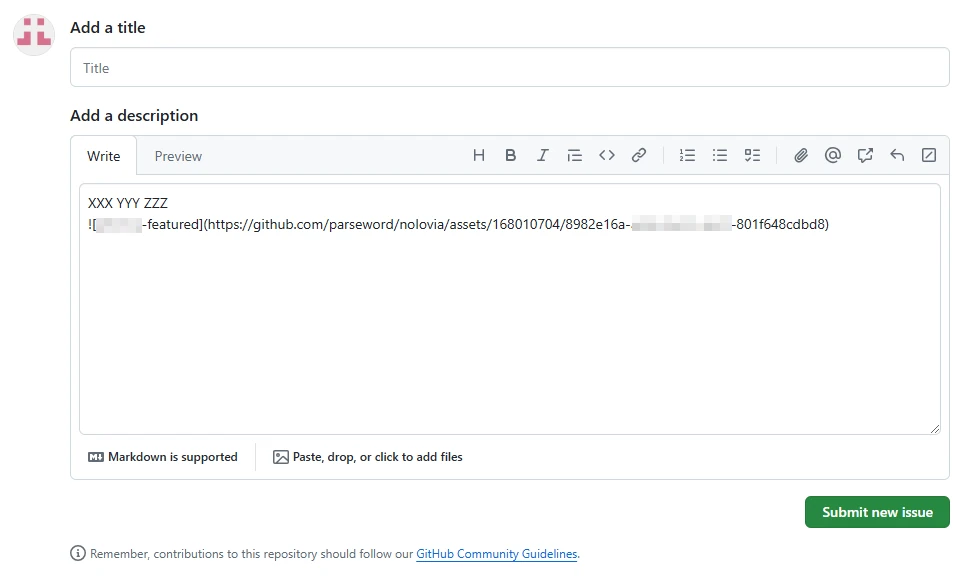
Github And Gitlab Cdns Abused To Spread Malware Gridinsoft Blog A github content delivery network (cdn) flaw abused by hackers to host and distribute malware could be exploited similarly on gitlab. the vulnerability weaponizes urls associated with microsoft repositories to obfuscate malicious content and make it appear safe. Hackers have recently exploited a vulnerability in github and gitlab, allowing them to upload malware disguised as legitimate repositories through phishing links generated from unpublished comments on open source projects. Hackers are using unpublished github and gitlab comments to generate phishing links that appear to come from legitimate open source software (oss) projects. Hackers abuse git cdns to spread malware, leveraging features in github and gitlab, enabling them to craft phishing urls and evade detection.

Thousands Of Github Repositories Spread Malware That Is Disguised As Hackers are using unpublished github and gitlab comments to generate phishing links that appear to come from legitimate open source software (oss) projects. Hackers abuse git cdns to spread malware, leveraging features in github and gitlab, enabling them to craft phishing urls and evade detection. This exploit enables attackers to upload files, including malware, to gitlab’s cdn under urls resembling official project repositories. the links remain live even if the associated comment is never posted or is deleted, making them a potential tool for deception. Threat actors are exploiting a github and gitlab flaw to distribute malware via urls associated with legitimate repositories, creating convincing lures. this issue also affects gitlab, allowing malware to be pushed via comments. In a recent discovery, github was found susceptible to a cdn (content delivery network) flaw that allows attackers to host malware. this appears to be a security issue or a bug that exposes the risks associated with cdns used by major software development platforms. Uma pesquisa recente sobre novas abordagens de disseminação de uma família de malware ladrão revelou uma nova maneira de abusar do github. instead of creating repositories that contain malware files, hackers push the files they need through the issue reporting mechanism in the repository menu.
Comments are closed.